300-720 Cisco Securing Email with Cisco Email Security Appliance (300-720 SESA) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-720 Securing Email with Cisco Email Security Appliance (300-720 SESA) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An administrator is managing multiple Cisco ESA devices and wants to view the quarantine emails from all devices in a central location.
How is this accomplished?
A content dictionary was created for use with Forged Email Detection. Proper data that pertains to the CEO Example CEO:
What are two phases of the Cisco ESA email pipeline? (Choose two.)
Email encryption is configured on a Cisco ESA that uses CRES.
Which action is taken on a message when CRES is unavailable?
A company has recently updated their security policy and now wants to drop all email messages larger than 100 MB coming from external sources. The Cisco Secure Email Gateway is LDAP integrated and all employee accounts are in the group "Employees". Which filter rule configuration provides the desired outcome?
When the spam quarantine is configured on the Cisco Secure Email Gateway, which type of query is used to validate non administrative user access to the end-user quarantine via LDAP?
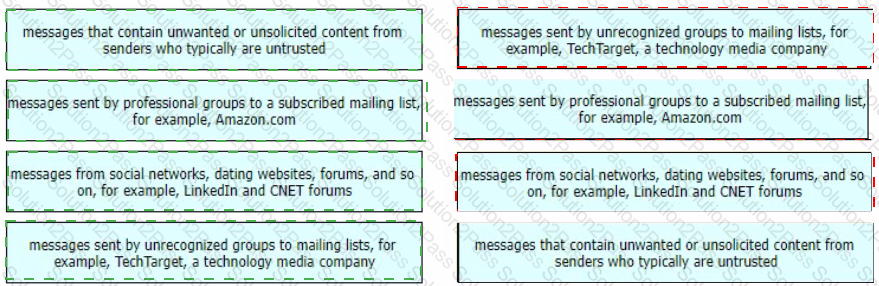
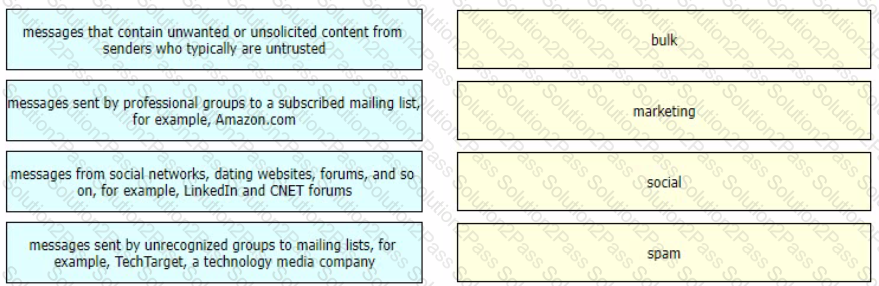
Which two components form the graymail management solution in Cisco ESA? (Choose two.)
An organization wants to prevent proprietary patent documents from being shared externally via email. The network administrator reviewed the DLP policies on the Cisco Secure Email Gateway and could not find an existing policy with the appropriate matching patterns. Which type of DLP policy template must be used to create a policy that meets this requirement?
Refer to the exhibit.
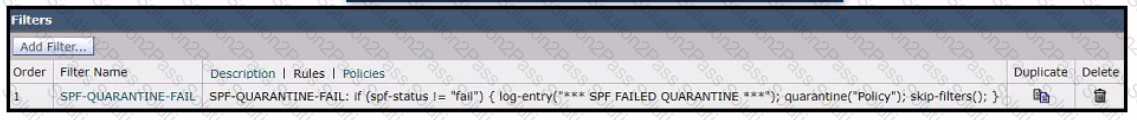
A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
What are the two different phases in the process of Cisco Secure Email Gateway performing S/MIME encryption? (Choose two.)
Drag and drop the graymail descriptions from the left onto the verdict categories they belong to on the right.
An organization has a strict policy on URLs embedded in emails. The policy allows visibility into what the URL is but does not allow the user to click it. Which action must be taken to meet the requirements of the security policy?
Which feature utilizes sensor information obtained from Talos intelligence to filter email servers connecting into the Cisco ESA?
A company has deployed a new mandate that requires all emails sent externally from the Sales Department to be scanned by DLP for PCI-DSS compliance. A new DLP policy has been created on the Cisco ESA and needs to be assigned to a mail policy named ‘Sales’ that has yet to be created.
Which mail policy should be created to accomplish this task?
An email containing a URL passes through the Cisco ESA that has content filtering disabled for all mail policies. The sender is sampleuser@test1.com, the recipients are testuser1@test2.com, testuser2@test2.com, testuser3@test2.com, and mailer1@test2.com. The subject of the email is Test Document395898847. An administrator wants to add a policy to ensure that the Cisco ESA evaluates the web reputation score before permitting this email.
Which two criteria must be used by the administrator to achieve this? (Choose two.)
An organization wants to use DMARC to improve its brand reputation by leveraging DNS records.
Which two email authentication mechanisms are utilized during this process? (Choose two.)
What is the default method of remotely accessing a newly deployed Cisco Secure Email Virtual Gateway when a DHCP server is not available?
What are two primary components of content filters? (Choose two.)
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
What must be configured to allow the Cisco ESA to encrypt an email using the Cisco Registered Envelope Service?