300-720 Cisco Securing Email with Cisco Email Security Appliance (300-720 SESA) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 300-720 Securing Email with Cisco Email Security Appliance (300-720 SESA) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which restriction is in place for end users accessing the spam quarantine on Cisco Secure Email Gateway appliances?
Refer to the exhibit.
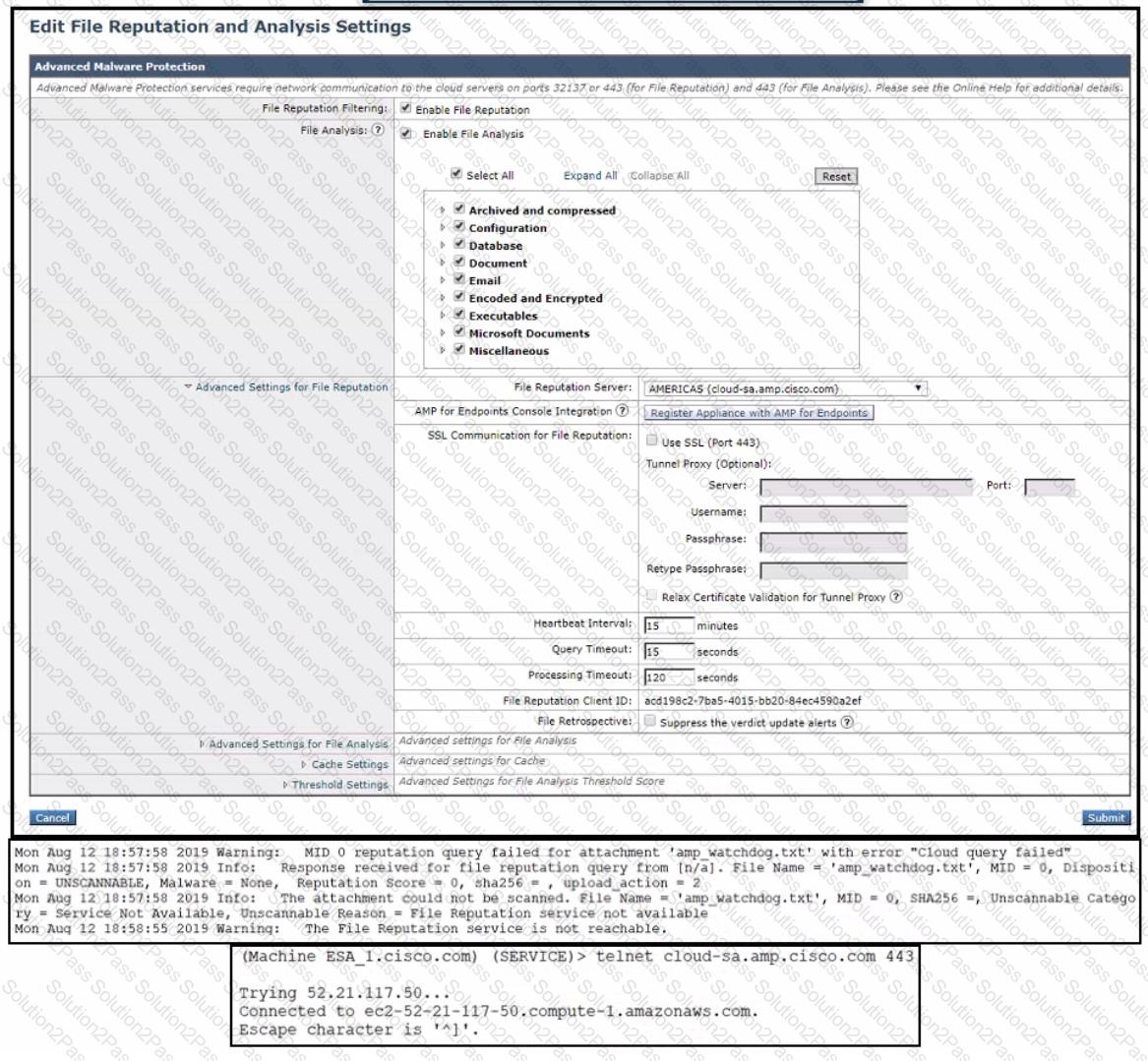
An administrator has configured File Reputation and File Analysis on the Cisco Secure Email Gateway appliance however it does not function as expected What must be configured on the appliance for this to function?
A Cisco ESA administrator was notified that a user was not receiving emails from a specific domain. After reviewing the mail logs, the sender had a negative sender-based reputation score.
What should the administrator do to allow inbound email from that specific domain?
Which two actions are configured on the Cisco ESA to query LDAP servers? (Choose two.)
Refer to the exhibit.
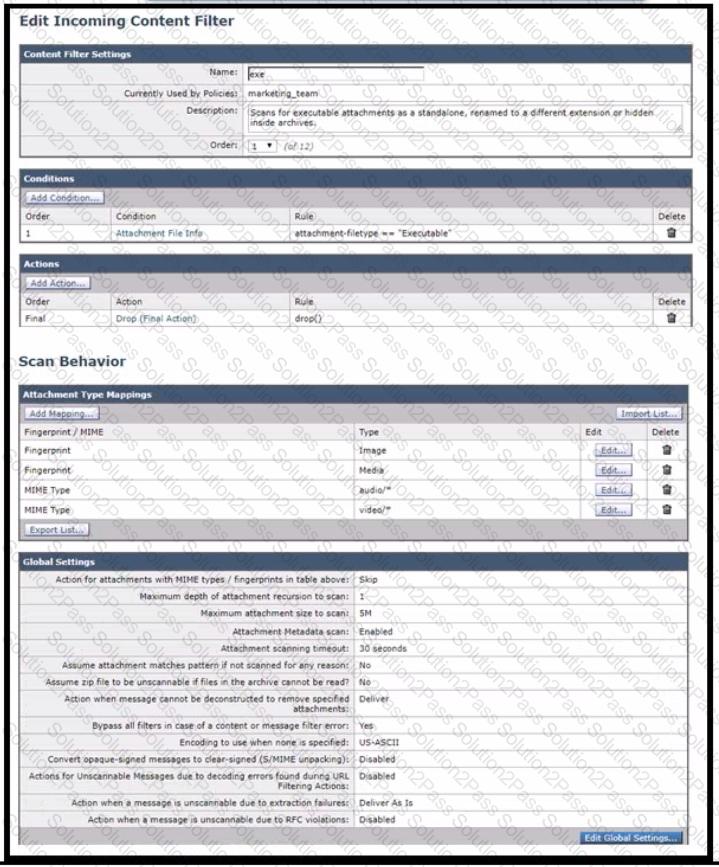
Which configuration allows the Cisco Secure Email Gateway to scan for executables inside the archive file and apply the action as per the content filter?
Which two statements about configuring message filters within the Cisco ESA are true? (Choose two.)
An administrator identifies that, over the past week, the Cisco ESA is receiving many emails from certain senders and domains which are being consistently quarantined. The administrator wants to ensure that these senders and domain are unable to send anymore emails.
Which feature on Cisco ESA should be used to achieve this?
A Cisco Secure Email Gateway appliance is processing many messages that are sent to invalid recipients verification. Which two steps are required to accomplish this task? (Choose two.)
Which two components must be configured to perform DLP scanning? (Choose two.)
An engineer is configuring a Cisco ESA for the first time and needs to ensure that any email traffic coming from the internal SMTP servers is relayed out through the Cisco ESA and is tied to the Outgoing Mail Policies.
Which Mail Flow Policy setting should be modified to accomplish this goal?
An administrator has created a content filter to quarantine all messages that result in an SPF hardfail to review the messages and determine whether a trusted partner has accidentally misconfigured the DNS settings. The administrator sets the policy quarantine to release the messages after 24 hours, allowing time to review while not interrupting business.
Which additional option should be used to help the end users be aware of the elevated risk of interacting with these messages?
Which attack is mitigated by using Bounce Verification?
What is the maximum message size that can be configured for encryption on the Cisco ESA?
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
An engineer is tasked with creating a content filter to catch attachments, including credit card numbers, and hold them for review until further action is taken. Which component on a Cisco Secure Email Gateway must be configured to meet this requirement?
Which Cisco ESA security service is configured only through an outgoing mail policy?
A security administrator deployed a Cisco Secure Email Gateway appliance with a mail policy configured to store suspected spam for review. The appliance is the DMZ and only the standard HTTP/HTTPS ports are allowed by the firewall. An administrator wants to ensure that users can view any suspected spam that was blocked. Which action must be taken to meet this requirement?
Which setting affects the aggressiveness of spam detection?
A Cisco Secure Email Gateway administrator must provide outbound email authenticity and configures a DKIM signing profile to handle this task. What is the next step to allow this organization to use DKIM for their outbound email?
Which two are configured in the DMARC verification profile? (Choose two.)
