350-501 Cisco Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-501 Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two routing protocols support Cisco MPLS TE tunnels? (Choose two.)
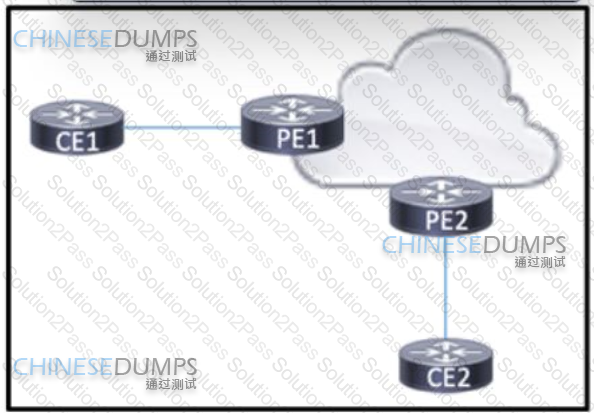
Refer to the exhibit BGP is running in the core of the service provider to exchange routes for its customers, and OSPF serves as the PE-CE routing protocol. The service provider s existing customer at CE1 is opening a new office in a different geographical location connected via CE2. A network engineer must update the BGP implementation so that PE1 and PE2 will share routes and provide communication between CE1 and CE2 Which action must the engineer take?
Which action occurs during the traceback phase of the six-phase approach to service provider security?
Refer to the exhibit.
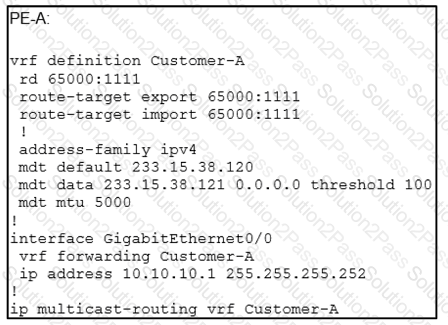
An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?
Refer to the exhibit:
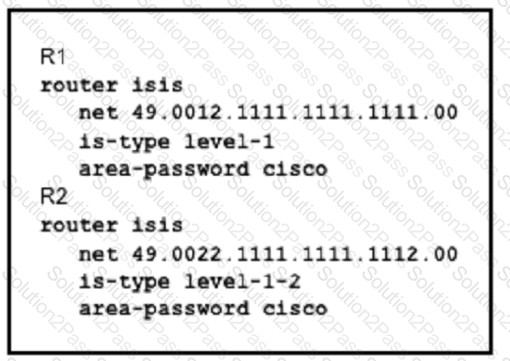
What is the effect of this configuration?
Refer to the exhibit.
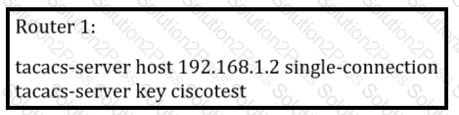
What is the result of this configuration?
What are the two uses of the YANG data modeling language? (Choose two.)
An engineer is developing a configuration script to enable dial-out telemetry streams using gRPC on several new devices. TLS must be disabled on the devices. Which configuration must the engineer apply on the network?
A)
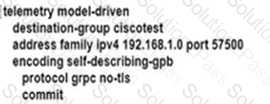
B)
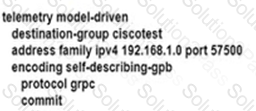
C)

D)

Refer to the exhibit:
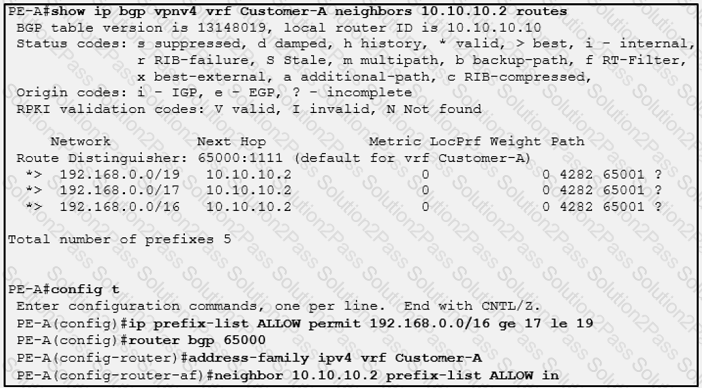
Which three outcomes occur if the prefix list is added to the neighbor? (Choose three)
How can shared services in an MPLS Layer 3 VPN provide Internet access to the customers of a central service provider?
Refer to the exhibit:
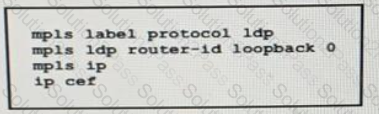
A network operator working for service provider with an employee id 3715 15:021 applied this configuration to a router.
Which additional step should the engineer use to enable LDP?
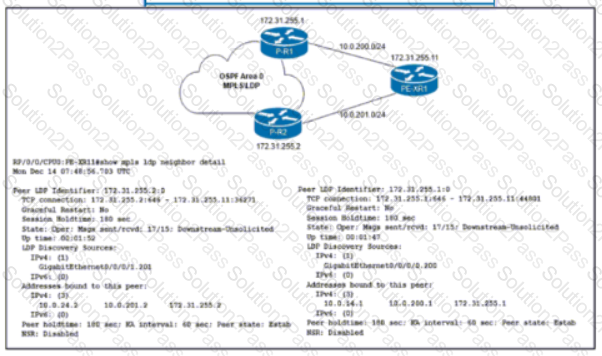
Refer to the exhibit. The network team must implement MPLS LDP session protection with two requirements:
Session protection is provided for core loopback IP addresses only.
The LDP session must remain operational for one hour when the WAN link on PE-XR1 fails.
Which configuration must the team implement on PE-XR1?
Refer to the exhibit.

A network engineer at a large ISP Is configuring telemetry streams to monitor the health status of PE routers on the network using gRPC dial-out. The PE routers are located at several data centers in different physical locations, and they are using IS-IS and BGP for routing. Which additional configuration must the engineer implement on the PE routers to meet the goal?
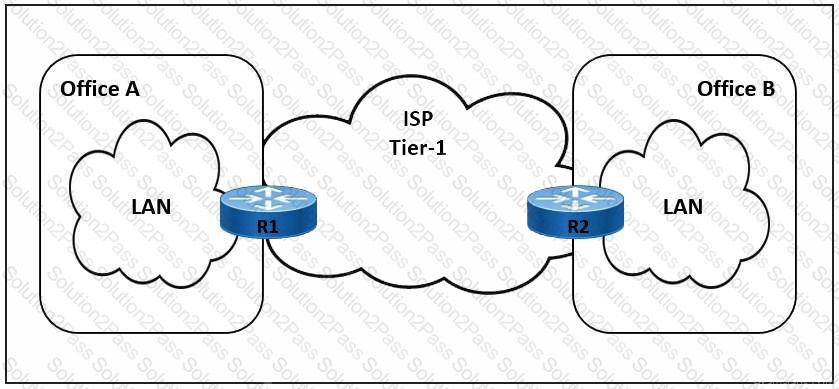
Refer to the exhibit. The link between Office A and Office B is running at 90% load, and occasionally the CPU on router R1 is overloaded. The company implemented QoS for business-critical applications at both offices as a temporary solution. A network engineer must update the R1 configuration to 600 ms to reduce CPU load and limit downtime after connection failure to avoid data loss. Which action meets this requirement?
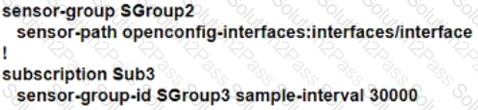 Text, letter
Description automatically generated
Text, letter
Description automatically generated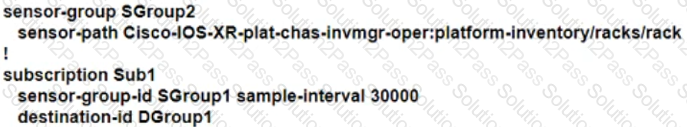 Text
Description automatically generated
Text
Description automatically generated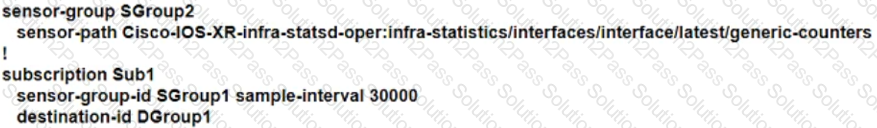 Graphical user interface, text
Description automatically generated
Graphical user interface, text
Description automatically generated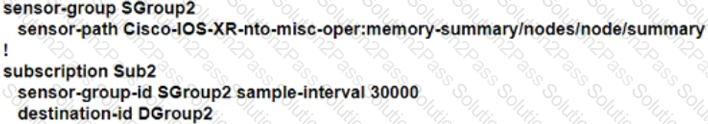 Text, letter
Description automatically generated
Text, letter
Description automatically generated