350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer needs to add protection for data in transit and have headers in the email message Which configuration is needed to accomplish this goal?
Which solution allows an administrator to provision, monitor, and secure mobile devices on Windows and Mac computers from a centralized dashboard?
Which compliance status is shown when a configured posture policy requirement is not met?
When using Cisco AMP for Networks which feature copies a file to the Cisco AMP cloud for analysis?
Which function is included when Cisco AMP is added to web security?
Which metric is used by the monitoring agent to collect and output packet loss and jitter information?
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
What is an advantage of the Cisco Umbrella roaming client?
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform?
A networking team must harden an organization's network from VLAN hopping attacks. The team disables Dynamic Trunking Protocol and puts any unused ports in an unused VLAN. A trunk port is used as a trunk link. What must the team configure next to harden the network against VLAN hopping attacks?
What are two rootkit types? (Choose two)
What are the components of endpoint protection against social engineering attacks?
An organization plans to upgrade its current email security solutions, and an engineer must deploy Cisco Secure Email. The requirements for the upgrade are:
Implement Data Loss Prevention
Implement mail encryption
Integrate with an existing Cisco IronPort Secure Email Gateway solution
Which Cisco Secure Email license is needed to accomplish this task?
Which VPN technology supports a multivendor environment and secure traffic between sites?
What is the term for the concept of limiting communication between applications or containers on the same node?
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
What is a difference between an XSS attack and an SQL injection attack?
What are two workload security models? (Choose two.)
A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants lo limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging?
A web hosting company must upgrade its older, unsupported on-premises servers. The company wants a cloud solution in which the cloud provider is responsible for:
Server patching
Application maintenance
Data center security
Disaster recovery
Which type of cloud meets the requirements?
In which two ways does Easy Connect help control network access when used with Cisco TrustSec? (Choose two)
Which Cisco DNA Center RESTful PNP API adds and claims a device into a workflow?
When planning a VPN deployment, for which reason does an engineer opt for an active/active FlexVPN
configuration as opposed to DMVPN?

Refer to the exhibit. An engineer must configure a new Cisco ISE backend server as a RADIUS server to provide AAA for all access requests from the client to the ISE-Frontend server.
Which Cisco ISE configuration must be used?
Which ESA implementation method segregates inbound and outbound email?
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer data?
Refer to the exhibit.
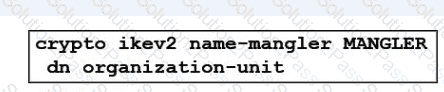
An engineer is implementing a certificate based VPN. What is the result of the existing configuration?
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability
would help an attacker brute force their way into the systems?
What is a benefit of flexible NetFlow records?
What is provided by the Secure Hash Algorithm in a VPN?
