350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
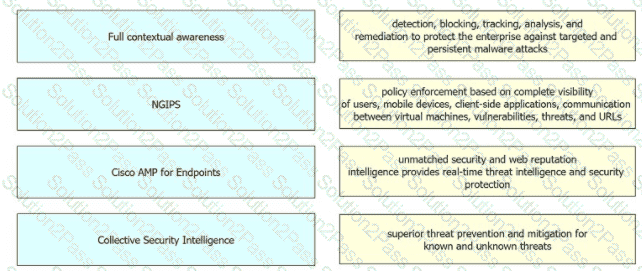
Drag and drop the security solutions from the left onto the benefits they provide on the right.
An engineer must configure Cisco AMP for Endpoints so that it contains a list of files that should not be executed by users. These files must not be quarantined. Which action meets this configuration requirement?
What is a difference between GRE over IPsec and IPsec with crypto map?
What is a characteristic of Firepower NGIPS inline deployment mode?
An administrator is adding a new Cisco ISE node to an existing deployment. What must be done to ensure that the addition of the node will be successful when inputting the FQDN?
While using Cisco Secure Firewall's Security Intelligence policies, which two criteria is blocking based upon? (Choose two.)
Refer to the exhibit.
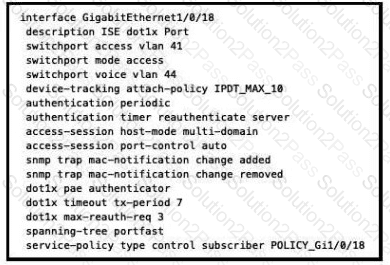
What will occur when this device tries to connect to the port?
Refer to the exhibit.
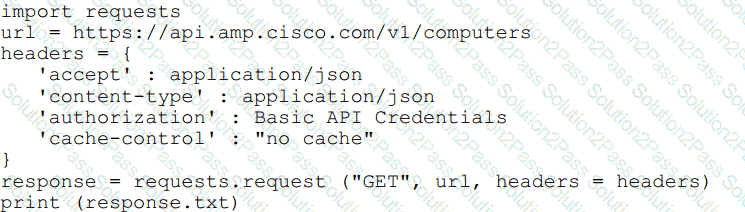
What will happen when this Python script is run?
Which two descriptions of AES encryption are true? (Choose two)
An organization has a requirement to collect full metadata information about the traffic going through their AWS cloud services They want to use this information for behavior analytics and statistics Which two actions must be taken to implement this requirement? (Choose two.)
An engineer needs to configure an access control policy rule to always send traffic for inspection without
using the default action. Which action should be configured for this rule?
Refer to the exhibit.
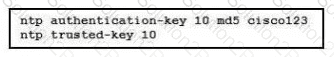
A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced What is the cause of this issue?
An engineer is configuring cloud logging using a company-managed Amazon S3 bucket for Cisco Umbrella logs. What benefit does this configuration provide for accessing log data?
What is the most common type of data exfiltration that organizations currently experience?
Which Cisco security solution integrates with cloud applications like Dropbox and Office 365 while protecting data from being exfiltrated?
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
An engineer is configuring Cisco WSA and needs to deploy it in transparent mode. Which configuration component must be used to accomplish this goal?
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two)
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
Which two deployment modes does the Cisco ASA FirePower module support? (Choose two)
Which command is used to log all events to a destination colector 209.165.201.107?
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively u: of the default policy elements. What else must be done to accomplish this task?
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat?
What are two benefits of Flexible NetFlow records? (Choose two)
What is the difference between a vulnerability and an exploit?
An MDM provides which two advantages to an organization with regards to device management? (Choose two)
Which type of encryption uses a public key and private key?
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social
engineering attacks? (Choose two)
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the
corporate network. The endpoints must have the corporate antivirus application installed and be running the
latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the
network?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)



