350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users.
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization?
What is the concept of Cl/CD pipelining?
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
A company recently discovered an attack propagating throughout their Windows network via a file named abc428565580xyz exe The malicious file was uploaded to a Simple Custom Detection list in the AMP for Endpoints Portal and the currently applied policy for the Windows clients was updated to reference the detection list Verification testing scans on known infected systems shows that AMP for Endpoints is not detecting the presence of this file as an indicator of compromise What must be performed to ensure detection of the malicious file?
Which action must be taken in the AMP for Endpoints console to detect specific MD5 signatures on endpoints and then quarantine the files?
Which technology provides the benefit of Layer 3 through Layer 7 innovative deep packet inspection,
enabling the platform to identify and output various applications within the network traffic flows?
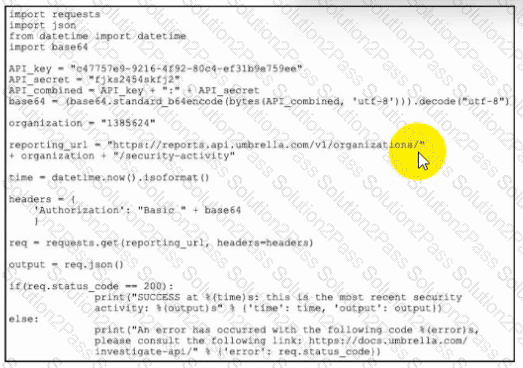
Refer to the exhibit. Which task is the Python script performing by using the Cisco Umbrella API?
What is the difference between deceptive phishing and spear phishing?
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network?
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length?
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
What are two things to consider when using PAC files with the Cisco WSA? (Choose two.)
What must be used to share data between multiple security products?
Which portion of the network do EPP solutions solely focus on and EDR solutions do not?
Which technology provides a combination of endpoint protection endpoint detection, and response?
What is a difference between weak passwords and missing encryption?
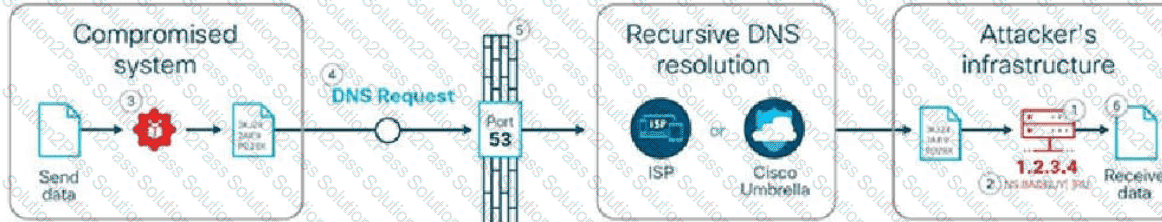
How is DNS tunneling used to exfiltrate data out of a corporate network?
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements?
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application specific activity. After enabling the AVC engine, what must be done to implement this?
Refer to the exhibit.

What is the result of this Python script of the Cisco DNA Center API?
What are two characteristics of Cisco Catalyst Center APIs? (Choose two.)
Email security has become a high-priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10.00 to -6.00) on the Cisco Secure Email Gateway. Which action will the system perform to disable any links in messages that match the filter?
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network?
An engineer is configuring Cisco Secure Endpoint to enhance security by preventing the execution of certain files by users. The engineer needs to ensure that the specific executable file name Cisco_Software_0505446151.exe is blocked from running while never being quarantined. What must the engineer configure to meet the requirement?
A Cisco ISE engineer configures Central Web Authentication (CWA) for wireless guest access and must have the guest endpoints redirect to the guest portal for authentication and authorization. While testing the policy, the engineer notices that the device is not redirected and instead gets full guest access. What must be done for the redirect to work?
An organization recently installed a Cisco Secure Web Appliance and would like to take advantage of the AVC engine to allow the organization to create a policy to control application-specific activity. After enabling the AVC engine, what must be done to implement this?
What Cisco command shows you the status of an 802.1X connection on interface gi0/1?
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?
What are two benefits of using an MDM solution? (Choose two.)