350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
What provides visibility and awareness into what is currently occurring on the network?
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system’s applications. Which
vulnerability allows the attacker to see the passwords being transmitted in clear text?
Which type of protection encrypts RSA keys when they are exported and imported?
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications?
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA?
A malicious user gained network access by spoofing printer connections that were authorized using MAB on
four different switch ports at the same time. What two catalyst switch security features will prevent further
violations? (Choose two)
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA Center?
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to
prevent the session during the initial TCP communication?
An organization wants to provide visibility and to identify active threats in its network using a VM. The
organization wants to extract metadata from network packet flow while ensuring that payloads are not retained
or transferred outside the network. Which solution meets these requirements?
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.)
Which technology enables integration between Cisco ISE and other platforms to gather and share
network and vulnerability data and SIEM and location information?
A network engineer has configured a NTP server on a Cisco ASA. The Cisco ASA has IP reachability to the
NTP server and is not filtering any traffic. The show ntp association detail command indicates that the
configured NTP server is unsynchronized and has a stratum of 16. What is the cause of this issue?
Which attack is preventable by Cisco ESA but not by the Cisco WSA?

Refer to the exhibit. Consider that any feature of DNS requests, such as the length of the domain name and the number of subdomains, can be used to construct models of expected behavior to which observed values can be compared. Which type of malicious attack are these values associated with?
A company has 5000 Windows users on its campus. Which two precautions should IT take to prevent WannaCry ransomware from spreading to all clients? (Choose two.)
Which Talos reputation center allows for tracking the reputation of IP addresses for email and web traffic?
Which Cisco Firewall solution requires zone definition?
An engineer is configuring cloud logging on Cisco ASA and needs events to compress. Which component must be configured to accomplish this goal?
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast
packets have been flooding the network. What must be configured, based on a predefined threshold, to
address this issue?
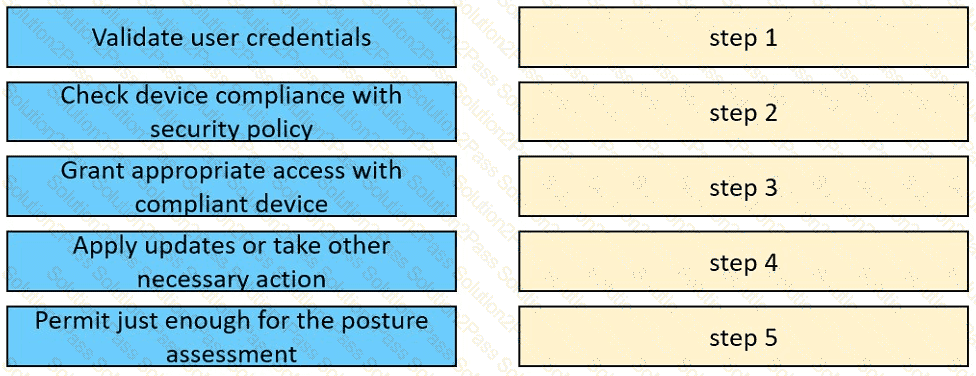
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
What are two benefits of using Cisco Duo as an MFA solution? (Choose two.)
What are two functionalities of northbound and southbound APIs within Cisco SDN architecture? (Choose two.)
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users,
data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity
platform. What should be used to meet these requirements?
What is a feature of the open platform capabilities of Cisco DNA Center?
How many interfaces per bridge group does an ASA bridge group deployment support?
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
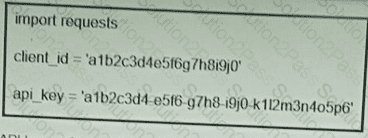
Refer to the exhibit. What function does the API key perform while working with https://api.amp.cisco.com/v1/computers?

