350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two)
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from
Cisco and other vendors to share data and interoperate with each other?
Why should organizations migrate to an MFA strategy for authentication?
Refer to the exhibit.
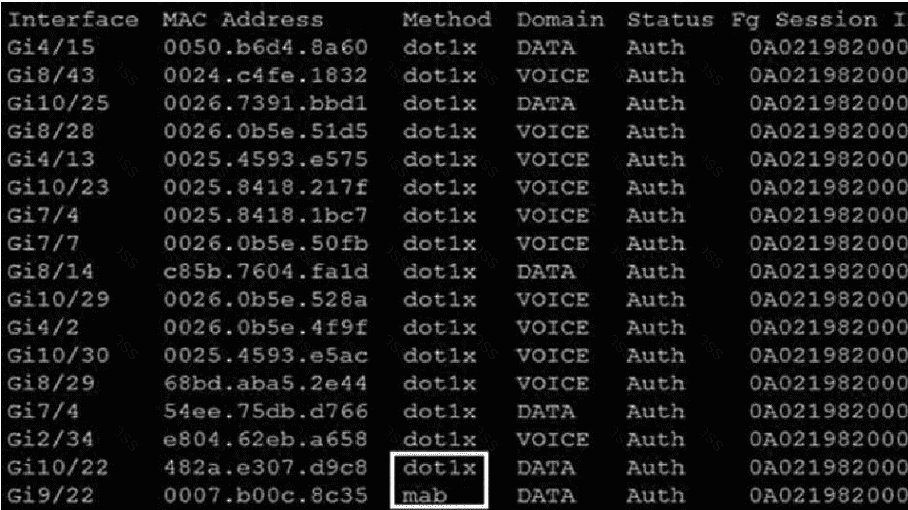
Which command was used to generate this output and to show which ports are
authenticating with dot1x or mab?
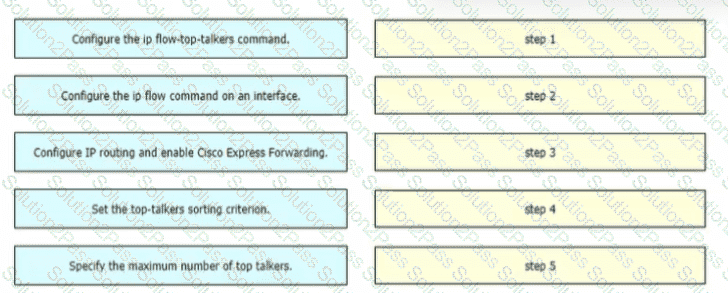
A network engineer is configuring NetFlow top talkers on a Cisco router Drag and drop the steps in the process from the left into the sequence on the right
An engineer is configuring IPsec VPN and needs an authentication protocol that is reliable and supports ACK
and sequence. Which protocol accomplishes this goal?
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline
posture node?

Refer to the exhibit. An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.)
Refer to the exhibit.
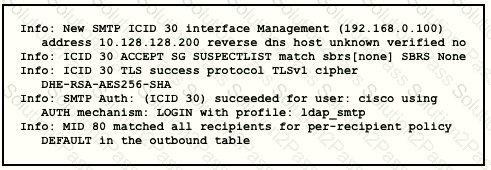
Which type of authentication is in use?
Which feature is used to restrict communication between interfaces on a Cisco ASA?
Refer to the exhibit.

How does Cisco Umbrella manage traffic that is directed toward risky domains?
Which IETF attribute is supported for the RADIUS CoA feature?
Which benefit does endpoint security provide the overall security posture of an organization?
Which two activities can be done using Cisco DNA Center? (Choose two)
Which two methods are available in Cisco Secure Web Appliance to process client requests when configured in Transparent mode? (Choose two.)
How does DNS Tunneling exfiltrate data?
Which configuration method provides the options to prevent physical and virtual endpoint devices that are in the same base EPG or uSeg from being able to communicate with each other with Vmware VDS or Microsoft vSwitch?
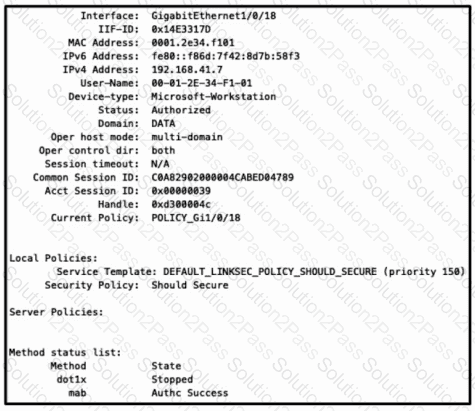
Refer to the exhibit. Which configuration item makes it possible to have the AAA session on the network?
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to
network resources?
Which parameter is required when configuring a Netflow exporter on a Cisco Router?
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized
solution. The organization does not have a local VM but does have existing Cisco ASAs that must migrate over
to Cisco FTDs. Which solution meets the needs of the organization?
An engineer is deploying Cisco Advanced Malware Protection (AMP) for Endpoints and wants to create a policy that prevents users from executing file named abc424952615.exe without quarantining that file What type of Outbreak Control list must the SHA.-256 hash value for the file be added to in order to accomplish this?
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
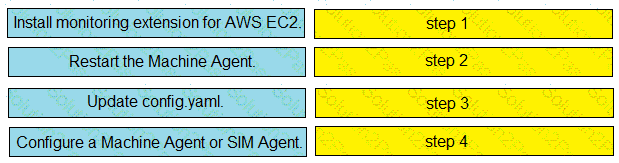
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.
Which Cisco security solution provides patch management in the cloud?
How is a cross-site scripting attack executed?
A security test performed on one of the applications shows that user input is not validated. Which security vulnerability is the application more susceptible to because of this lack of validation?
What is the difference between Cross-site Scripting and SQL Injection, attacks?
Which Cisco solution provides a comprehensive view of Internet domains. IP addresses, and autonomous systems to help pinpoint attackers and malicious infrastructures?
In which cloud services model is the customer responsible for scanning for and mitigation of application vulnerabilities?


