350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
What is the role of an endpoint in protecting a user from a phishing attack?
What is the intent of a basic SYN flood attack?
What are two features of NetFlow flow monitoring? (Choose two)
An engineer is trying to decide between using L2TP or GRE over IPsec for their site-to-site VPN implementation. What must be un solution?
An organization is trying to improve their Defense in Depth by blocking malicious destinations prior to a
connection being established. The solution must be able to block certain applications from being used within the network. Which product should be used to accomplish this goal?
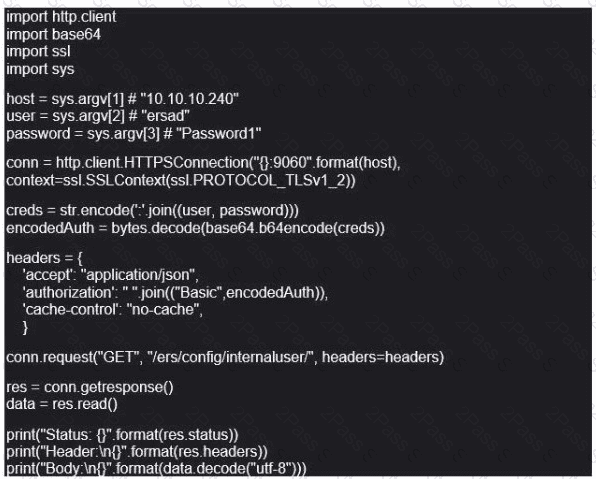
Refer to the exhibit. What does this Python script accomplish?
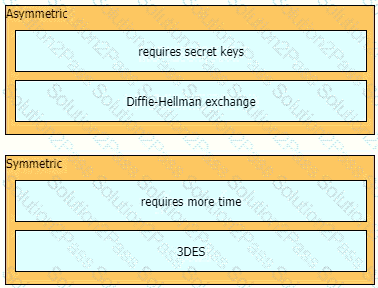
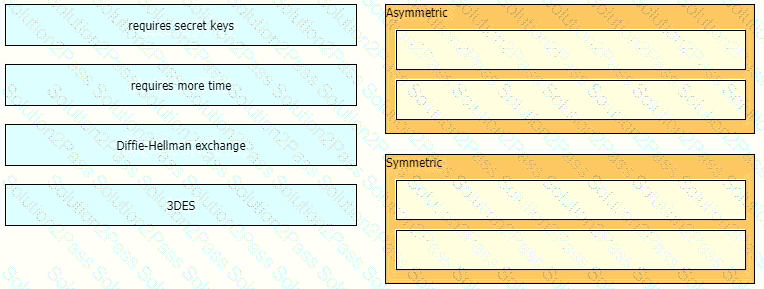
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
A Cisco ESA network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Cisco ESA is not dropping files that have an undetermined verdict. What is causing this issue?
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a
proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured
to select when to connect direct or when to use the proxy?
What is the process In DevSecOps where all changes In the central code repository are merged and synchronized?
Which method must be used to connect Cisco Secure Workload to external orchestrators at a client site when the client does not allow incoming connections?
Which cloud service model offers an environment for cloud consumers to develop and deploy applications
without needing to manage or maintain the underlying cloud infrastructure?
Which two capabilities of Integration APIs are utilized with Cisco Catalyst Center? (Choose two.)
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256
cisc0380739941 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
What are two functionalities of SDN Northbound APIs? (Choose two.)
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead. Which solution meets these requirements?
What are two characteristics of the RESTful architecture used within Cisco DNA Center? (Choose two.)
Which option is the main function of Cisco Firepower impact flags?
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise?
Where are individual sites specified to be block listed in Cisco Umbrella?
Which two Cisco ISE components must be configured for BYOD? (Choose two.)
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data
within a network perimeter?
Which benefit is provided by ensuring that an endpoint is compliant with a posture policy configured in Cisco ISE?
Which two risks is a company vulnerable to if it does not have a well-established patching solution for
endpoints? (Choose two)
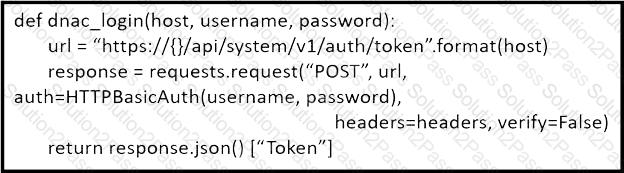
Refer to the exhibit. What is the result of the Python script?
Which type of dashboard does Cisco Catalyst Center provide for complete control of the network?
What must be configured on Cisco Secure Endpoint to create a custom detection tile list to detect and quarantine future files?
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?