350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which
probe must be enabled for this type of profiling to work?
Which Cisco ISE service checks the compliance of endpoints before allowing the endpoints to connect to
the network?
What is the purpose of the Cisco Endpoint loC feature?
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
When Cisco and other industry organizations publish and inform users of known security findings and
vulnerabilities, which name is used?
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two)
Refer to the exhibit.
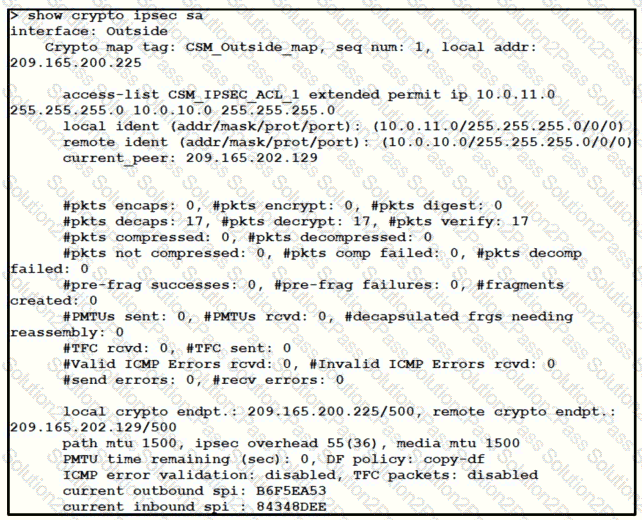
Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense appliance. What is causing this issue?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites but other sites are not accessible due to an error. Why is the error occurring?
Which component of Cisco umbrella architecture increases reliability of the service?
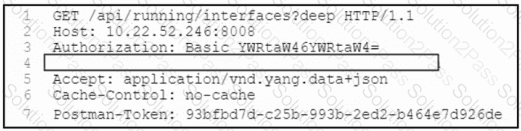
Refer to the exhibit. A network engineer must retrieve the interface configuration on a Cisco router by using the NETCONF API. The engineer uses a python script to automate the activity.
Which code snippet completes the script?
What is the process of performing automated static and dynamic analysis of files against preloaded
behavioral indicators for threat analysis?
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network?
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?
An engineer integrates Cisco FMC and Cisco ISE using pxGrid Which role is assigned for Cisco FMC?
Which industry standard is used to integrate Cisco ISE and pxGrid to each other and with other
interoperable security platforms?
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two)
Which service allows a user to export application usage and performance statistics with Cisco Application Visibility and Control?
Refer to the exhibit.
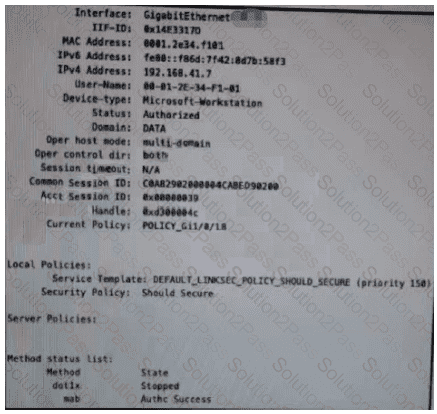
Which configuration item makes it possible to have the AAA session on the network?
Which two functions does the Cisco Advanced Phishing Protection solution perform in trying to protect from phishing attacks? (Choose two.)
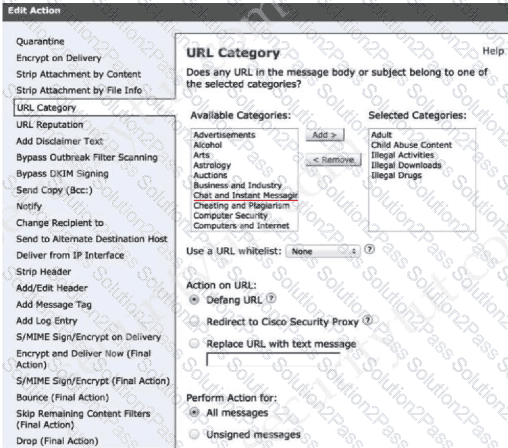
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the “Chat and Instant Messaging” category. Which reputation score should be selected to accomplish this goal?
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view
of activity?
What is a difference between FlexVPN and DMVPN?
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
Which Cisco AMP feature allows an engineer to look back to trace past activities, such as file and process
activity on an endpoint?
Which technology must De used to Implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
Which problem Is solved by deploying a multicontext firewall?
An organization wants to improve its cybersecurity processes and to add intelligence to its data The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA What must be done to accomplish these objectives?
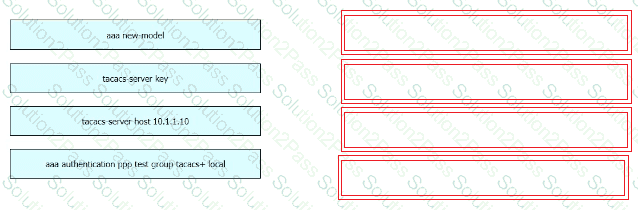
Refer to the exhibit.

An engineer must configure a Cisco switch to perform PPP authentication via a TACACS server located at IP address 10.1.1.10. Authentication must fall back to the local database using the username LocalUser and password C1Sc0451069341l if the TACACS server is unreachable.
Drag and drop the commands from the left onto the corresponding configuration steps on the right.
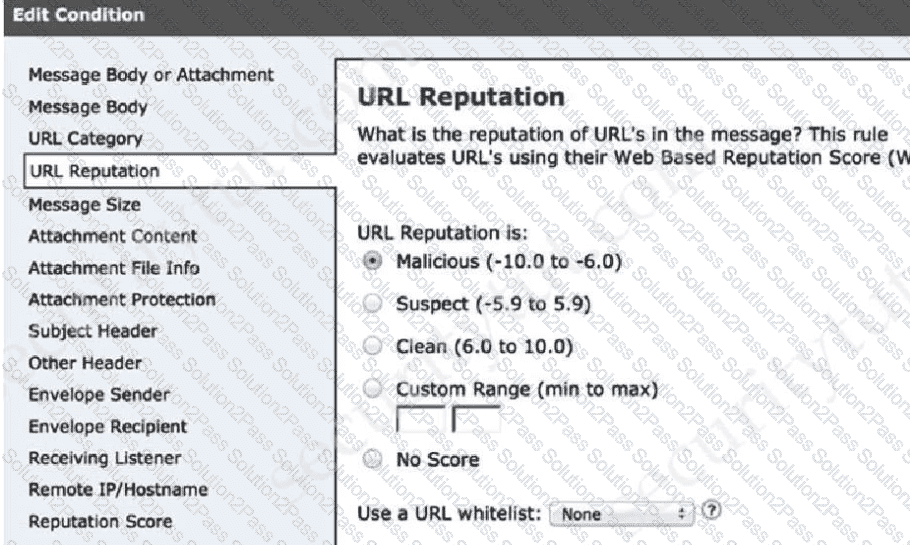
Email security has become a high priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10 00 to -6 00) on the Cisco ESA Which action will the system perform to disable any links in messages that match the filter?