350-701 Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
An engineer is configuring guest WLAN access using Cisco ISE and the Cisco WLC. Which action temporarily gives guest endpoints access dynamically while maintaining visibility into who or what is connecting?
What is a characteristic of an EDR solution and not of an EPP solution?
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services
Engine? (Choose two)
An organization configures Cisco Umbrella to be used for its DNS services. The organization must be able to block traffic based on the subnet that the endpoint is on but it sees only the requests from its public IP address instead of each internal IP address. What must be done to resolve this issue?
Why is it important for the organization to have an endpoint patching strategy?
Refer to the exhibit.
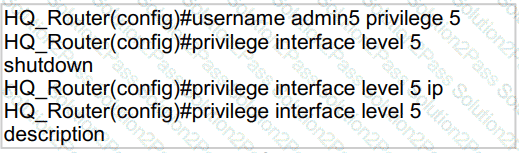
A network administrator configures command authorization for the admin5 user. What is the admin5 user able to do on HQ_Router after this configuration?
