350-901 Cisco Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the result of a successful OAuth2 authorization grant flow?
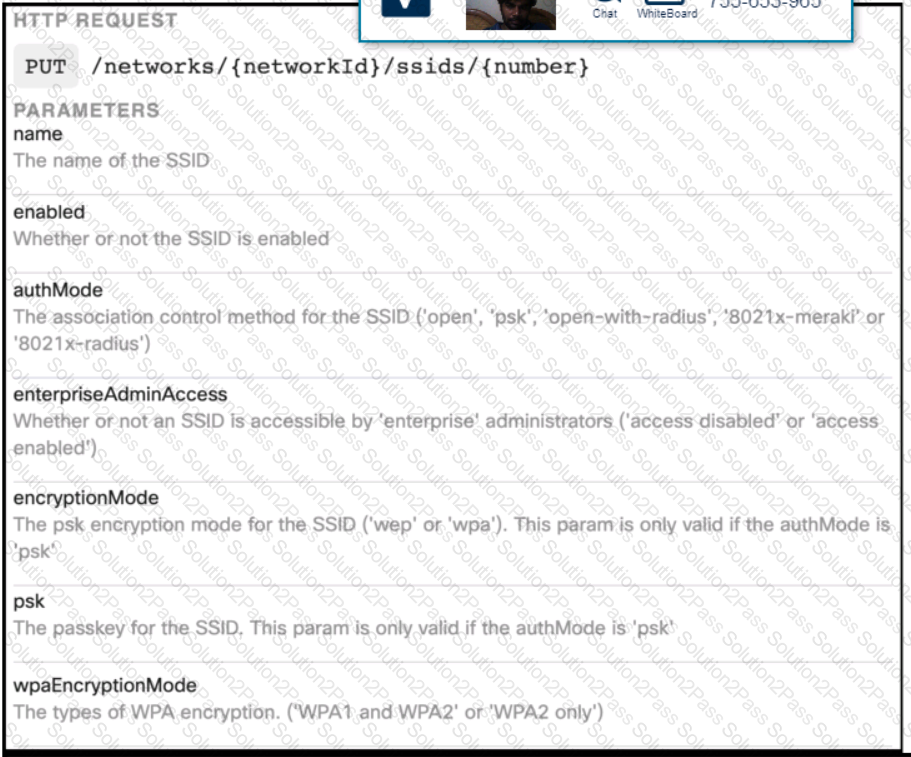
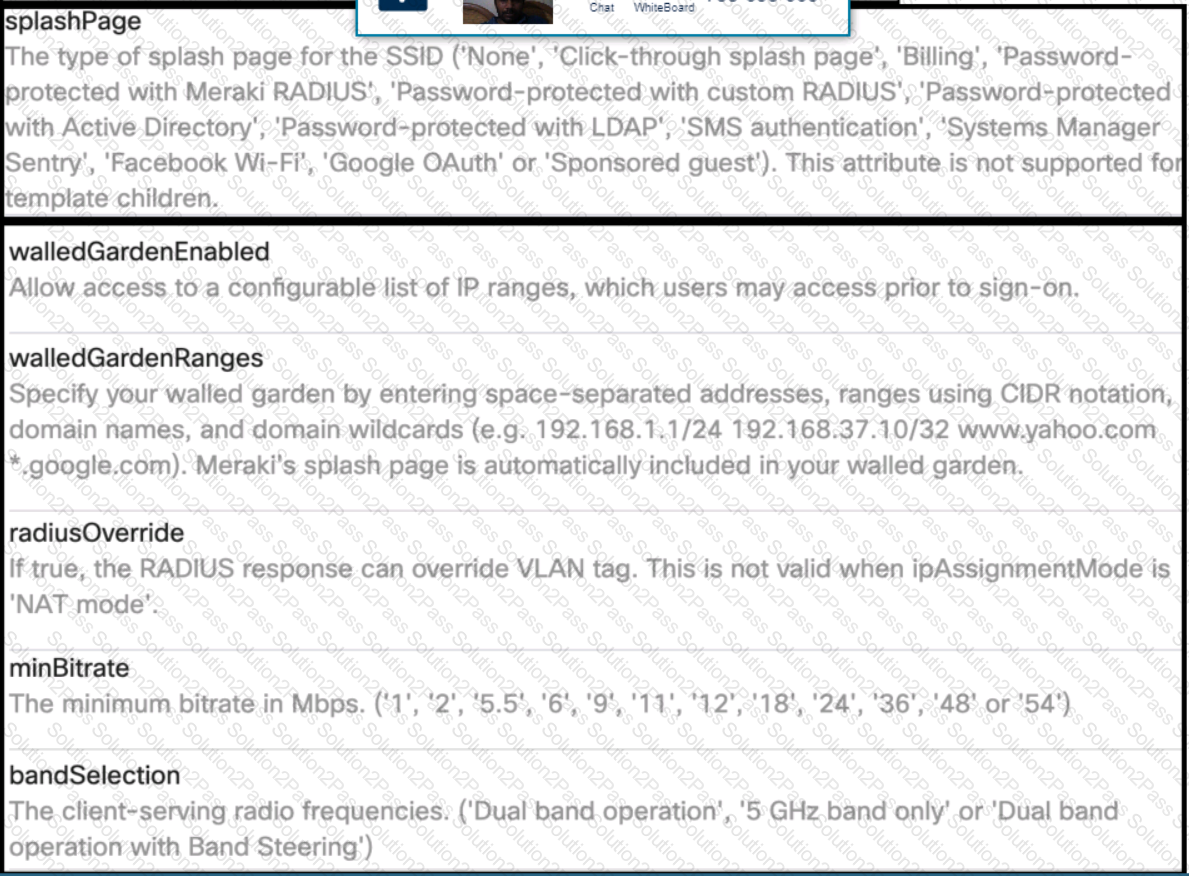
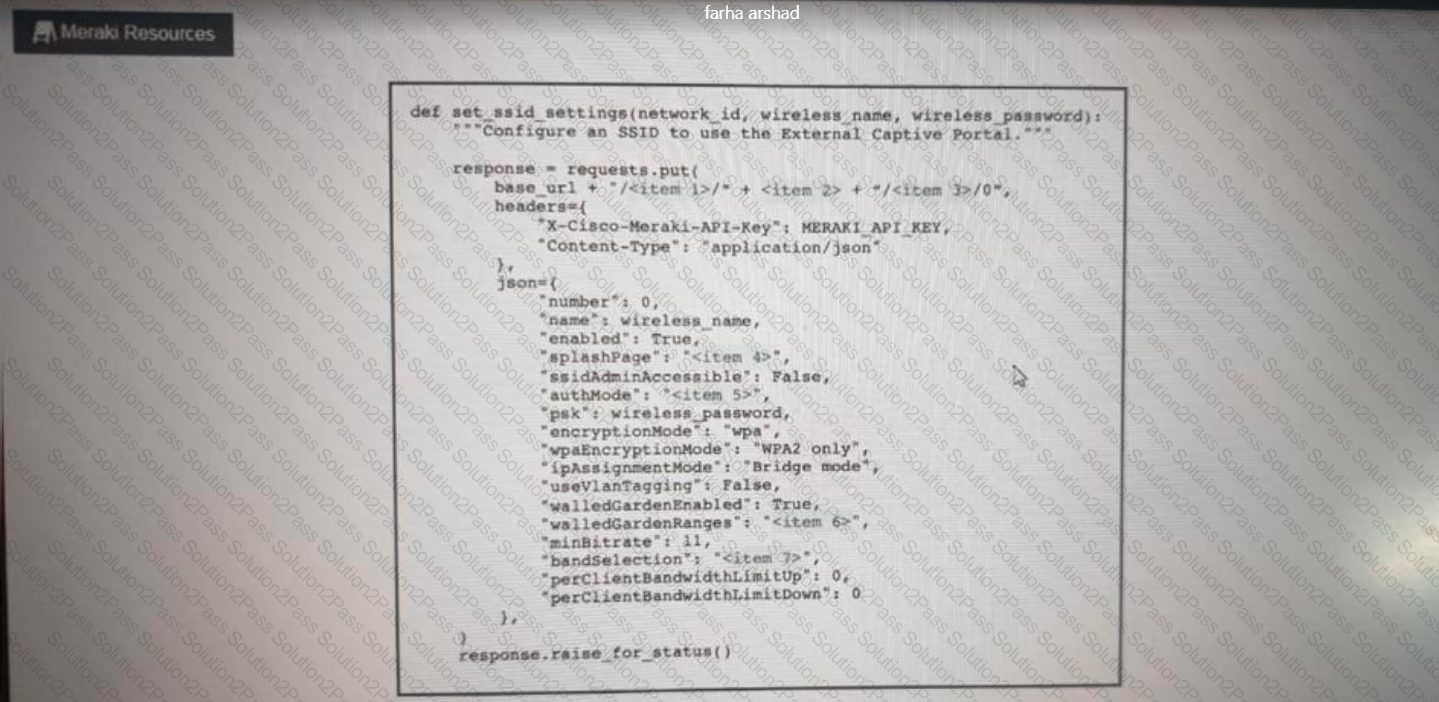
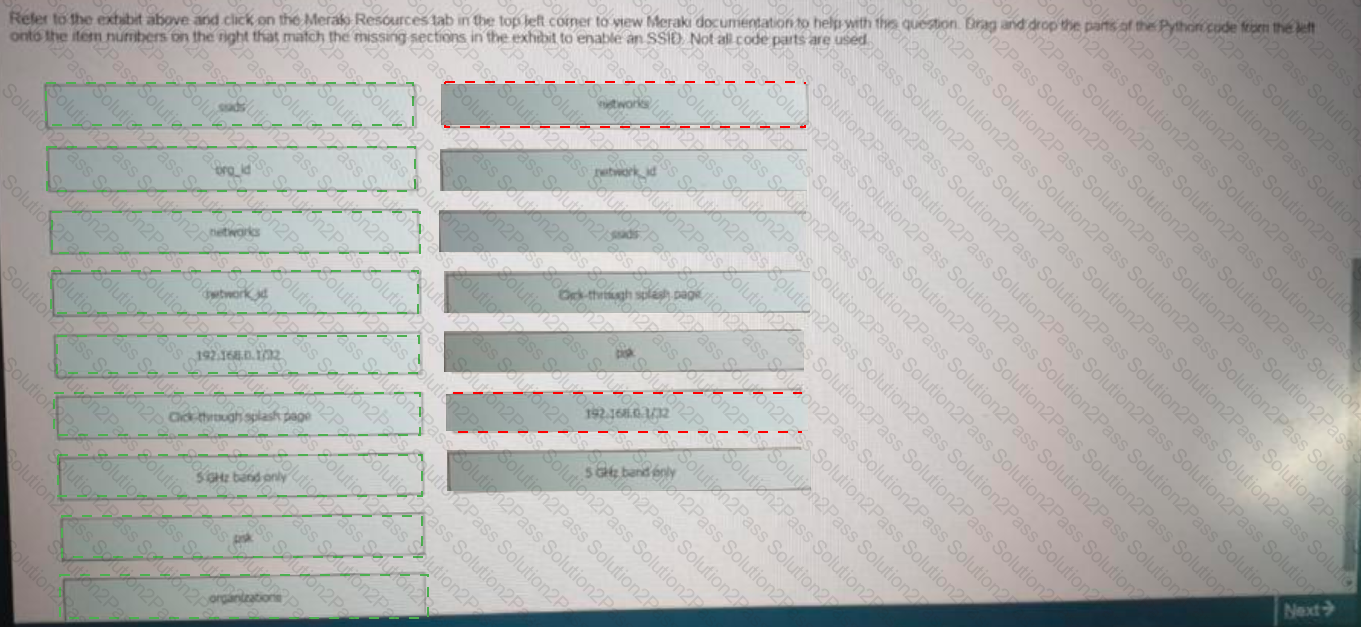
Click on the Meraki Resources tab in the left corner to view Meraki documentation to help with this question.Drag and drop the parts of the python code from the left onto the item numbers on the right that match the missing sections in the exhibit to enable an SSID. Not all code parts are used.
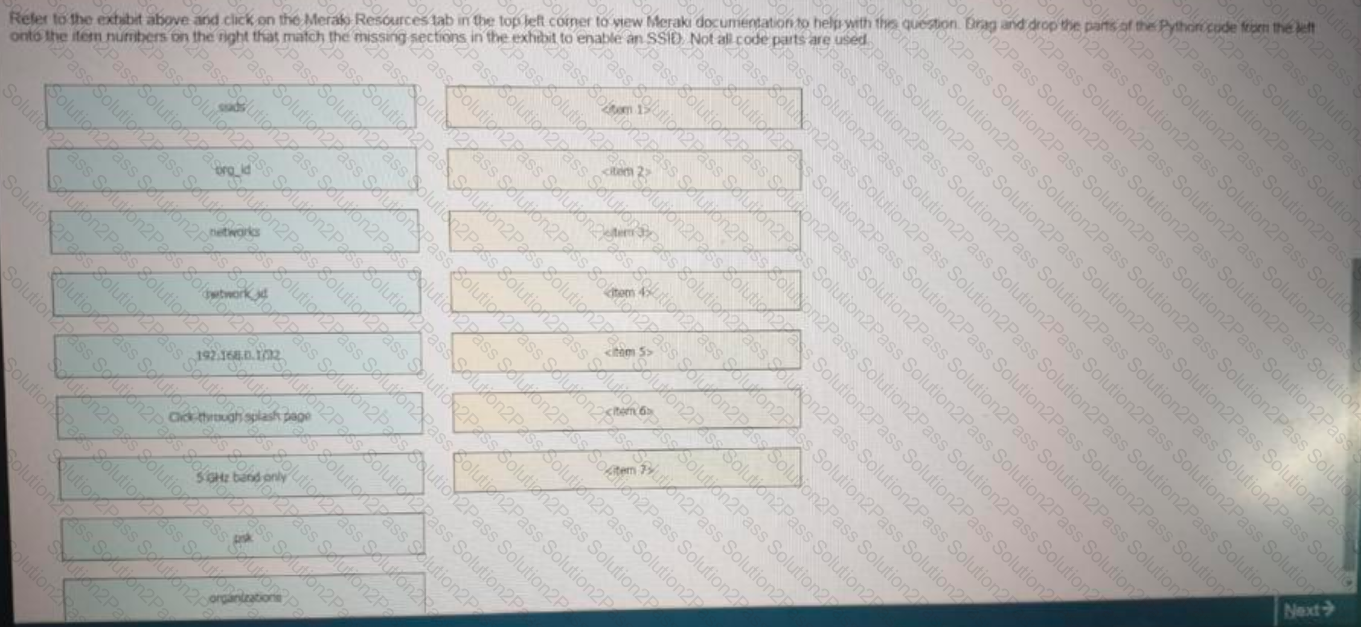
Refer to the exhibit.
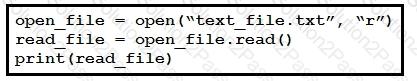
A developer created the code, but it fails to execute. Which code snippet helps to identify the issue?
Which two encryption principles should be applied to secure APIs? (Choose two.)
A new record-keeping application for employees to track customer orders must be deployed to a company's existing infrastructure. The host servers reside in a data center in a different country to where the majority of users work. The new network configuration for the database server is: •IP: 10.8.32.10
• Subnet Mask: 255.255.255.0
• Hostname: CustOrd423320458-Prod-010
• MAC: 18-46-AC-6F-F4-52.
The performance of the client-side application is a priority due to the high demand placed on it by employees. Which area should the team consider in terms of impact to application performance due to the planned deployment?
Refer to the exhibit.
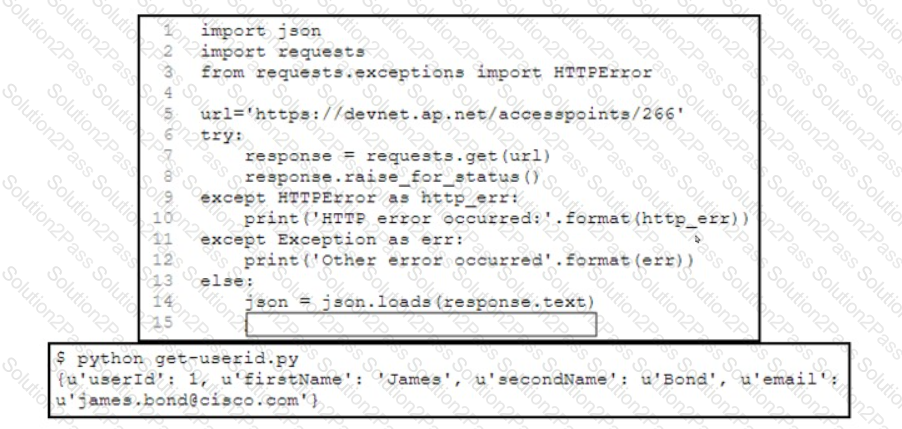
A developer has created a Python script that retrieves information about the deployment of Cisco wireless access points using REST API. Which two code snippets must be added to the blank in the code to print the value of the userid key instead of printing the full JSON response? (Choose two.)
A)

B)

C)

D)
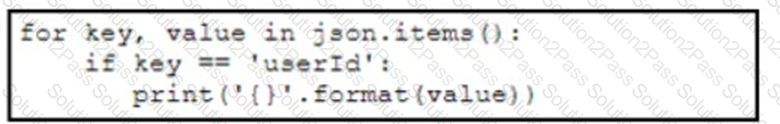
E)
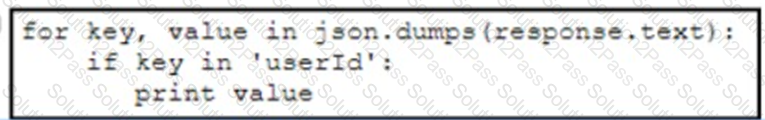
Refer to the exhibit.
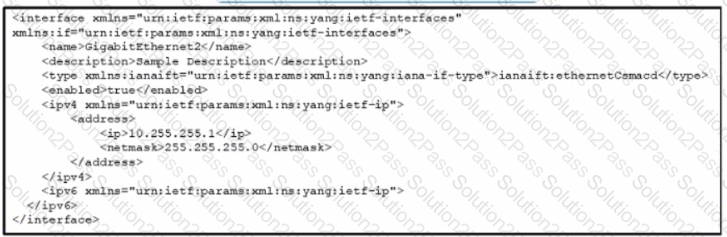
A)

B)

C)

D)

What is a risk to data privacy during the storage and transmission of data?