400-007 Cisco Certified Design Expert (CCDE v3.1) Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Cisco 400-007 Cisco Certified Design Expert (CCDE v3.1) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Refer to the exhibit.
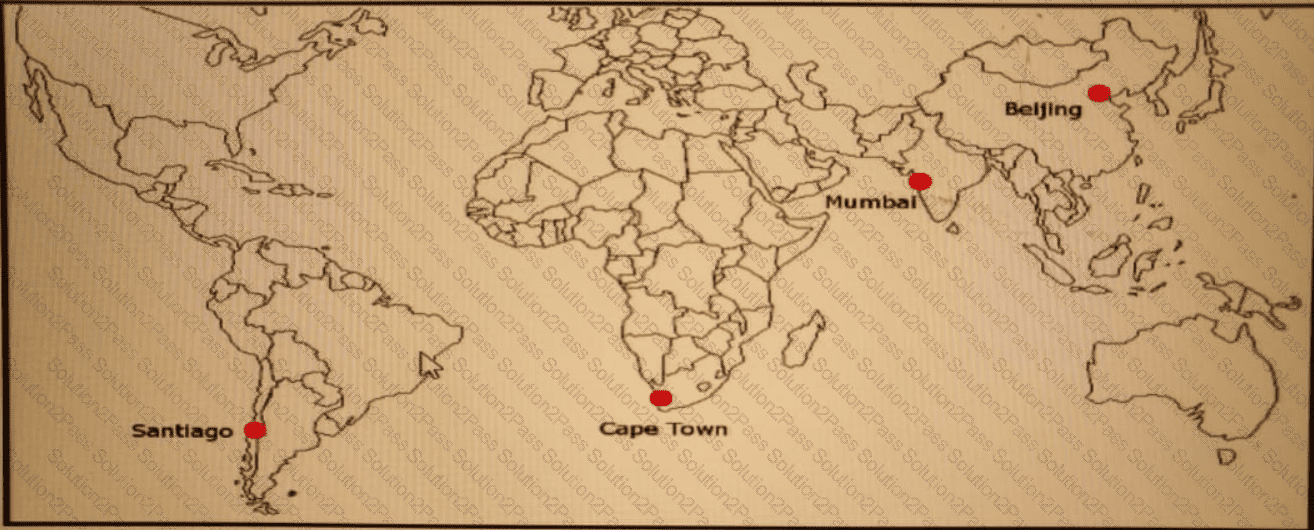
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
clusterheartbeat2Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
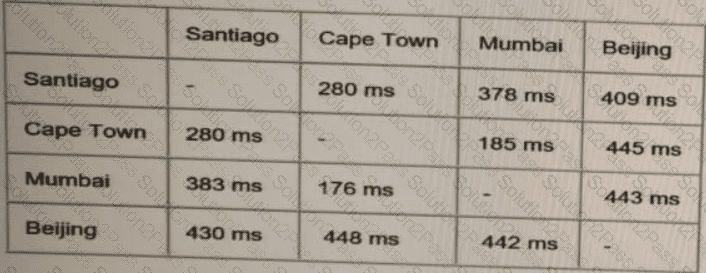
Which hosting data center pair can host the new application?
Which three tools are used for ongoing monitoring and maintenance of a voice and video environment? (Choose three.)
The Company XYZ network requires OSPF dead neighbor detection in a subsecond manner. However, the company network does not support BFD. Which other feature can be used to fulfill the design requirement?
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
Which two design options are available to dynamically discover the RP in an IPv6 multicast network? (Choose two)
Refer to the exhibit.
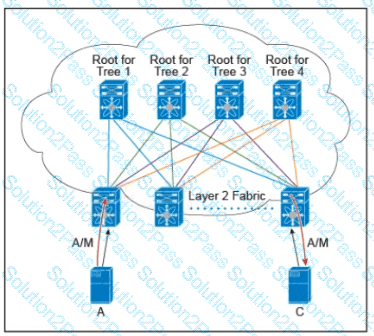
There are multiple trees in the Cisco FabricPath. All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two.)
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol. A spoke-to-spoke data propagation model must be set up. Which two design considerations must be taken into account? (Choose two)
What are two examples of components that are part of an SDN architecture? (Choose two.)
The goal for any network designer is to strive to build a resilient network that adapts to changing conditions rapidly with minimal impact on the services running over the network. A resilient network can adapt to failures, but which soft failure can be harder to define and detect?
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two.)
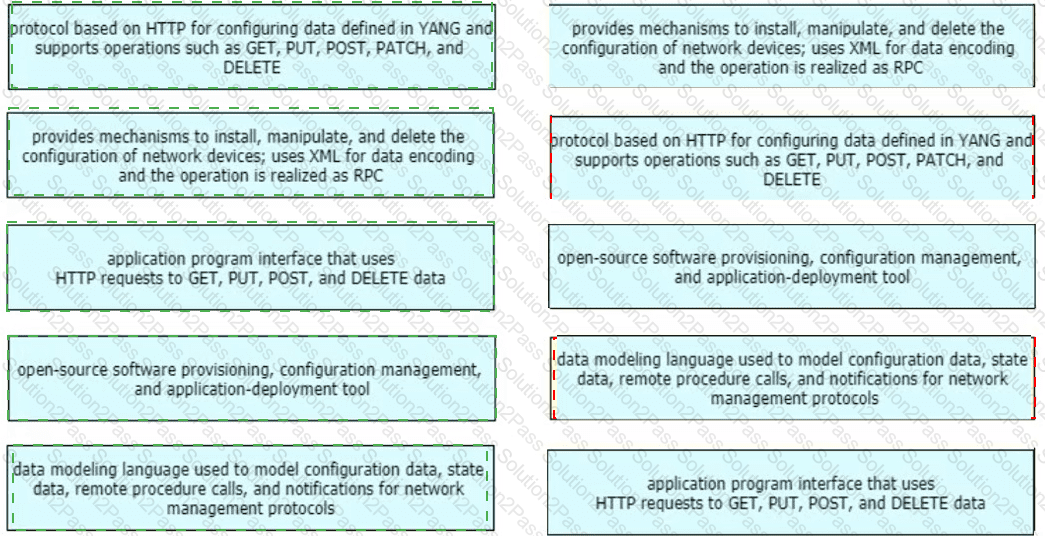
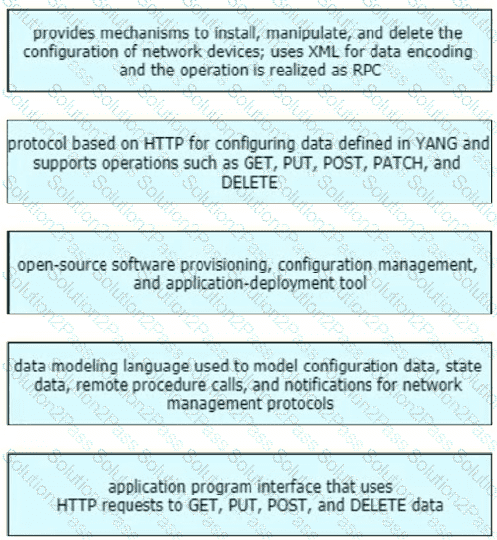
Drag and drop the characteristics from the left onto the corresponding network management options on the right.
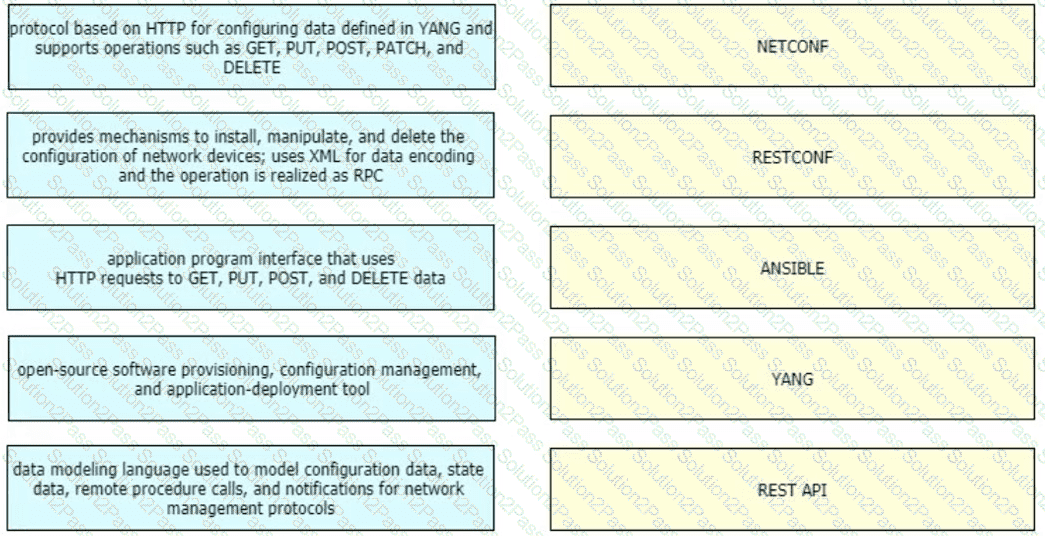
What are two descriptions of network optimization? (Choose two.)
A business wants to refresh its legacy Frame Relay WAN and consolidate product specialists via video in 200 branches. Which technology should be used?
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two.)
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
Which SDN architecture component is used by the application layer to communicate with the control plane layer to provide instructions about the resources required by applications?
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
Which two features describe controller-based networking solutions compared to traditional networking solutions? (Choose two.)
Which tool automates network implementation activities and shortens the implementation lifecycle?
What is a characteristic of a secure cloud architecture model?
 Text
Description automatically generated
Text
Description automatically generated