CAS-005 CompTIA SecurityX Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CAS-005 CompTIA SecurityX Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A security architect must make sure that the least number of services as possible is exposed in order to limit an adversary's ability to access the systems. Which of the following should the architect do first?
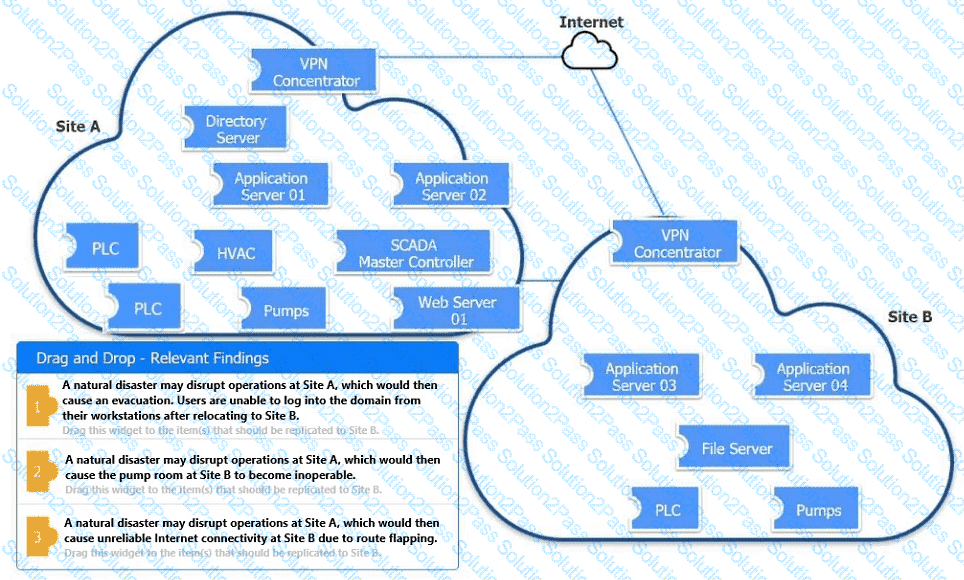
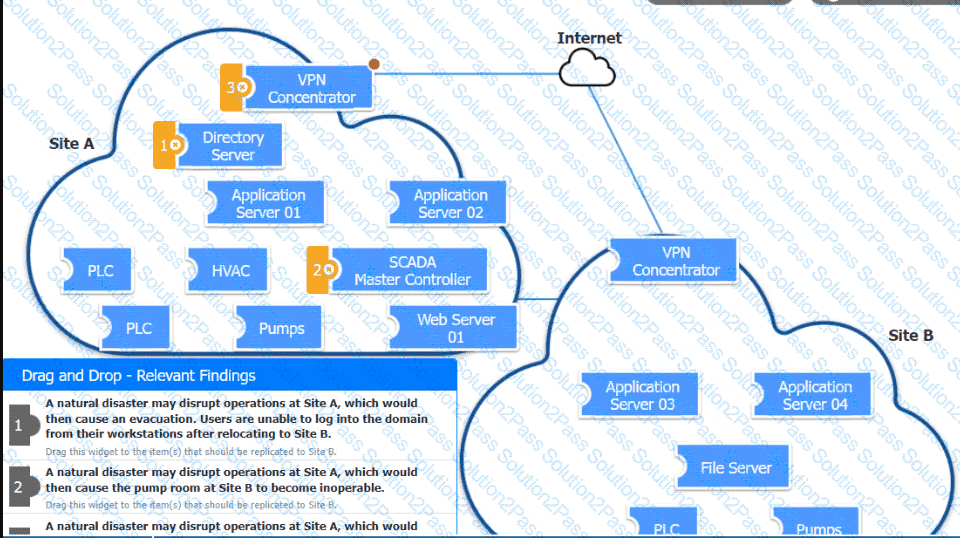
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
A company discovers intellectual property data on commonly known collaboration web applications that allow the use of slide templates. The systems administrator is reviewing the configurations of each tool to determine how to prevent this issue. The following security solutions are deployed:
CASB
SASE
WAF
EDR
Firewall
IDS
SIEM
DLP endpoints
Which of the following should the administrator do to address the issue?
An organization determines existing business continuity practices are inadequate to support critical internal process dependencies during a contingency event. A compliance analyst wants the Chief Information Officer (CIO) to identify the level of residual risk that is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
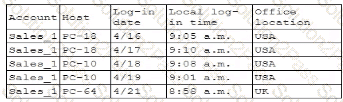
Which of the following is the security engineer most likely doing?
A security engineer is implementing a code signing requirement for all code developed by the organization. Currently, the PKI only generates website certificates. Which of the following steps should the engineer perform first?
An incident response analyst finds the following content inside of a log file that was collected from a compromised server:
.2308464678 ... whoami ..... su2032829%72%322/// ...... /etc/passwd .... 2087031731467478432 ...
$6490/90/./ ..< XML ?.. .... nty.
Which of the following is the best action to prevent future compromise?
A company wants to protect against the most common attacks and rapidly integrate with different programming languages. Which of the following technologies is most likely to meet this need?
A senior security engineer flags the following log file snippet as having likely facilitated an attacker’s lateral movement in a recent breach:
qry_source: 19.27.214.22 TCP/53
qry_dest: 199.105.22.13 TCP/53
qry_type: AXFR
| in comptia.org
------------ directoryserver1 A 10.80.8.10
------------directoryserver2 A 10.80.8.11
------------ directoryserver3 A 10.80.8.12
------------ internal-dns A 10.80.9.1
----------- www-int A 10.80.9.3
------------ fshare A 10.80.9.4
------------ sip A 10.80.9.5
------------ msn-crit-apcs A 10.81.22.33
Which of the following solutions, if implemented, would mitigate the risk of this issue reoccurring?
A user reports application access issues to the help desk. The help desk reviews the logs for the user
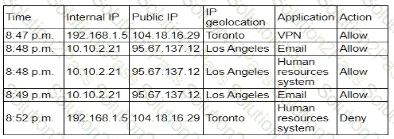
Which of the following is most likely The reason for the issue?
A developer needs toimprove the cryptographic strength of a password-storage component in a web application without completely replacing the crypto-module. Which of the following is the most appropriate technique?
A security analyst is performing a review of a web application. During testing as a standard user, the following error log appears:
Error Message in Database Connection
Connection to host USA-WebApp-Database failed
Database "Prod-DB01" not found
Table "CustomerInfo" not found
Please retry your request later
Which of the following best describes the analyst’s findings and a potential mitigation technique?
Source code snippets for two separate malware samples are shown below:
Sample 1:
knockEmDown(String e) {
if(target.isAccessed()) {
target.toShell(e);
System.out.printIn(e.toString());
c2.sendTelemetry(target.hostname.toString + " is " + e.toString());
} else {
target.close();
}
}
Sample 2:
targetSys(address a) {
if(address.islpv4()) {
address.connect(1337);
address.keepAlive("paranoid");
String status = knockEmDown(address.current);
remote.sendC2(address.current + " is " + status);
} else {
throw Exception e;
}
}
Which of the following describes the most important observation about the two samples?
A security architect wants to configure a mail server so it maintains an updated list of IoCs and blocks known-malicious incoming emails. Which of the following will the security architect most likely need for this task? (Select two)
Which of the following are risks associated with vendor lock-in? (Select two).
A developer makes a small change to a resource allocation module on a popular social media website and causes a memory leak. During a peak utilization period, several web servers crash, causing the website to go offline. Which of the following testing techniques is the most efficient way to prevent this from reoccurring?
A compliance officer isfacilitating abusiness impact analysis (BIA)and wantsbusiness unit leadersto collect meaningful data. Several business unit leaders want more information about the types of data the officer needs.
Which of the following data types would be the most beneficial for the compliance officer?(Select two)
Which of the following supports the process of collecting a large pool of behavioral observations to inform decision-making?
A company's Chief Information Security Officer learns that the senior leadership team is traveling to a country accused of attempting to steal intellectual property saved on laptops. Which of the following is the best method to protect against this attack?
An incident response team is analyzing malware and observes the following:
• Does not execute in a sandbox
• No network loCs
• No publicly known hash match
• No process injection method detected
Which of thefollowing should the team do next to proceed with further analysis?

 A computer screen shot of a diagram Description automatically generated
A computer screen shot of a diagram Description automatically generated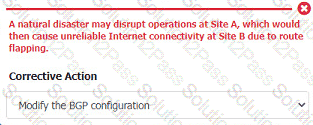 A screenshot of a computer error Description automatically generated
A screenshot of a computer error Description automatically generated