CAS-005 CompTIA SecurityX Certification Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CAS-005 CompTIA SecurityX Certification Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An organization is deploying a new data lake that will centralize records from several applications. During the design phase, the security architect identifies the following requirements:
• The sensitivity levels of the data is different.
• The data must be accessed through stateless API calls after authentication.
• Different users will have access to different data sets.
Which of the following should the architect implement to best meet these requirements?
Asoftware company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?
An organization would like to increase the effectiveness of its incident response process across its multiplatform environment. A security engineer needs to implement the improvements using the organization's existing incident response tools. Which of the following should the security engineer use?
A company implements an Al model that handles sensitive and personally identifiable information. Which of the following threats is most likely the company's primary concern?
A security team is responding to malicious activity and needs to determine the scope of impact the malicious activity appears to affect certain version of an application used by the organization Which of the following actions best enables the team to determine the scope of Impact?
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the least amount of downtime. Which of the following should the analyst perform?
Embedded malware has been discovered in a popular PDF reader application and is currently being exploited in the wild. Because the supply chain was compromised, this malware is present in versions 10.0 through 10.3 of the software's official versions. The malware is not present in version 10.4.
Since the details around this malware are still emerging, the Chief Information Security Officer has asked the senior security analyst to collaborate with the IT asset inventory manager to find instances of the installed software in order to begin response activities. The asset inventory manager has asked an analyst to provide a regular expression that will identify the affected versions. The software installation entries are formatted as follows:
Reader 10.0
Reader 10.1
Reader 10.2
Reader 10.3
Reader 10.4
Which of the following regular expression entries will accuratelyidentify all the affected versions?
An organization is implementing advanced security controls associated with the execution of software applications on corporate endpoints. The organization must implement a deny-all, permit-by-exception approach to software authorization for all systems regardless of OS. Which of the following should be implemented to meet these requirements?
A company was recently infected by malware. During the root cause analysis, the company determined that several users were installing their own applications. To prevent further compromises, the company has decided it will onlyallow authorized applications to run on its systems. Which of the following should the company implement?
After several companies in the financial industry were affected by a similar incident, they shared information about threat intelligence and the malware used for exploitation. Which of the following should the companies do to best indicate whether the attacks are being conducted by the same actor?
An external SaaS solution user reports a bug associated with the role-based access control module. This bug allows users to bypass system logic associated with client segmentation in the multitenant deployment model. When assessing the bug report, the developer finds that the same bug was previously identified and addressed in an earlier release. The developer then determines the bug was reintroduced when an existing software component was integrated from a prior version of the platform. Which of the following is the best way to prevent this scenario?
A security analyst needs to ensure email domains that send phishing attempts without previous communications are not delivered to mailboxes The following email headers are being reviewed
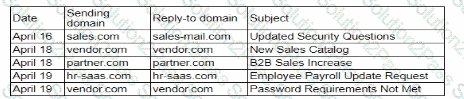
Which of thefollowing is the best action for the security analyst to take?
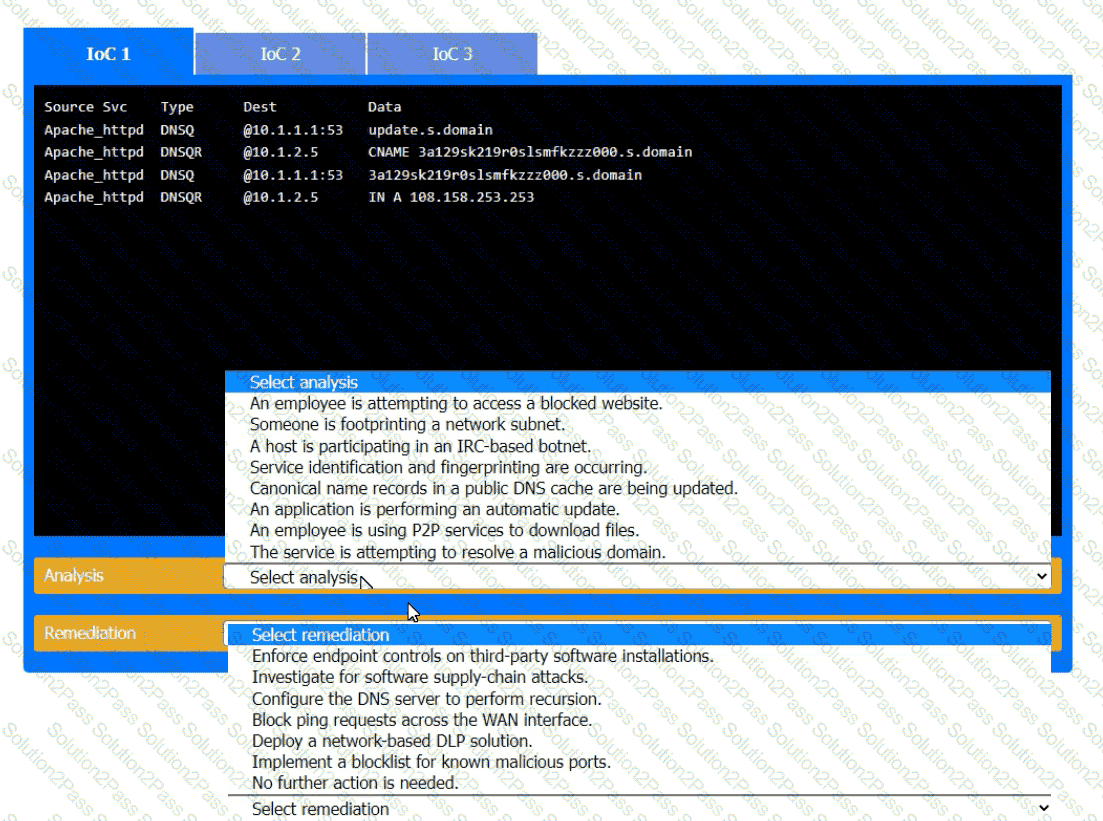
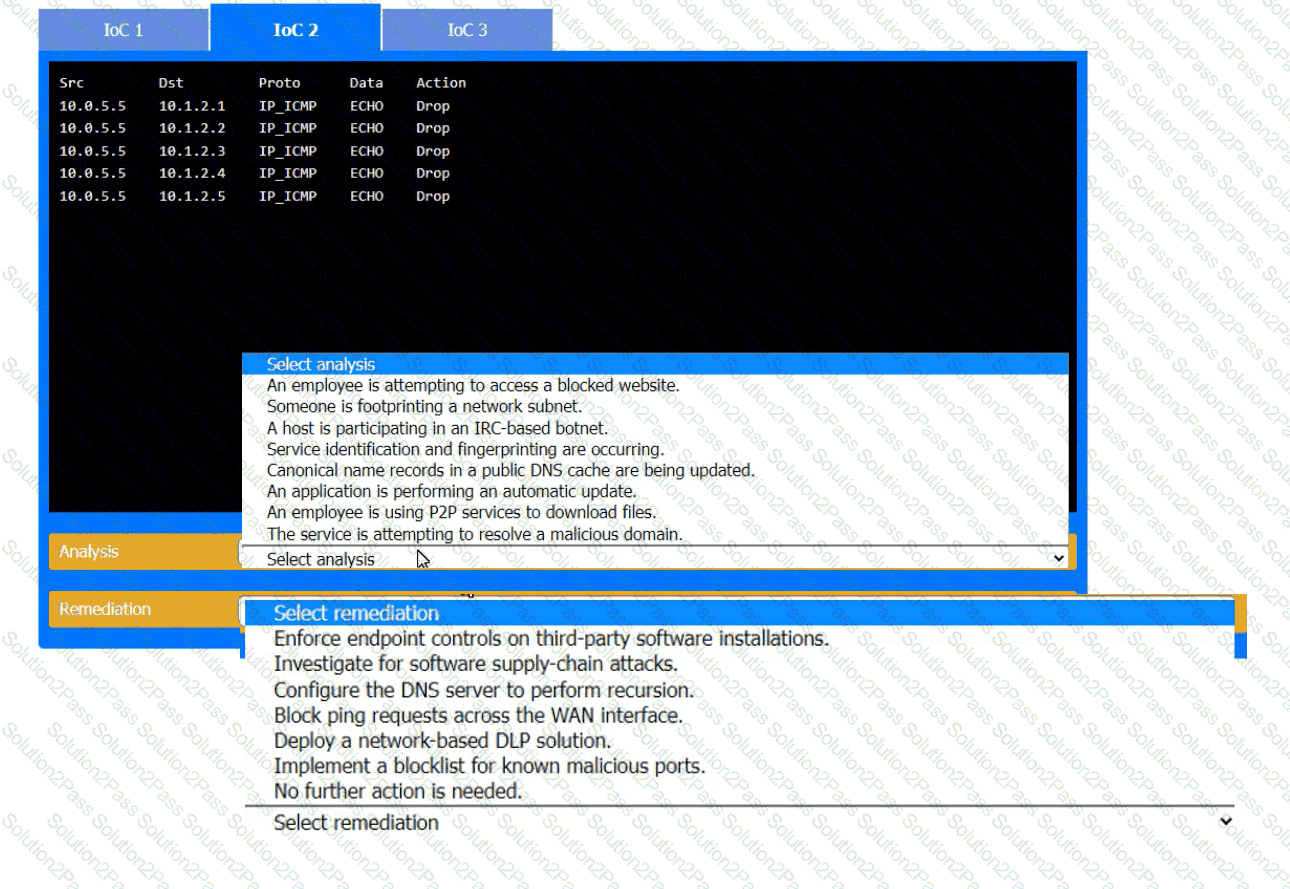
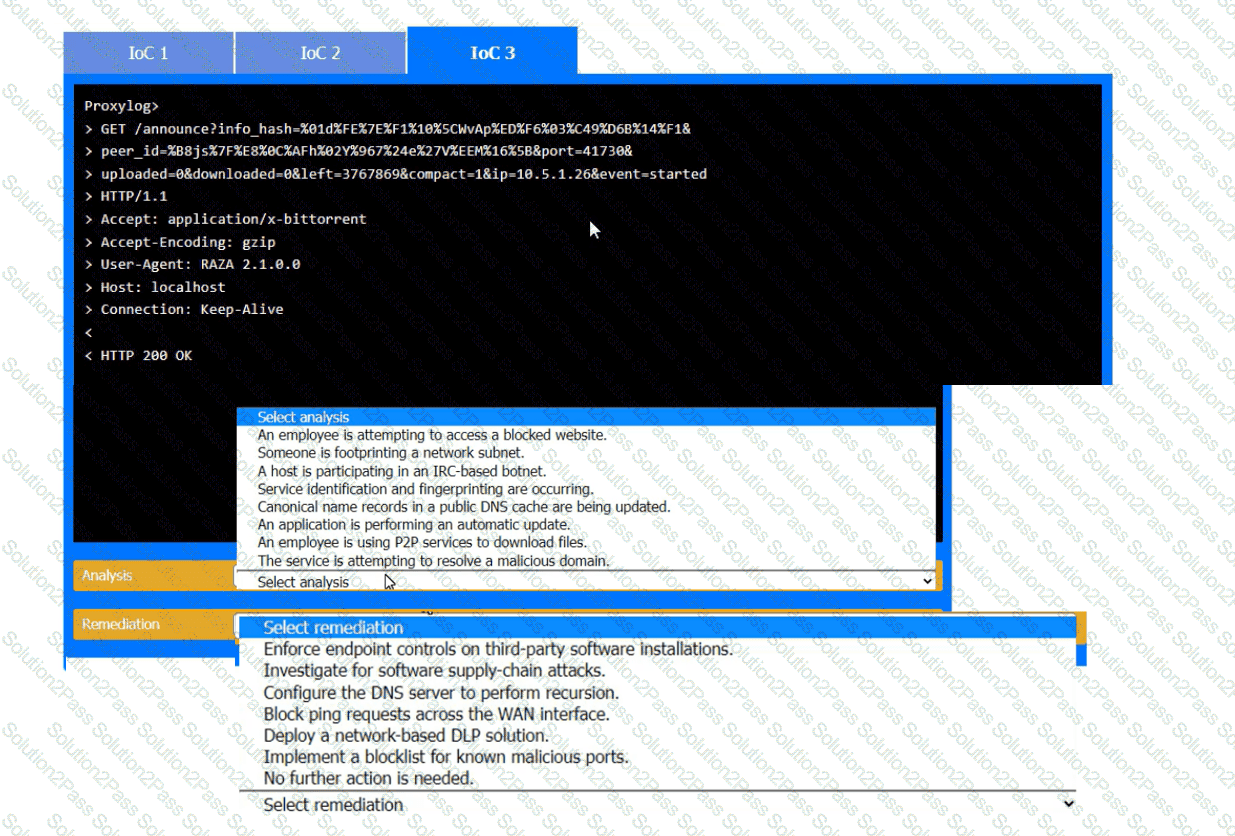
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
Review each of the events and select the appropriate analysis and remediation options for each IoC.
A security architect is performing threat-modeling activities related to an acquired overseas software company that will be integrated with existing products and systems Once its software is integrated, the software company will process customer data for the acqumng company Given the following:
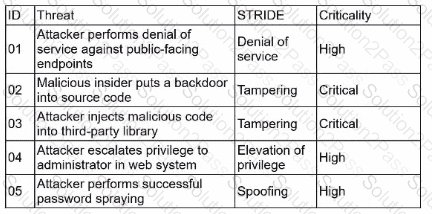
Which of the following mitigations would reduce the risk of the most significant threats?
A security engineer receives an alert from the threat intelligence platform with the following information:
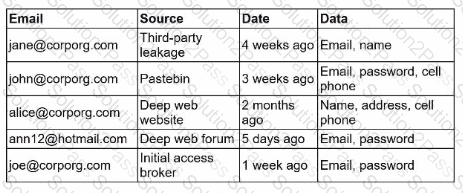
Which of the following actions should the security engineer do first?
Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
Which of the following best describes the reason PQC preparation is important?
Company A acquired Company B and needs to determine how the acquisition will impact the attack surface of the organization as a whole. Which of the following is the best way to achieve this goal? (Select two).
Implementing DLP controls preventing sensitive data from leaving Company B's network
A security operations analyst is reviewing network traffic baselines for nightly database backups. Given the following information:
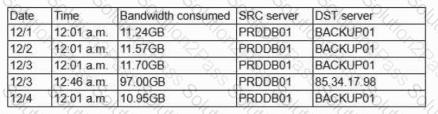
Which of the following should the security analyst do next?
