CV0-004 CompTIA Cloud+ (2025) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CV0-004 CompTIA Cloud+ (2025) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A cloud solutions architect needs to have consistency between production, staging, and development environments. Which of the following options will best achieve this goal?
A company developed an online trading platform. The engineering team selected event-based scaling for the platform's underlying resources. The platform resources scale up with every 2,000 subscribed users. The engineering team finds out that although compute utilization is low, scaling is still occurring. Which of the following statements best explains why this is the case?
An IT manager needs to deploy a cloud solution that meets the following requirements:
. Users must use two authentication methods to access resources.
· Each user must have 10GB of storage space by default.
Which of the following combinations should the manager use to provision these requirements?
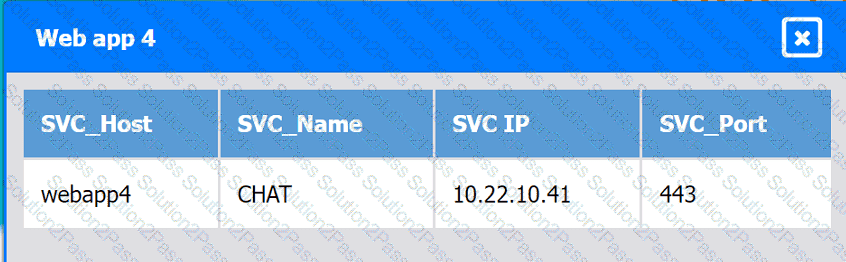
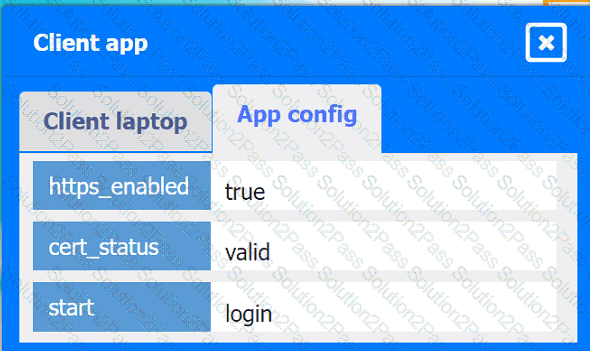
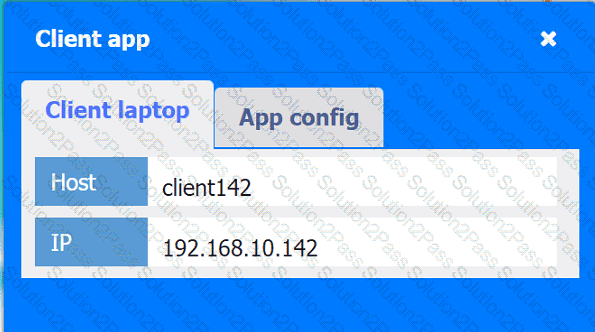
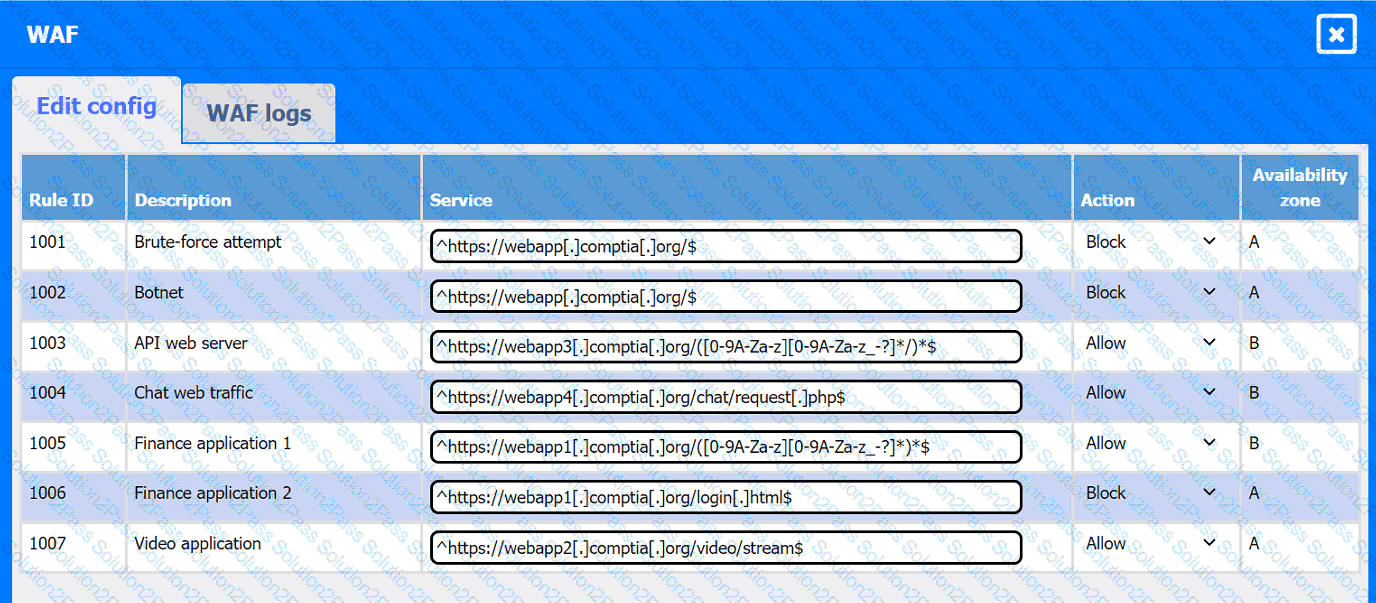
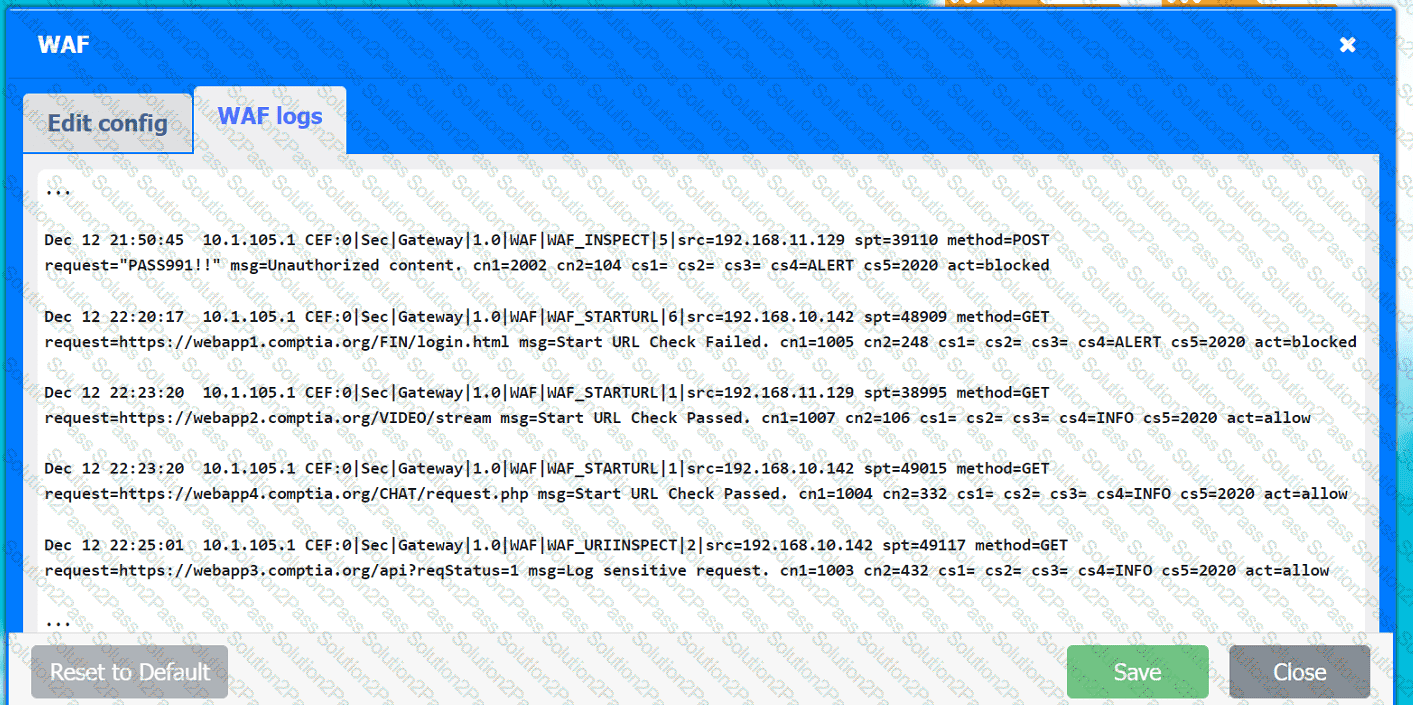
A company hosts various containerized applications for business uses. A client reports that one of its routine business applications fails to load the web-based login prompt hosted in the company cloud.
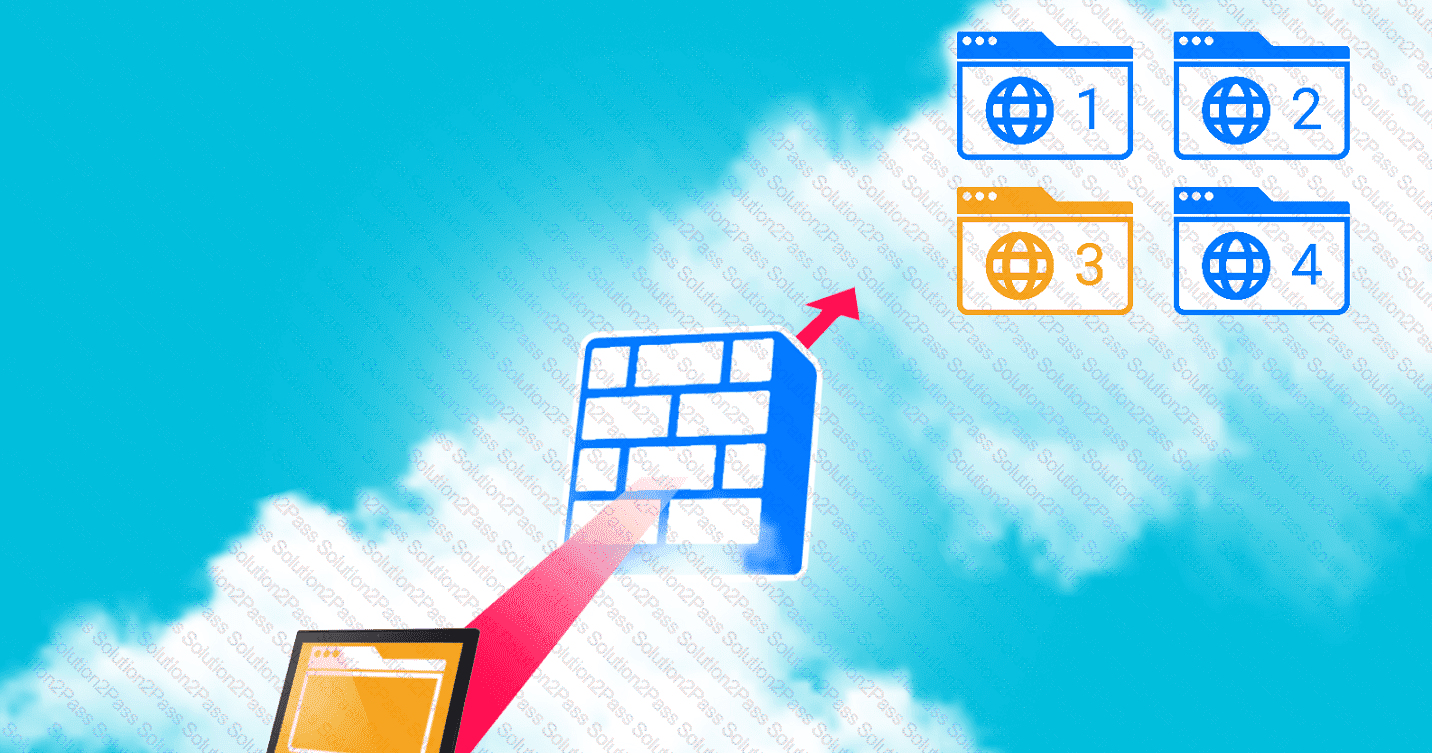
INSTRUCTIONS
Click on each device and resource. Review the configurations, logs, and characteristics of each node in the architecture to diagnose the issue. Then, make the necessary changes to the WAF configuration to remediate the issue.
Web app 1
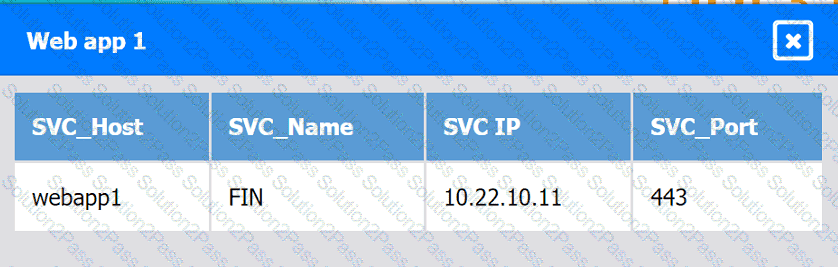
Web app 2
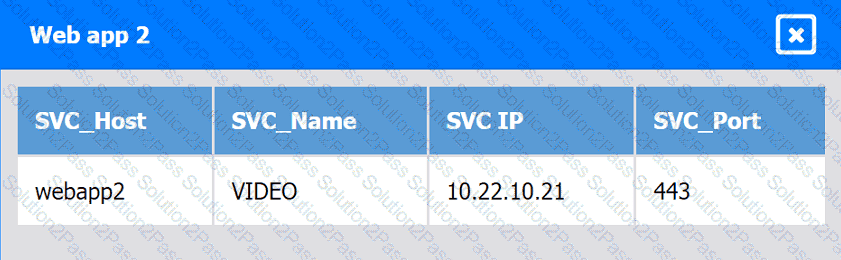
Web app 3
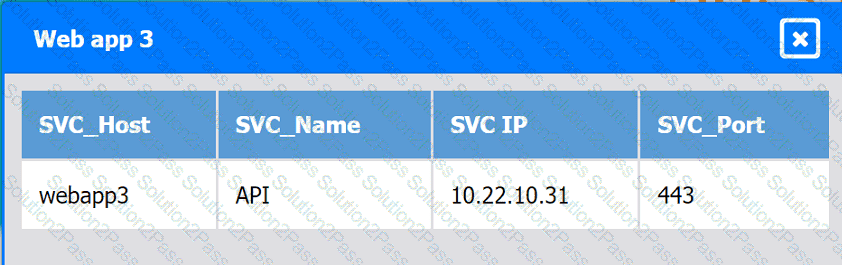
Web app 4
Client app
A cloud engineer is developing an operating expense report that will be used to purchase various cloud billing models for virtual machine instances. The cloud billing model must meet the following requirements:
• The instance cannot be ephemeral.
• The minimum life cycle of the instance is expected to be five years.
• The software license is charged per physical CPU count.
Which of the following models would best meet these requirements?
A cloud administrator deploys new VMs in a cluster and discovers they are getting IP addresses in the range of 169.254.0.0/16. Which of the following is the most likely cause?
A cloud administrator wants to provision a host with two VMs. The VMs require the following:
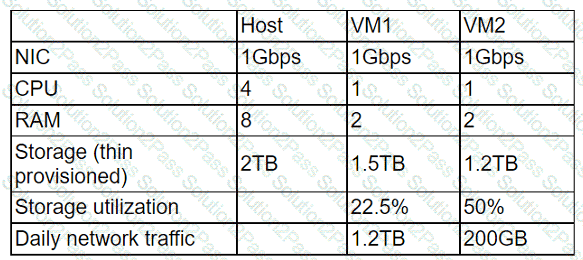
After configuring the servers, the administrator notices that during certain hours of the day, the performance heavily degrades. Which of the following is the best explanation?
A developer is sending requests to a SaaS application. The developer becomes unable to send more requests after sending a number of them, but other developers can still send requests. Which of the following is most likely causing the issue?
A technician receives an email from a vendor who is requesting payment of an invoice for human resources services. The email contains a request for bank account numbers. Which of the following types of attacks does this behavior most likely indicate?
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
Users report being unable to access an application that uses TLS 1.1. The users are able to access other applications on the internet. Which of the following is the most likely
reason for this issue?
Which of the following network protocols is generally used in a NAS environment?
An e-commerce store is preparing for an annual holiday sale. Previously, this sale has increased the number of transactions between two and ten times the normal level of
transactions. A cloud administrator wants to implement a process to scale the web server seamlessly. The goal is to automate changes only when necessary and with minimal cost.
Which of the following scaling approaches should the administrator use?
A customer is migrating applications to the cloud and wants to grant authorization based on the classification levels of each system. Which of the following should the customer implement to ensure authorisation to systems is granted when the user and system classification properties match? (Select two).
A cloud engineer is concerned about command-and-control (C2) communication out of a cloud network over HTTPS. Which of the following should the cloud engineer implement to most efficiently identify the type of communication?
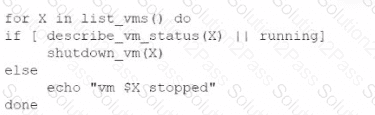
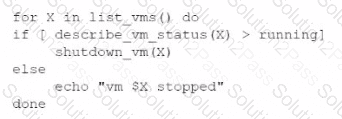
An administrator is creating a cron job that shuts down the virtual machines at night to save on costs. Which of the following is the best way to achieve this task?
A)
B)
C)
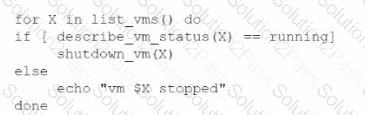
D)
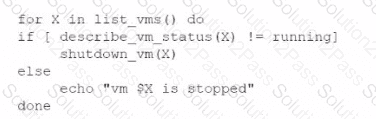
Which of the following is an auditing procedure that ensures service providers securely manage the data to protect the interests of the organization and the privacy of its clients?
A cloud engineer wants containers to run the latest version of a container base image to reduce the number of vulnerabilities. The applications in use requite Python 3.10 and ate not compatible with any other version. The containers' images are created every time a new version is released from the source image. Given the container Dockerfile below:

Which of the following actions will achieve the objectives with the least effort?
Following a ransomware attack, the legal department at a company instructs the IT administrator to store the data from the affected virtual machines for a minimum of one year.
Which of the following is this an example of?
A cloud administrator needs to collect process-level, memory-usage tracking for the virtual machines that are part of an autoscaling group. Which of the following is the best way to
accomplish the goal by using cloud-native monitoring services?
