CV0-004 CompTIA Cloud+ (2025) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA CV0-004 CompTIA Cloud+ (2025) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A developer is building a new application version using a CI/CD pipeline. The developer receives the following error message log when the build fails:
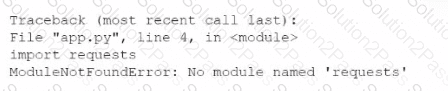
Which of the following is the most likely cause of this failure?
A cloud administrator recently created three servers in the cloud. The goal was to create ACLs so the servers could not communicate with each other. The servers were configured
with the following IP addresses:
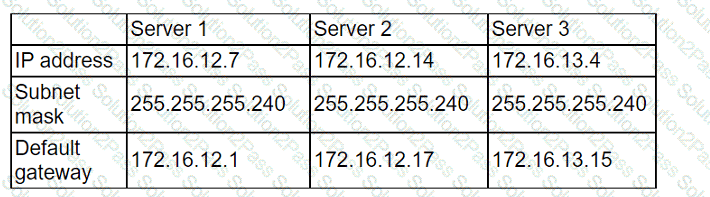
After implementing the ACLs, the administrator confirmed that some servers are still able to reach the other servers. Which of the following should the administrator change to
prevent the servers from being on the same network?
A company has decided to adopt a microservices architecture for its applications that are deployed to the cloud. Which of the following is a major advantage of this type of architecture?
Which of the following industry standards mentions that credit card data must not be exchanged or stored in cleartext?
A systems administrator is provisioning VMs according to the following requirements:
· A VM instance needs to be present in at least two data centers.
. During replication, the application hosted on the VM tolerates a maximum latency of one second.
· When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?
A high-usage cloud resource needs to be monitored in real time on specific events to guarantee its availability. Which of the following actions should be used to meet this requirement?
A cloud infrastructure administrator updated the IP tables to block incoming connections and outgoing responses to 104.225.110.203. Which of the following vulnerability management steps is this an example of?
During project initiation, a project manager needs to identify goals and deliverables that should be completed by the end of the project and also meet certain cost and time factors. Which of the following would best align with these needs?
A project manager is reviewing quality planning techniques. Which of the following involves comparing results of similar activities?
A cloud engineer is provisioning a new application that requires access to the organization's public cloud resources. Which of the following is the best way for the cloud engineer to authenticate the application?
Which of the following refers to the idea that data should stay within certain borders or territories?
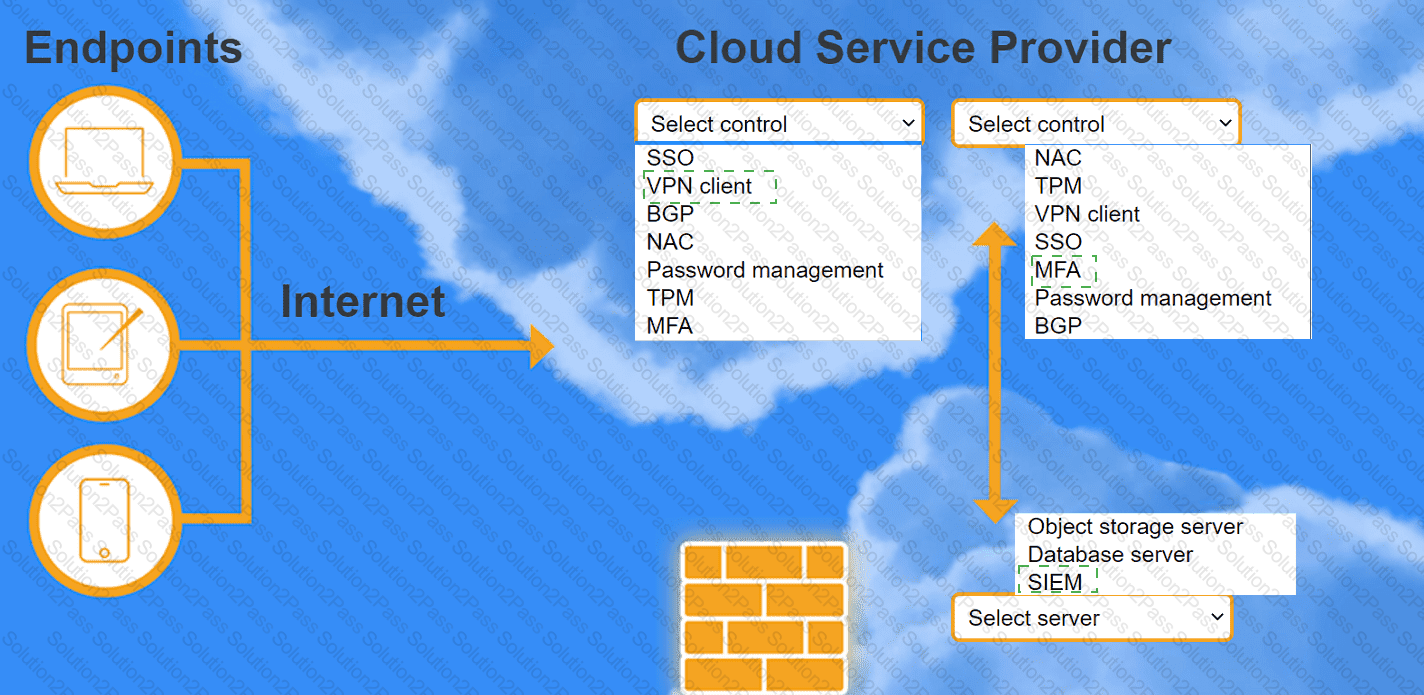
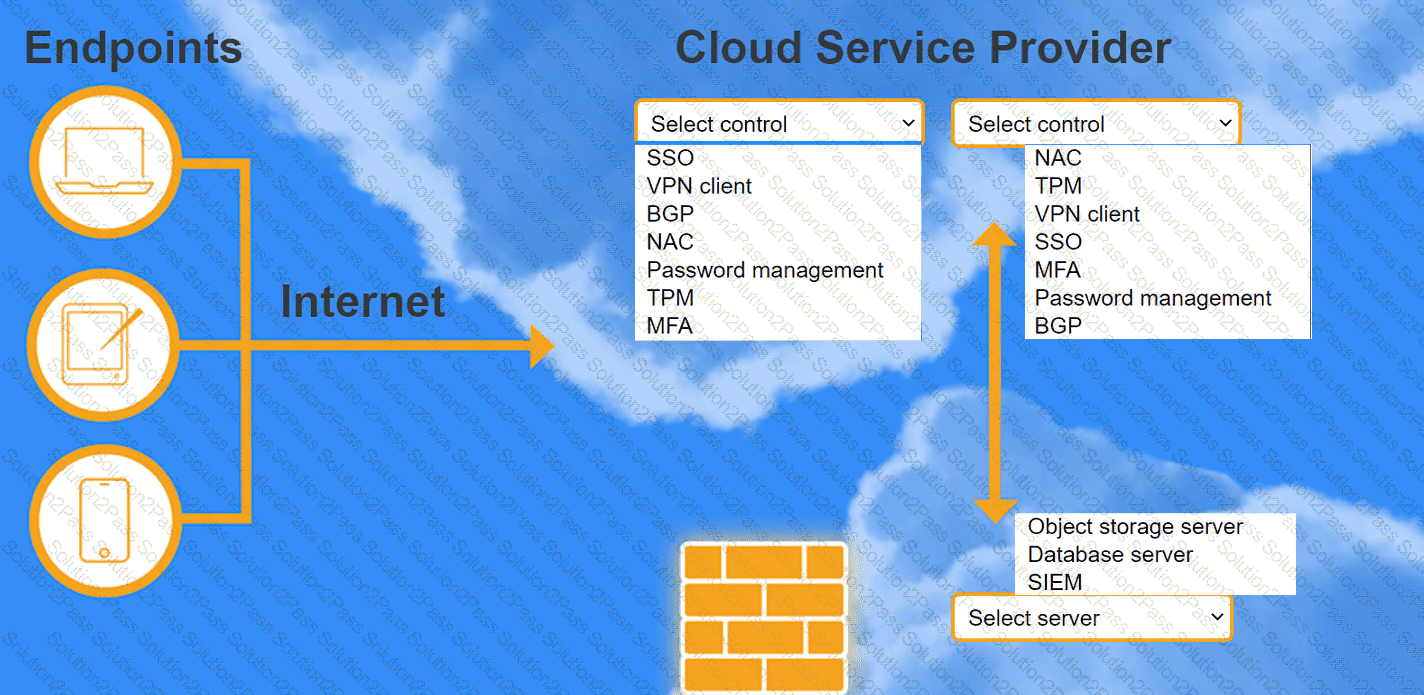
A highly regulated business is required to work remotely, and the risk tolerance is very low. You are tasked with providing an identity solution to the company cloud that includes the following:
secure connectivity that minimizes user login
tracks user activity and monitors for anomalous activity
requires secondary authentication
INSTRUCTIONS
Select controls and servers for the proper control points.
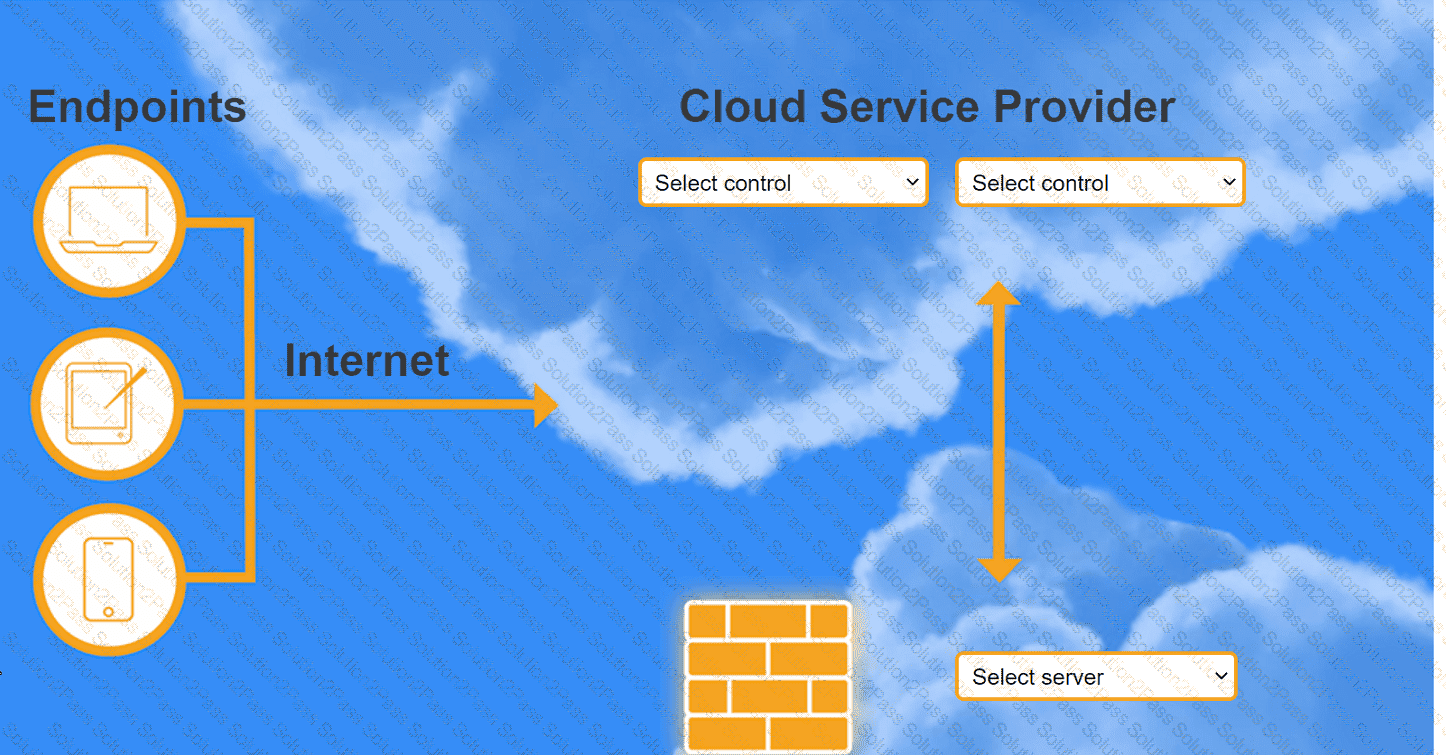
A company recently migrated to a public cloud provider. The company's computer incident response team needs to configure native cloud services tor detailed logging. Which of the following should the team implement on each cloud service to support root cause analysis of past events? {Select two).
A software engineer needs to transfer data over the internet using programmatic access while also being able to query the data. Which of the following will best help the engineer to complete this task?
Servers in the hot site are clustered with the main site.
A cloud administrator needs to distribute workloads across remote data centers for redundancy reasons. Which of the following deployment strategies would eliminate downtime, accelerate deployment, and remain cost efficient?
A log-parsing application requires significant processing power to ingest the logs streaming from web servers. The engineering team presents the cloud architect with four proposals
using the same underlying hardware. Which of the following should the cloud architect select in order to minimize the impact of an instance failure while keeping the cost as low as
possible?
A cloud networking engineer is troubleshooting the corporate office's network configuration. Employees in the IT and operations departments are unable to resolve IP addresses on all devices, and the IT department cannot establish a connection to other departments' subnets. The engineer identifies the following configuration currently in place to support the office network:
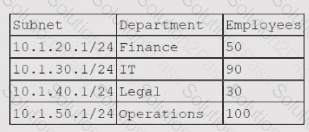
Each employee needs to connect to the network with a maximum of three hosts. Each subnet must be segregated, but the IT department must have the ability to communicate with all subnets. Which of the following meet the IP addressing and routing requirements? (Select two).
A security team recently hired multiple interns who all need the same level of access. Which of the following controls should the security team implement to provide access to the
cloud environment with the least amount of overhead?
The PMO wants to streamline the routing and approval of project activities to provide up-to-date visibility of the status. Which of the following collaboration tools would be most appropriate to use?