XK0-006 CompTIA Linux+ V8 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your CompTIA XK0-006 CompTIA Linux+ V8 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A systems administrator receives reports about connection issues to a secure web server. Given the following firewall and web server outputs:
Firewall output:
Status: active
To Action From
443/tcp DENY Anywhere
443/tcp (v6) DENY Anywhere (v6)
Web server output:
tcp LISTEN 0 4096 *:443 :
Which of the following commands best resolves this issue?
Users report that a Linux system is unresponsive and simple commands take too long to complete. The Linux administrator logs in to the system and sees the following: Output 1:
10:06:29 up 235 day, 19:23, 2 users, load average: 8.71, 8.24, 7.71
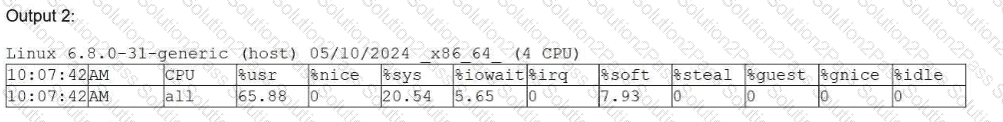
Which of the following is the system experiencing?
An administrator logs in to a Linux server and notices the clock is 37 minutes fast. Which of the following commands will fix the issue?
Which of the following is the main reason for setting up password expiry policies?
While hardening a system, an administrator runs a port scan with Nmap, which returned the following output:
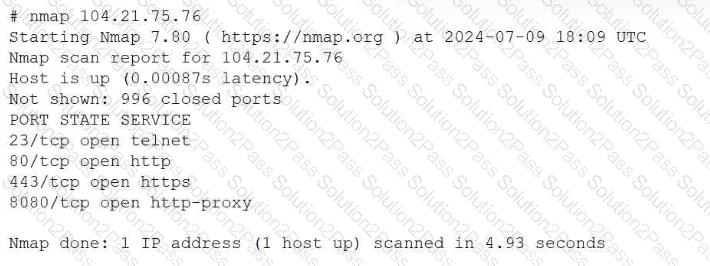
Which of the following is the best way to address this security issue?
An administrator wants to search a file named myFile and look for all occurrences of strings containing at least five characters, where characters two and five are i, but character three is not b. Which of the following commands should the administrator execute to get the intended result?
A systems administrator receives reports from users who are having issues while trying to modify newly created files in a shared directory. The administrator sees the following outputs:
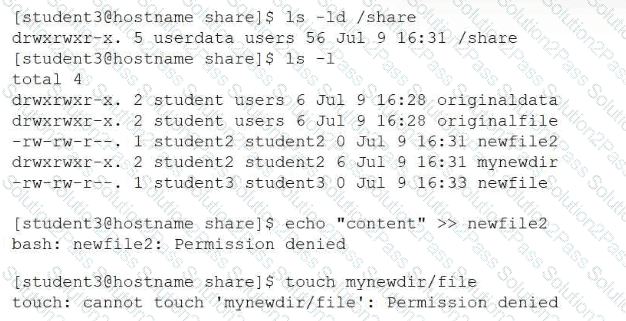
Which of the following provides the best resolution to this issue?
A Linux administrator needs to analyze a compromised disk for traces of malware. To complete the analysis, the administrator wants to make an exact, block-level copy of the disk. Which of the following commands accomplishes this task?
A Linux user needs to download the latest Debian image from a Docker repository. Which of the following commands makes this task possible?
Which of the following commands should an administrator use to see a full hardware inventory of a Linux system?
To perform a live migration, which of the following must match on both host servers? (Choose two)
Which of the following best describes journald?
Which of the following utilities supports the automation of security compliance and vulnerability management?
User1 reports "access denied" errors while trying to execute app. Given the following outputs:
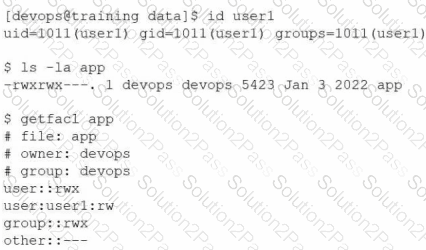
Which of the following options will remediate this issue?
Which of the following passwords is the most complex?
Users cannot access an application that is running inside containers. The administrator wants to validate whether the containers are running. Which of the following commands should the administrator use?
A systems administrator is creating a backup copy of the /home/ directory. Which of the following commands allows the administrator to archive and compress the directory at the same time?
Which of the following is a reason multiple password changes on the same day are not allowed?
A systems administrator is configuring new Linux systems and needs to enable passwordless authentication between two of the servers. Which of the following commands should the administrator use?
A systems administrator needs to set the IP address of a new DNS server. Which of the following files should the administrator modify to complete this task?
