312-38 ECCouncil Certified Network Defender (CND) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-38 Certified Network Defender (CND) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following Layers of IoT Architecture provides dashboards to monitor, analyze, and implement proactive decisions?
David, a network and system admin, encrypted all the files in a Windows system that supports NTFS file system using Encrypted File Systems (EFS). He then backed up the same files into another Windows
system that supports FAT file system. Later, he found that the backup files were not encrypted. What could be the reason for this?
Which of following are benefits of using loT devices in loT-enabled environments? I. loT device car be connected anytime M. loT device can be connected at any place ill. loT devices connected to anything
An organization’s web server was recently compromised triggering its admin team into action to
defend the network. The admin team wants to place the web server in such a way that, even if it is
attacked, the other network resources will be unavailable to the attacker. Moreover, the network
monitoring will easily detect the future attacks. How can the admin team implement this plan?
Which category of suspicious traffic signatures includes SYN flood attempts?
Which of the following connects the SDN application layer and SDN controller and allows communication between the network services and business applications?
Sean has built a site-to-site VPN architecture between the head office and the branch office of his company. When users in the branch office and head office try to communicate with each other, the traffic is
encapsulated. As the traffic passes though the gateway, it is encapsulated again. The header and payload both are encapsulated. This second encapsulation occurs only in the __________implementation of a VPN.
Which of the following is a windows in-built feature that provides filesystem-level encryption in the OS (starting from Windows 2000). except the Home version of Windows?
Identify the network topology where each computer acts as a repeater and the data passes from one computer to the other in a single direction until it reaches the destination.
Which scan attempt can penetrate through a router and a firewall that filter incoming packets with particular flags set and is not supported by Windows?
Which of the following acts as a verifier for the certificate authority?
Henry needs to design a backup strategy for the organization with no service level downtime. Which backup method will he select?
Which of the following Wireshark filters can a network administrator use to view the packets without any flags set in order to detect TCP Null Scan attempts?
Kyle is an IT technician managing 25 workstations and 4 servers. The servers run applications and mostly store confidential data. Kyle must backup the server's data daily to ensure nothing is lost. The power in the
company's office is not always reliable, Kyle needs to make sure the servers do not go down or are without power for too long. Kyle decides to purchase an Uninterruptible Power Supply (UPS) that has a pair of inverters
and converters to charge the battery and provides power when needed. What type of UPS has Kyle purchased?
David is working in a mid-sized IT company. Management asks him to suggest a framework that can be used effectively to align the IT goals to the business goals of the company. David suggests the______framework,
as it provides a set of controls over IT and consolidates them to form a framework.
If Myron, head of network defense at Cyberdyne, wants to change the default password policy settings on the company’s Linux systems, which directory should he access?
An US-based organization decided to implement a RAID storage technology for their data backup plan. John wants to setup a RAID level that require a minimum of six drives but will meet high fault tolerance and with a
high speed for the data read and write operations. What RAID level is John considering to meet this requirement?
Which firewall technology provides the best of both packet filtering and application-based filtering and is used in Cisco Adaptive Security Appliances?
John has planned to update all Linux workstations in his network. The organization is using various Linux distributions including Red hat, Fedora and Debian. Which of following commands will he use to
update each respective Linux distribution?
XX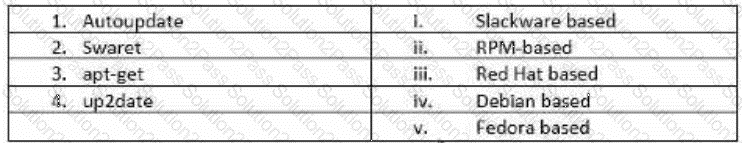
Which wireless networking topology setup requires same channel name and SSID?
