312-50v13 ECCouncil Certified Ethical Hacker Exam (CEHv13) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50v13 Certified Ethical Hacker Exam (CEHv13) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which type of sniffing technique is generally referred as MiTM attack?
Your organization has signed an agreement with a web hosting provider that requires you to take full responsibility for the maintenance of the cloud-based resources. Which of the following models covers this?
What type of a vulnerability/attack is it when the malicious person forces the user’s browser to send an authenticated request to a server?
Shiela is an information security analyst working at HiTech Security Solutions. She is performing service version discovery using Nmap to obtain information about the running services and their versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the target host?
What is the algorithm used by LM for Windows 2000 SAM?
You are logged in as a local admin on a Windows 7 system and you need to launch the Computer Management Console from command line.
Which command would you use?
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm’s public-facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
HTTP/1.1 200 OK
Server: Microsoft-IIS/6
...
Which of the following is an example of what the engineer performed?
User A is writing a sensitive email message to user B outside the local network. User A has chosen to use PKI to secure his message and ensure only user B can read the sensitive email. At what layer of the OSI layer does the encryption and decryption of the message take place?
One of your team members has asked you to analyze the following SOA record.
What is the TTL?
Rutgers.edu. SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
A cybersecurity research team identifies suspicious behavior on a user’s Android device. Upon investigation, they discover that a seemingly harmless app, downloaded from a third-party app store, has silently overwritten several legitimate applications such as WhatsApp and SHAREit. These fake replicas maintain the original icon and user interface but serve intrusive advertisements and covertly harvest credentials and personal data in the background. The attackers achieved this by embedding malicious code in utility apps like video editors and photo filters, which users were tricked into installing. The replacement occurred without user consent, and the malicious code communicates with a command-and-control (C&C) server to execute further instructions. What type of attack is being carried out in this scenario?
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of these switches.
If these switches' ARP cache is successfully flooded, what will be the result?
A serverless application was compromised through an insecure third-party API used by a function. What is the most effective countermeasure?
A penetration tester evaluates a secure web application using HTTPS, secure cookies, and multi-factor authentication. To hijack a legitimate user’s session without triggering alerts, which technique should be used?
Let's imagine three companies (A, B, and C), all competing in a challenging global environment.
Company A and B are working together in developing a product that will generate a major competitive advantage for them.
Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing.
With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B.
How do you prevent DNS spoofing?
Jude, a pen tester, examined a network from a hacker's perspective to identify exploits and vulnerabilities accessible to the outside world by using devices such as firewalls, routers, and servers. In this process, he also estimated the threat of network security attacks and determined the level of security of the corporate network.
What is the type of vulnerability assessment that Jude performed on the organization?
A company’s customer data in a cloud environment has been exposed due to an unknown vulnerability. Which type of issue most likely led to the incident?
What would be the fastest way to perform content enumeration on a given web server by using the Gobuster tool?
A sophisticated attacker targets your web server with the intent to execute a Denial of Service (DoS) attack. His strategy involves a unique mixture of TCP SYN, UDP, and ICMP floods, using 'r' packets per second. Your server, reinforced with advanced security measures, can handle 'h' packets per second before it starts showing signs of strain. If 'r' surpasses 'h', it overwhelms the server, causing it to become unresponsive. In a peculiar pattern, the attacker selects 'r' as a composite number and 'h' as a prime number, making the attack detection more challenging. Considering 'r=2010' and different values for 'h', which of the following scenarios would potentially cause the server to falter?
Maria is conducting passive reconnaissance on a competitor without interacting with their systems. Which method would be least appropriate and potentially risky?
This form of encryption algorithm is asymmetric key block cipher that is characterized by a 128-bit block size, and its key size can be up to 256 bits. Which among the following is this encryption algorithm?
Which advanced session-hijacking technique is hardest to detect and mitigate?
What hacking attack is challenge/response authentication used to prevent?
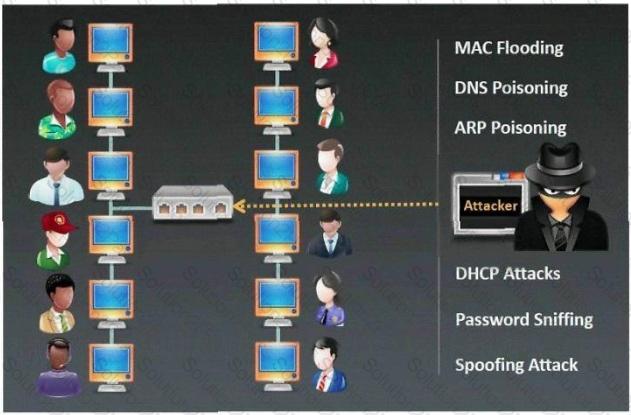
In a large organization, a network security analyst discovered a series of packet captures that seem unusual.
The network operates on a switched Ethernet environment. The security team suspects that an attacker might
be using a sniffer tool. Which technique could the attacker be using to successfully carry out this attack,
considering the switched nature of the network?
Which among the following is the best example of the hacking concept called "clearing tracks"?
An ethical hacker is testing the security of a website's database system against SQL Injection attacks. They discover that the IDS has a strong signature detection mechanism to detect typical SQL injection patterns.
Which evasion technique can be most effectively used to bypass the IDS signature detection while performing a SQL Injection attack?
Infected systems receive external instructions over HTTP and DNS, with fileless payloads modifying system components. What is the most effective action to detect and disrupt this malware?
A company’s Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?
What is the purpose of a demilitarized zone on a network?
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bab denies that he had ever sent a mail. What do you want to ““know”” to prove yourself that it was Bob who had send a mail?
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network’s external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file.
What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
A penetration tester is evaluating the security of a mobile application and discovers that it lacks proper input validation. The tester suspects that the application is vulnerable to a malicious code injection attack. What is the most effective way to confirm and exploit this vulnerability?
A penetration tester runs a vulnerability scan and identifies an outdated version of a web application running on the company’s server. The scan flags this as a medium-risk vulnerability. What is the best next step for the tester?
What is the following command used for?
net use \target\ipc$ "" /u:""
During a cryptographic audit of a legacy system, a security analyst observes that an outdated block cipher is leaking key-related information when analyzing large sets of plaintext–ciphertext pairs. What approach might an attacker exploit here?
Which of the following is assured by the use of a hash?
An attacker scans a host with the below command. Which three flags are set?
# nmap -sX host.domain.com
Working as an Information Security Analyst, you are creating training material on session hijacking. Which scenario best describes a side jacking attack?
A penetration tester is assessing the security of a corporate wireless network that uses WPA2-Enterprise encryption with RADIUS authentication. The tester wants to perform a man-in-the-middle attack by tricking wireless clients into connecting to a rogue access point. What is the most effective method to achieve this?
An attacker utilizes a Wi-Fi Pineapple to run an access point with a legitimate-looking SSID for a nearby business in order to capture the wireless password. What kind of attack is this?
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
