312-50v13 ECCouncil Certified Ethical Hacker Exam (CEHv13) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your ECCouncil 312-50v13 Certified Ethical Hacker Exam (CEHv13) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is the BEST alternative if you discover that a rootkit has been installed on one of your computers?
ViruXine.W32 virus hides its presence by changing the underlying executable code. This virus code mutates while keeping the original algorithm intact — the code changes itself each time it runs, but the function of the code (its semantics) does not change at all.
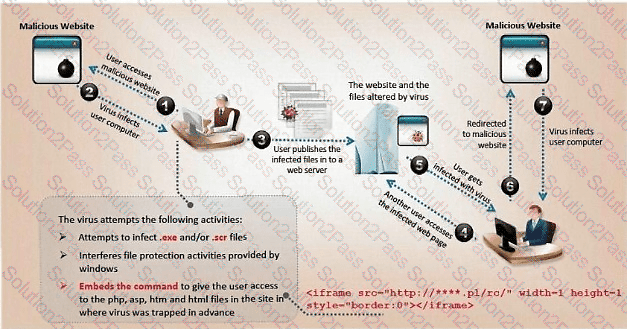
Here is a section of the virus code (refer to image), where the loop performs XOR encryption and changes the way the code looks every time it is executed.
What is this technique called?
Your company suspects a potential security breach and has hired you as a Certified Ethical Hacker to investigate. You discover evidence of footprinting through search engines and advanced Google hacking techniques. The attacker utilized Google search operators to extract sensitive information. You further notice queries that indicate the use of the Google Hacking Database (GHDB) with an emphasis on VPN footprinting.
Which of the following Google advanced search operators would be the LEAST useful in providing the attacker with sensitive VPN-related information?
What type of virus is most likely to remain undetected by antivirus software?
Sarah, a system administrator, was alerted of potential malicious activity on the network of her company. She
discovered a malicious program spread through the instant messenger application used by her team. The
attacker had obtained access to one of her teammate's messenger accounts and started sending files across
the contact list. Which best describes the attack scenario and what measure could have prevented it?
Tremp is an IT Security Manager planning to deploy an IDS. He needs a solution that:
Verifies success/failure of an attack
Monitors system activities
Detects local (host-based) attacks
Provides near real-time detection
Doesn’t require additional hardware
Has a lower entry cost
Which type of IDS is best suited for Tremp’s requirements?
Peter, a system administrator working at a reputed IT firm, decided to work from his home and login remotely. Later, he anticipated that the remote connection could be exposed to session hijacking. To curb this possibility, he implemented a technique that creates a safe and encrypted tunnel over a public network to securely send and receive sensitive information and prevent hackers from decrypting the data flow between the endpoints.
What is the technique followed by Peter to send files securely through a remote connection?
Which social engineering attack involves impersonating a co-worker or authority figure to extract confidential information?
Attacker Steve targeted an organization's network with the aim of redirecting the company's web traffic to another malicious website. To achieve this goal, Steve performed DNS cache poisoning by exploiting the vulnerabilities In the DNS server software and modified the original IP address of the target website to that of a fake website. What is the technique employed by Steve to gather information for identity theft?
During a penetration test, you perform extensive DNS interrogation to gather intelligence about a target organization. Considering the inherent limitations of DNS-based reconnaissance, which of the following pieces of information cannot be directly obtained through DNS interrogation?
Which of the following allows attackers to draw a map or outline the target organization's network infrastructure to know about the actual environment that they are going to hack.
By using a smart card and pin, you are using a two-factor authentication that satisfies
A future-focused security audit discusses risks where attackers collect encrypted data now, anticipating that they can decrypt it later with quantum computers. What is this threat known as?
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
Calvin, a software developer, uses a feature that helps him auto-generate the content of a web page without manual involvement and is integrated with SSI directives. This leads to a vulnerability in the developed web application as this feature accepts remote user inputs and uses them on the page. Hackers can exploit this feature and pass malicious SSI directives as input values to perform malicious activities such as modifying and erasing server files. What is the type of injection attack Calvin's web application is susceptible to?
A pen tester is configuring a Windows laptop for a test. In setting up Wireshark, what driver and library are required to allow the NIC to work in promiscuous mode?
An attacker has partial root access to a mobile application. What control best prevents further exploitation?
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist’s email, and you send her an email changing the source email to her boss’s email (boss@company). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don’t work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network. What testing method did you use?
An attacker performs DNS cache snooping using the dig command with the +norecurse flag against a known DNS server. The server returns NOERROR but provides no answer to the query. What does this most likely suggest?
A penetration tester suspects that the web application's "Order History" page is vulnerable to SQL injection because it displays user orders based on an unprotected user ID parameter in the URL. What is the most appropriate approach to test this?
Why should the security analyst disable/remove unnecessary ISAPI filters?
env x='(){ :;};echo exploit' bash –c 'cat /etc/passwd'
What is the Shellshock bash vulnerability attempting to do on a vulnerable Linux host?
A penetration tester is tasked with assessing the security of a smart home IoT device that communicates with a mobile app over an unencrypted connection. The tester wants to intercept the communication and extract sensitive information. What is the most effective approach to exploit this vulnerability?
You are investigating unauthorized access to a web application using token-based authentication. Tokens expire after 30 minutes. Server logs show multiple failed login attempts using expired tokens within a short window, followed by successful access with a valid token. What is the most likely attack scenario?
During a security evaluation of a smart agriculture setup, an analyst investigates a cloud-managed irrigation controller. The device is found to transmit operational commands and receive firmware updates over unencrypted HTTP. Additionally, it lacks mechanisms to verify the integrity or authenticity of those updates. This vulnerability could allow an adversary to intercept communications or inject malicious firmware, leading to unauthorized control over the device's behavior or denial of essential functionality. Which IoT threat category does this situation best illustrate?
Harry. a professional hacker, targets the IT infrastructure of an organization. After preparing for the attack, he attempts to enter the target network using techniques such as sending spear-phishing emails and exploiting vulnerabilities on publicly available servers. Using these techniques, he successfully deployed malware on the target system to establish an outbound connection. What is the APT lifecycle phase that Harry is currently executing?
What is the proper response for a NULL scan if the port is closed?
During an investigation, an ethical hacker discovers that a web application’s API has been compromised, leading to unauthorized access and data manipulation. The attacker is using webhooks and a webshell. To prevent further exploitation, which of the following actions should be taken?
Dayn, an attacker, wanted to detect if any honeypots are installed in a target network. For this purpose, he used a time-based TCP fingerprinting method to validate the response to a normal computer and the response of a honeypot to a manual SYN request.
Which of the following techniques is employed by Dayn to detect honeypots?
A system analyst wants to implement an encryption solution that allows secure key distribution between communicating parties. Which encryption method should the analyst consider?
A penetration tester evaluates an industrial control system (ICS) that manages critical infrastructure. The tester discovers that the system uses weak default passwords for remote access. What is the most effective method to exploit this vulnerability?
Thomas, a cloud security professional, is performing security assessment on cloud services to identify any loopholes. He detects a vulnerability in a bare-metal cloud server that can enable hackers to implant malicious backdoors in its firmware. He also identified that an installed backdoor can persist even if the server is reallocated to new clients or businesses that use it as an IaaS.
What is the type of cloud attack that can be performed by exploiting the vulnerability discussed in the above scenario?
You need to deploy a new web-based software package for your organization. The package requires three separate servers and needs to be available on the Internet. What is the recommended architecture in terms of server placement?
A penetration tester is conducting an external assessment of a corporate web server. They start by accessing https://www.targetcorp.com/robots.txt and observe multiple Disallow entries that reference directories such as /admin-panel/, /backup/, and /confidentialdocs/. When the tester directly visits these paths via a browser, they find that access is not restricted by authentication and gain access to sensitive files, including server configuration and unprotected credentials. Which stage of the web server attack methodology is demonstrated in this scenario?
Which of the following describes the characteristics of a Boot Sector Virus?
You want to analyze packets on your wireless network. Which program would you use?
Bill has been hired as a penetration tester and cybersecurity auditor for a major credit card company. Which information security standard is most applicable to his role?
As a Certified Ethical Hacker, you are assessing a corporation’s serverless cloud architecture. The organization experienced an attack where a user manipulated a function-as-a-service (FaaS) component to execute malicious commands. The root cause was traced to an insecure third-party API used within a serverless function. What is the most effective countermeasure to strengthen the security posture?
An attacker performs DNS cache snooping using dig +norecurse. The DNS server returns NOERROR but no answer. What does this indicate?
PGP, SSL, and IKE are all examples of which type of cryptography?
