NSE6_SDW_AD-7.6 Fortinet NSE 6 - SD-WAN 7.6 Enterprise Administrator Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE6_SDW_AD-7.6 Fortinet NSE 6 - SD-WAN 7.6 Enterprise Administrator certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
(Refer to the exhibits.
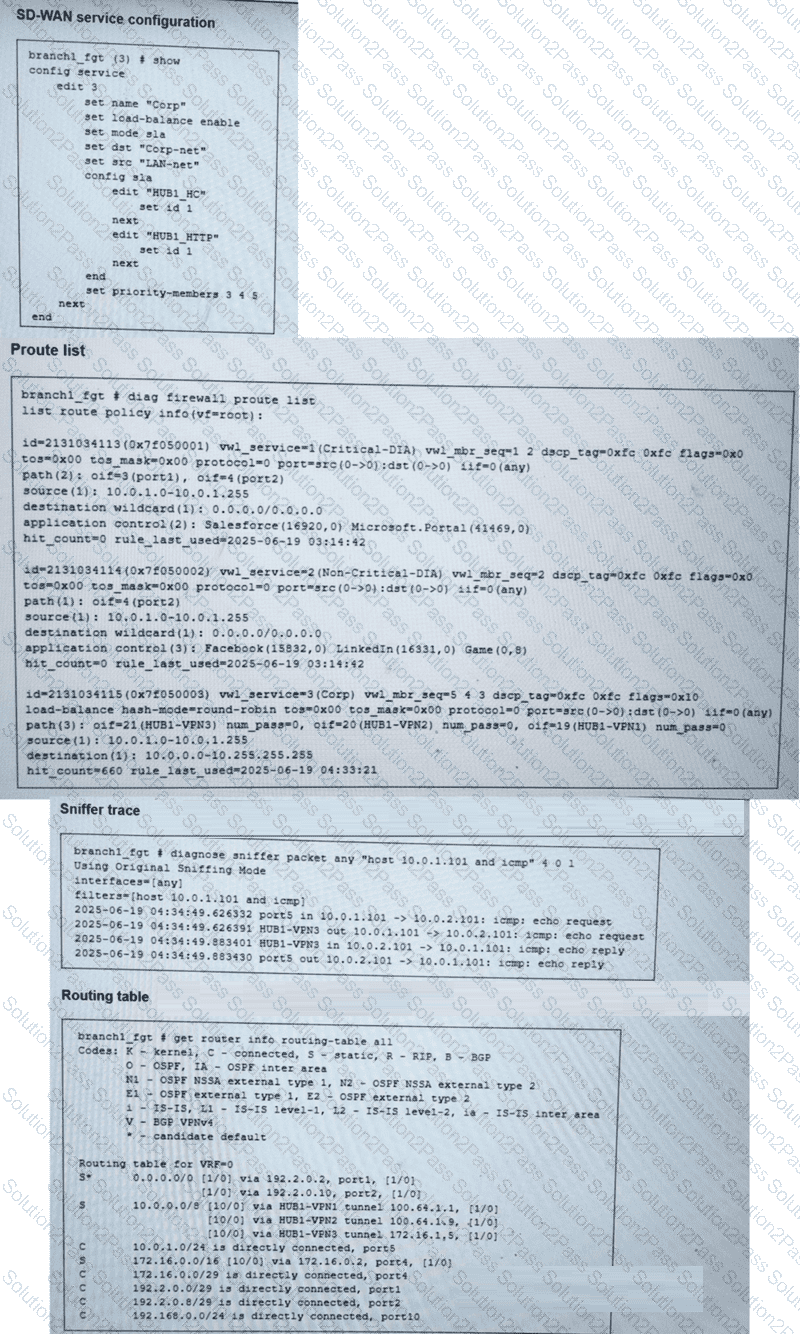
You collected the output shown in the exhibits and want to know which interface HTTP traffic will flow through from the user device 10.0.1.101 to the corporate web server 10.0.0.126. All SD-WAN links are stable.
Which interface will FortiGate use to steer the traffic? Choose one answer.)
Refer to the exhibit.
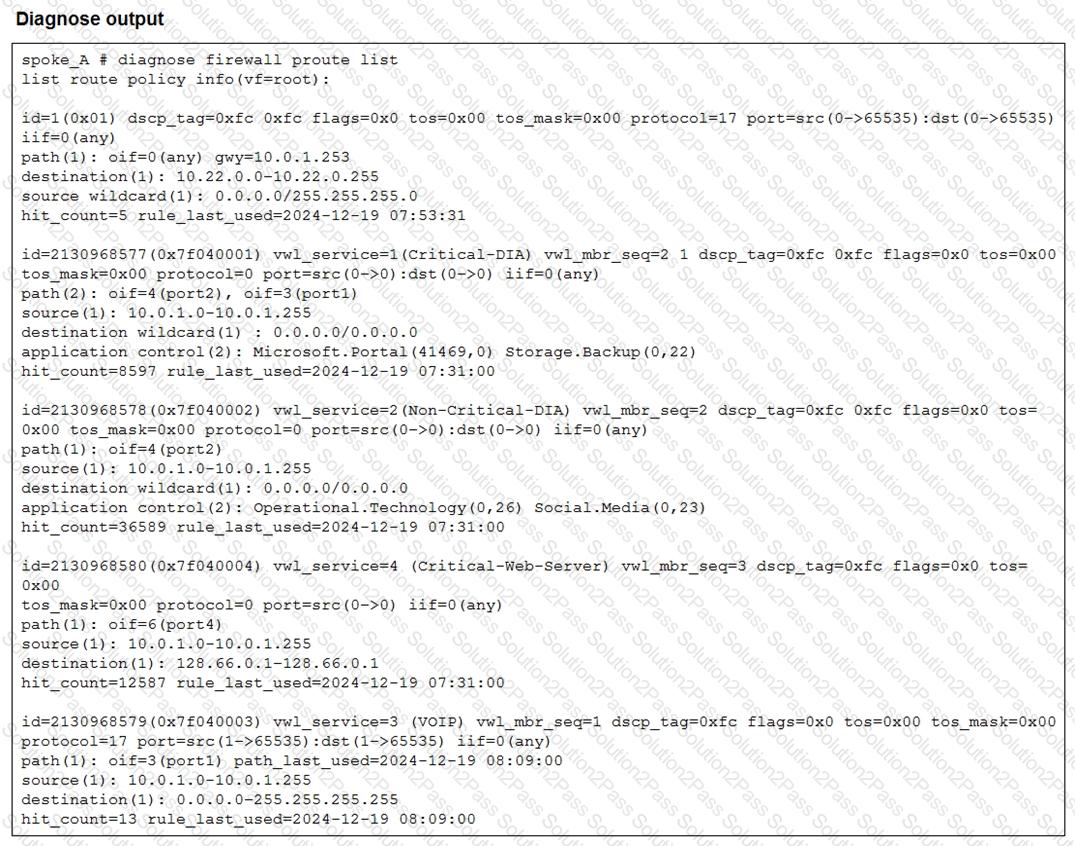
Which two conclusions can you draw from the output shown? (Choose two.)
Which statement describes FortiGate behavior when you reference a zone in a static route?
Refer to the exhibits.
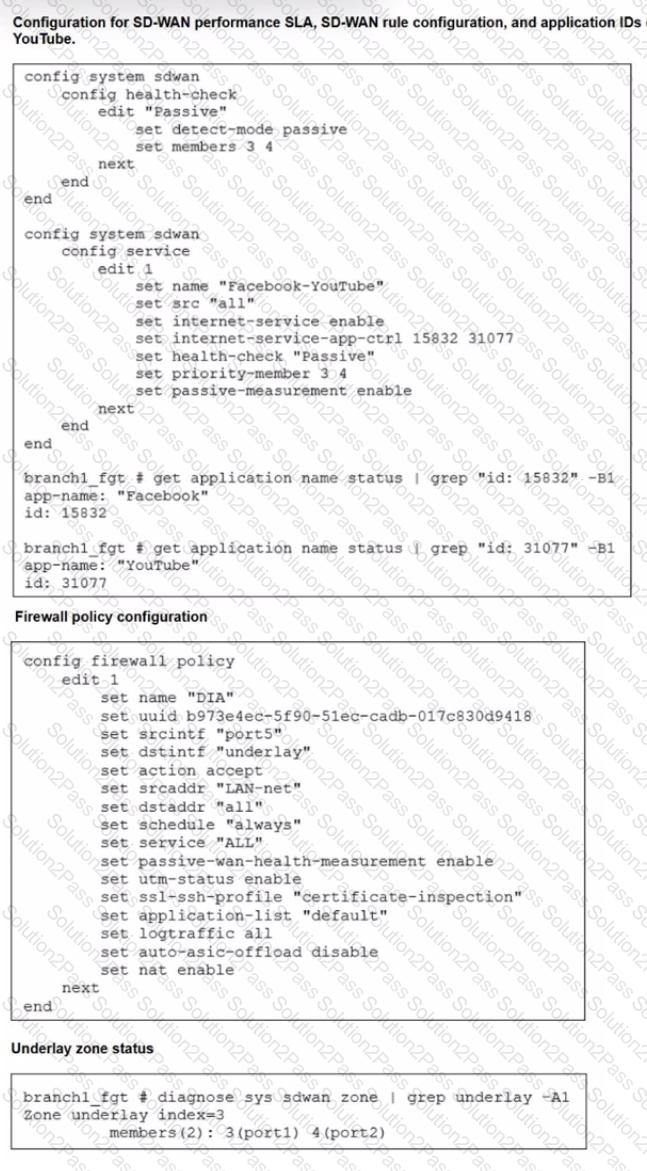
The exhibits show the configuration for SD-WAN performance. SD-WAN rule, the application IDs of Facebook and YouTube along with the firewall policy configuration and the underlay zone status.
Which two statements are true about the health and performance of SD-WAN members 3 and 4? (Choose two.)
Refer to the exhibits.
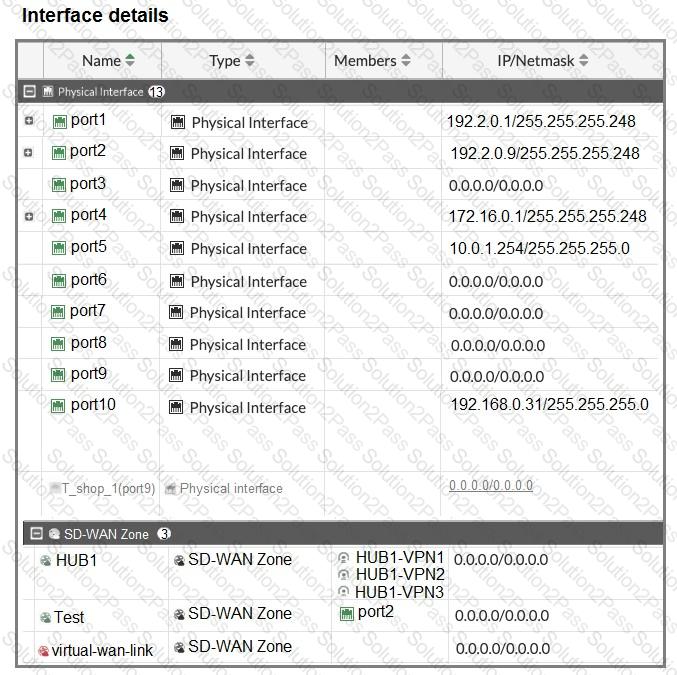
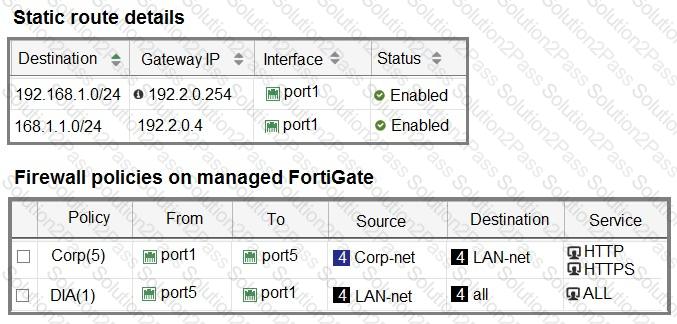
The interface details, static route configuration, and firewall policies on the managed FortiGate device are shown.
You want to configure a new SD-WAN zone, named Underlay, that contains the interfaces port1 and port2.
What must be your first action?
Refer to the exhibit.
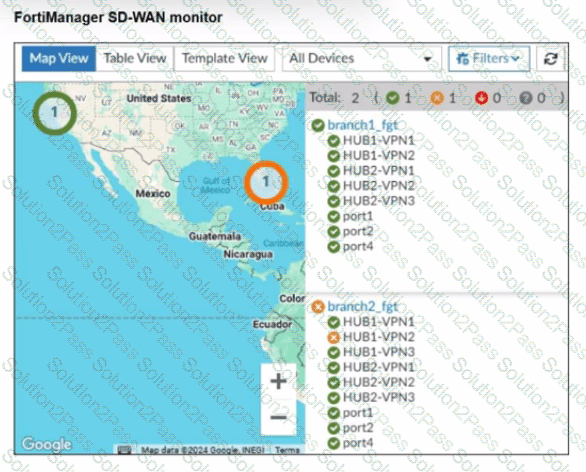
An administrator checks the status of an SD-WAN topology using the FortiManager SD-WAN monitor menus. All members are configured with one or two SLAs.
Which two conclusions can you draw from the output shown? (Choose two.)
As an IT manager for a healthcare company, you want to delegate the installation and management of your SD-WAN deployment to a managed security service provider (MSSP). Each site must maintain direct internet access and ensure that it is secure. You expected significant traffic flow between the sites and want to delegate as much of the network administration and management as possible to the MSSP.
Which two MSSP deployment blueprints best address the customer’s requirements? (Choose two.)
(Which two features must you configure before FortiGate can steer traffic according to SD-WAN rules? Choose two answers.)
Refer to the exhibit.
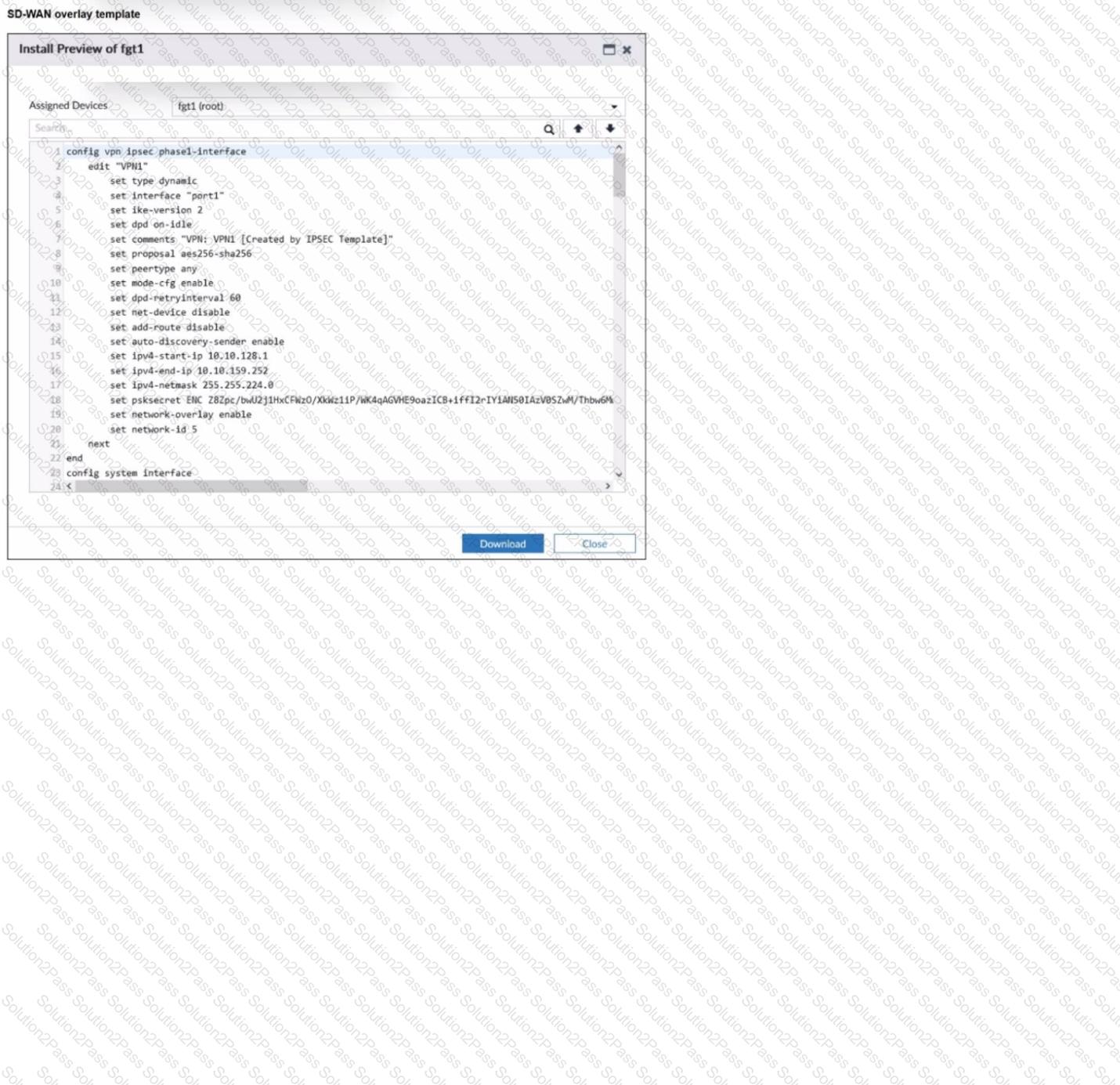
The administrator used the SD-WAN overlay template to prepare an IPsec tunnels configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the FortiManager installation preview for one FortiGate device.
Based on the exhibit, which statement best describes the configuration applied to the FortiGate device?
(Refer to the exhibit.
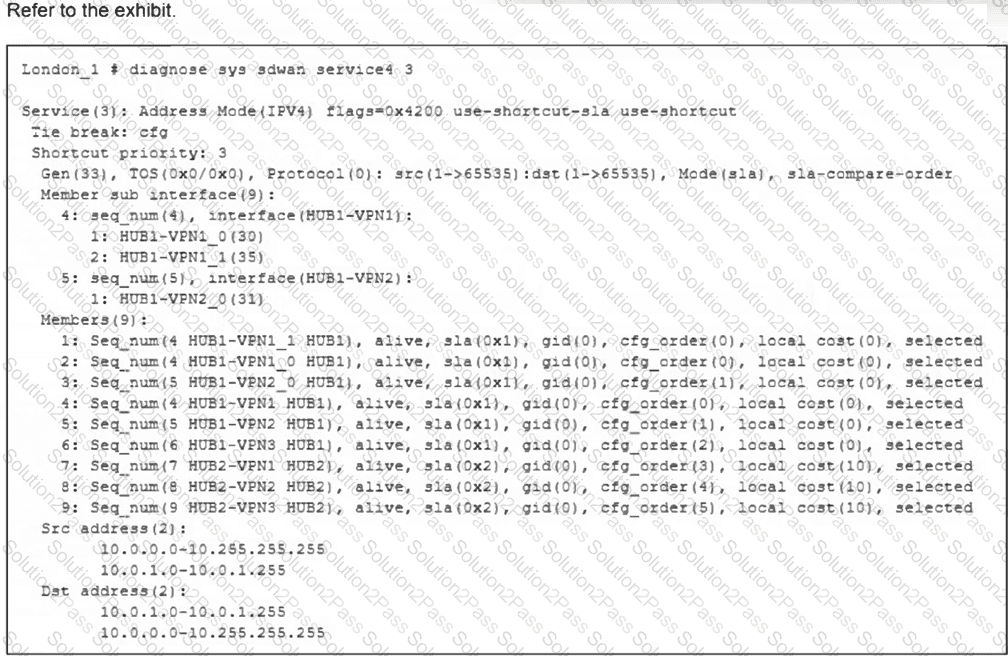
What can you conclude from the output shown? Choose one answer.)
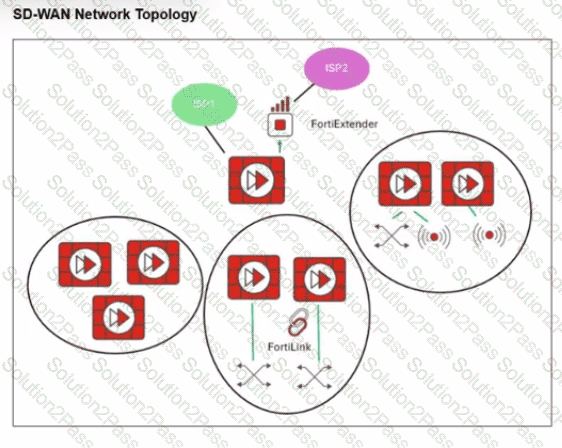
Refer to the exhibit.
You want to configure SD-WAN on a network as shown in the exhibit.
The network contains many FortiGate devices. Some are used as NGFW, and some are installed with extensions such as FortiSwitch. FortiAP. or Forti Ex tender.
What should you consider when planning your deployment?
Which three characteristics apply to provisioning templates available on FortiManager? (Choose three.)
(In which order does FortiGate consider the following elements during the route lookup process? Choose one answer.)
You are planning a new SD-WAN deployment with the following criteria:
- Two regions
- Most of the traffic is expected to remain within its region
- No requirement for inter-region ADVPN
To remain within the recommended best practices, which routing protocol should you select for the overlays?
Refer to the exhibits.
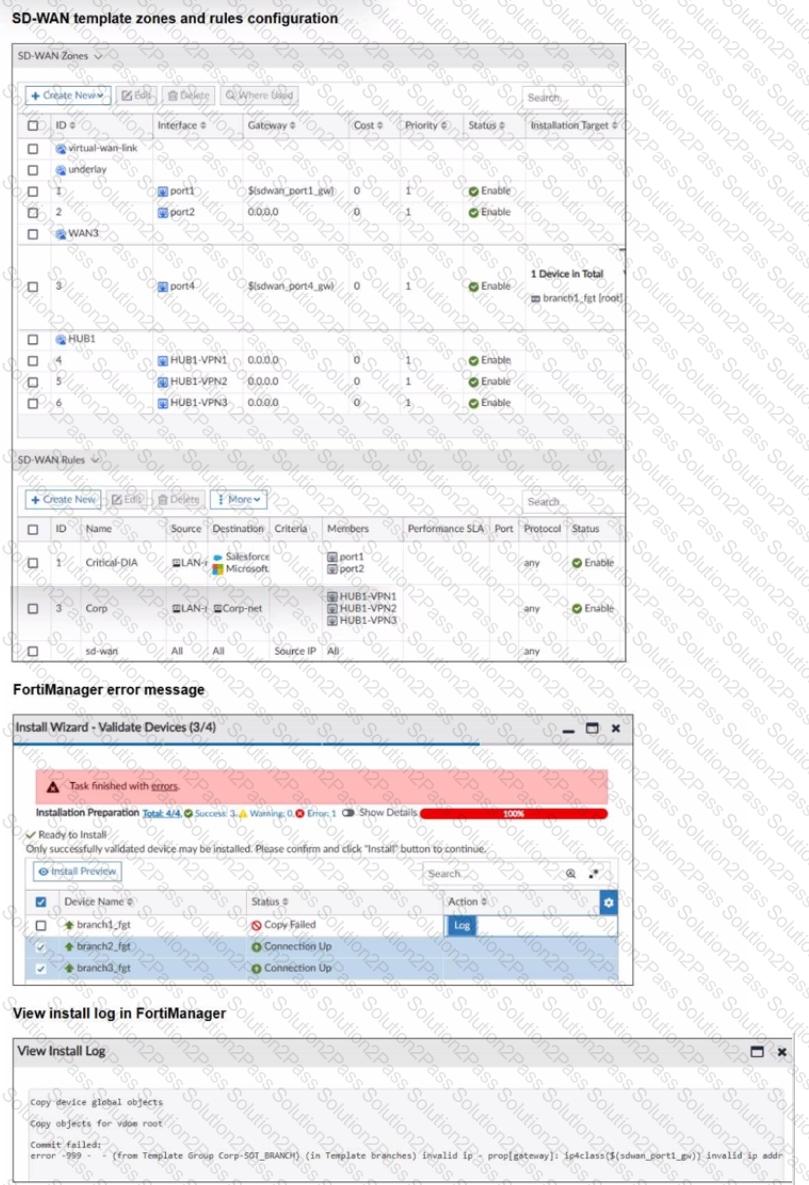
You use FortiManager to configure SD-WAN on three branch devices.
When you install the device settings. FortiManager prompts you with the error "Copy Failed" for the device branch1_fat When you click the log button. FortiManager displays the message shown in the exhibit.
When you use the command diagnose sys session list, how do you identify the sessions that correspond to traffic steered according to SD-WAN rules?
(Refer to the exhibit.
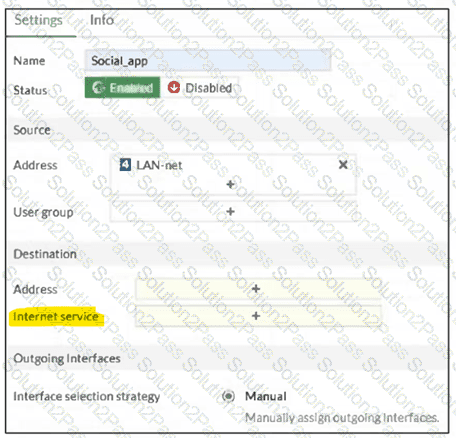
You configure SD-WAN on a standalone FortiGate device.
You want to create an SD-WAN rule that steers traffic related to Facebook and LinkedIn through the less costly internet link.
What must you do to set Facebook and LinkedIn applications as destinations from the GUI? Choose one answer.)
Refer to the exhibit.
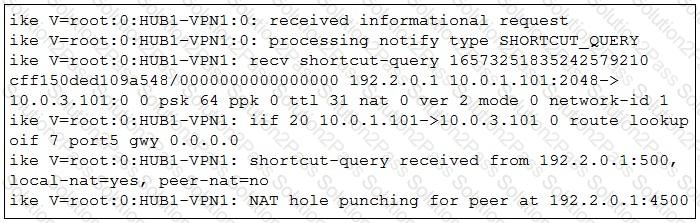
Which statement best describe the role of the ADVPN device in handling traffic?
Refer to the exhibits.
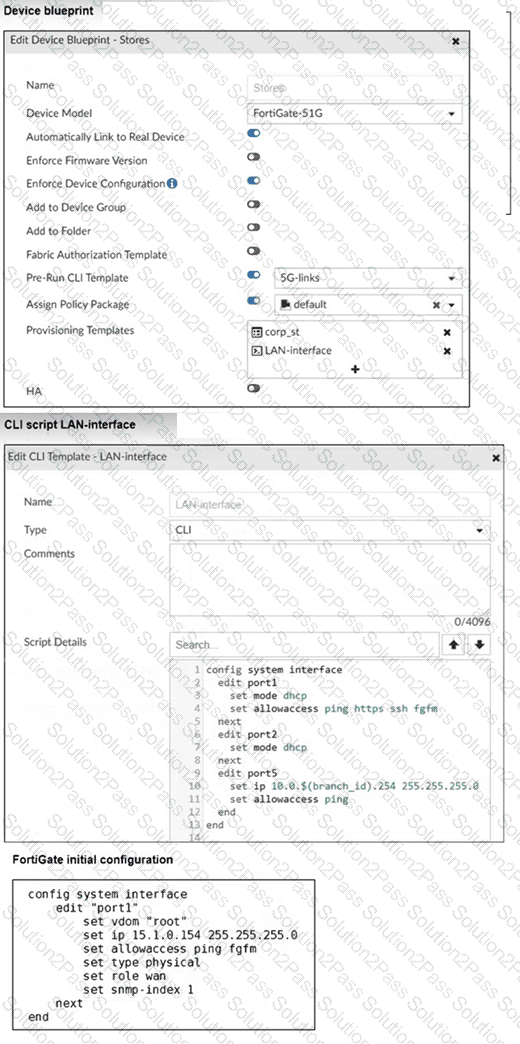
To prepare to onboard FortiGate devices to your company's stores, you configure the device blueprint and CLI scripts shown in the exhibit. Then, a technician prepares a FortiGate 90G with a basic configuration and connects it to the network. The basic configuration contains the port1 configuration and the minimal configuration required to allow the device to connect to FortiManager.
After the device initially connects to FortiManager, FortiManager updates the device configuration.
Based on what is shown in the exhibits, which statement about the actions taken by FortiManager is true?
When a customer delegate the installation and management of its SD-WAN infrastructure to an MSSP, the MSSP usually keeps the hub within its infrastructure for ease of management and to share costly resources.
In which two situations will the MSSP install the hub in customer premises? (Choose two.)
