NSE7_SDW-7.2 Fortinet NSE 7 - SD-WAN 7.2 Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE7_SDW-7.2 Fortinet NSE 7 - SD-WAN 7.2 certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two statements about SLA targets and SD-WAN rules are true? (Choose two.)
What are two benefits of using forward error correction (FEC) in IPsec VPNs? (Choose two.)
Which statement is correct about SD-WAN and ADVPN?
What are two common use cases for remote internet access (RIA)? (Choose two.)
Refer to the exhibits.
Exhibit A
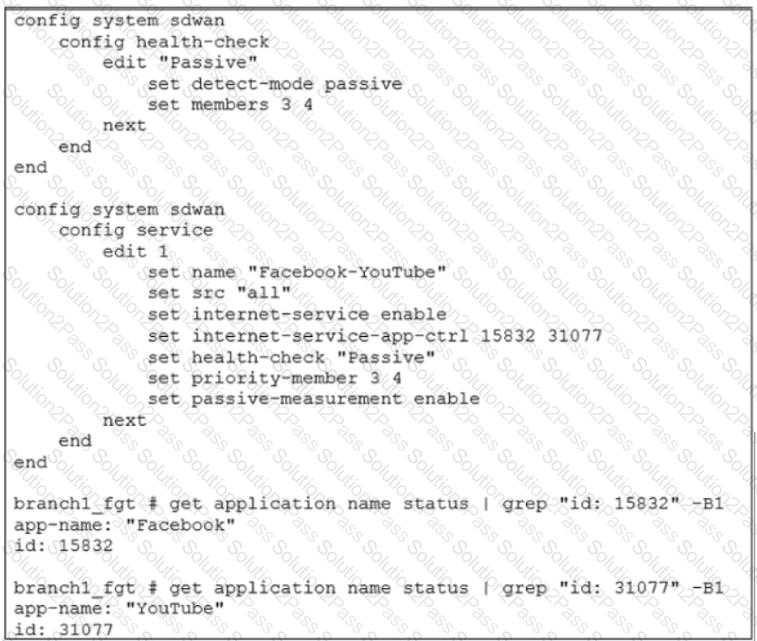
Exhibit B
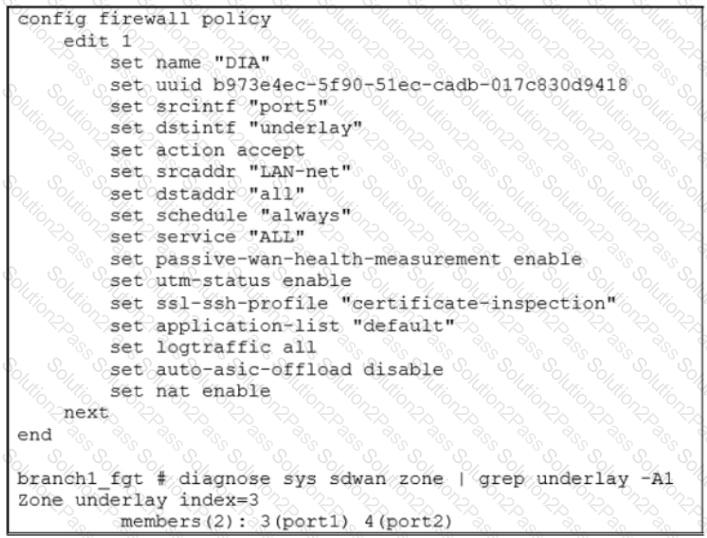
Exhibit A shows the SD-WAN performance SLA configuration, the SD-WAN rule configuration, and the application IDs of Facebook and YouTube. Exhibit B shows the firewall policy configuration and the underlay zone status.
Based on the exhibits, which two statements are correct about the health and performance of port1 and port2? (Choose two.)
Which two statements describe how IPsec phase 1 main mode is different from aggressive mode when performing IKE negotiation? (Choose two )
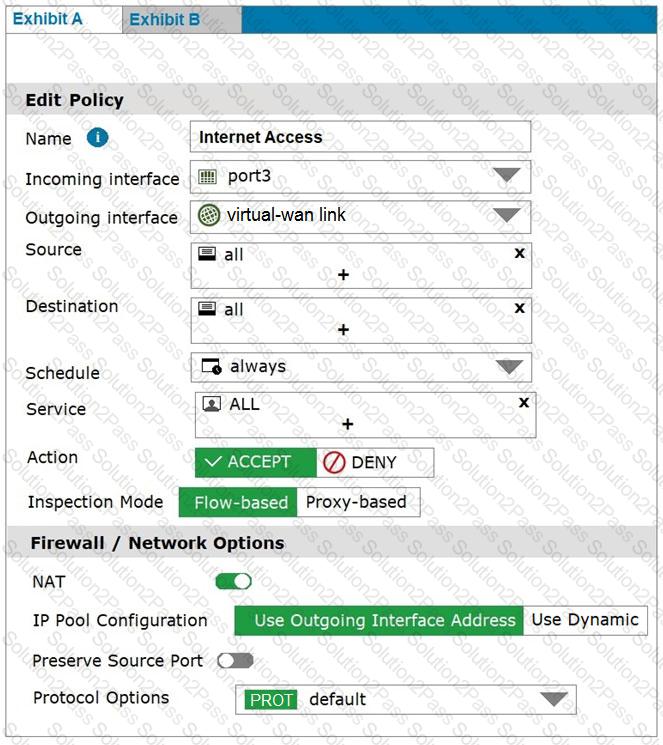
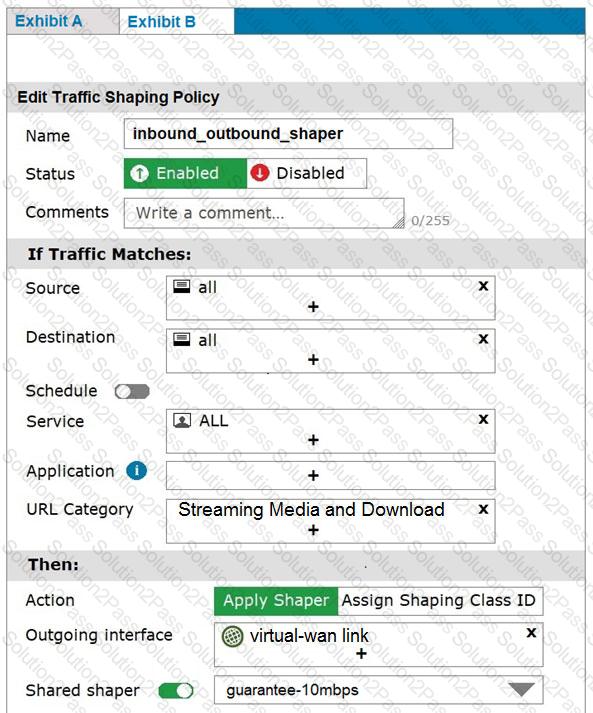
Exhibit A shows the firewall policy and exhibit B shows the traffic shaping policy.
The traffic shaping policy is being applied to all outbound traffic; however, inbound traffic is not being evaluated by the shaping policy.
Based on the exhibits, what configuration change must be made in which policy so that traffic shaping can be applied to inbound traffic?
Which two settings can you configure to speed up routing convergence in BGP? (Choose two.)
Exhibit.
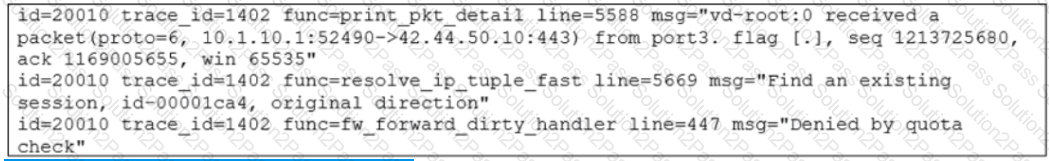
Which conclusion about the packet debug flow output is correct?
Which two tasks are part of using central VPN management? (Choose two.)
Refer to the exhibit.
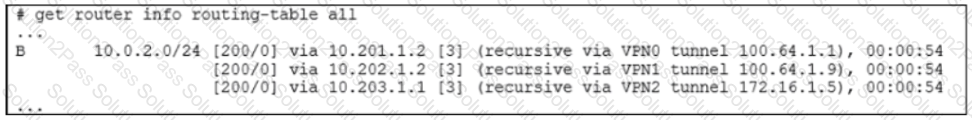
The device exchanges routes using IBGP.
Which two statements are correct about the IBGP configuration and routing information on the device? (Choose two.)
Refer to the exhibit.
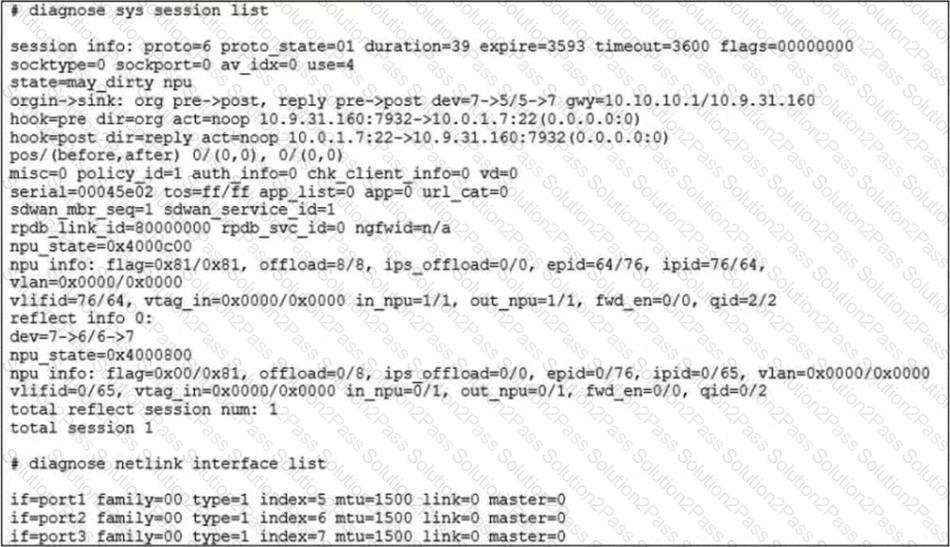
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate appliance that supports hardware offloading. Based on the information shown in the exhibits, which two statements about the session are true? (Choose two.)
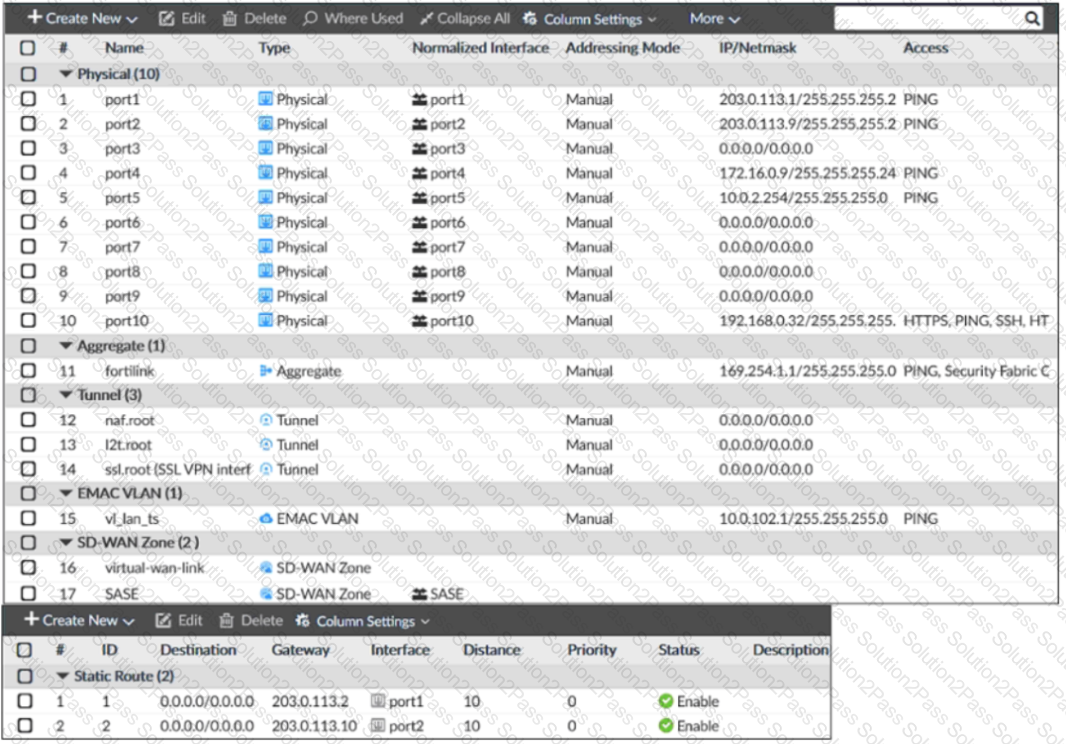
Exhibit B –
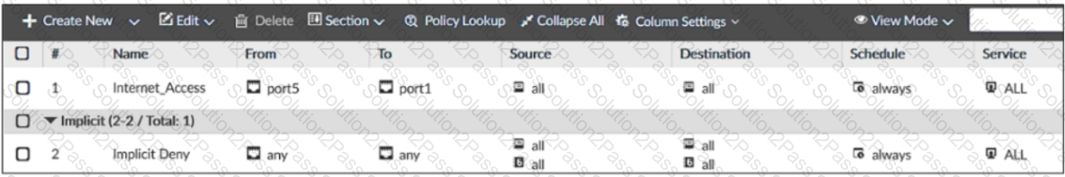
Exhibit A shows the system interface with the static routes and exhibit B shows the firewall policies on the managed FortiGate.
Based on the FortiGate configuration shown in the exhibits, what issue might you encounter when creating an SD-WAN zone for port1 and port2?
Which two statements about SD-WAN central management are true? (Choose two.)
In a hub-and-spoke topology, what are two advantages of enabling ADVPN on the IPsec overlays? (Choose two.)
Refer to the exhibit.
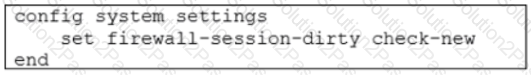
Based on the exhibit, which two actions does FortiGate perform on sessions after a firewall policy change? (Choose two.)
Refer to the exhibit.
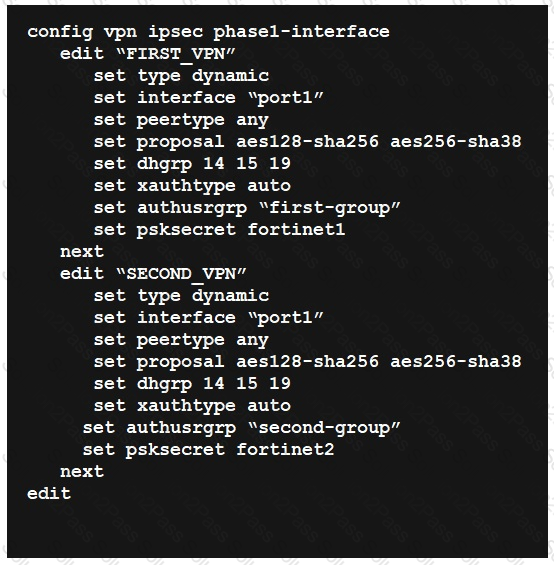
FortiGate has multiple dial-up VPN interfaces incoming on port1 that match only FIRST_VPN.
Which two configuration changes must be made to both IPsec VPN interfaces to allow incoming connections to match all possible IPsec dial-up interfaces? (Choose two.)
Refer to the exhibit.
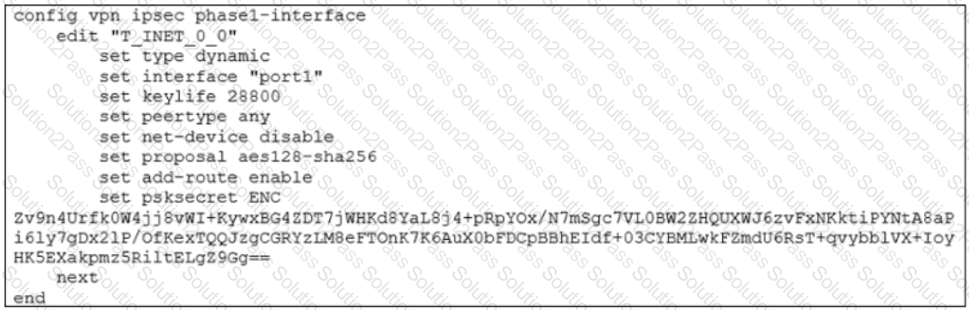
Which configuration change is required if the responder FortiGate uses a dynamic routing protocol to exchange routes over IPsec?
Refer to the exhibit.
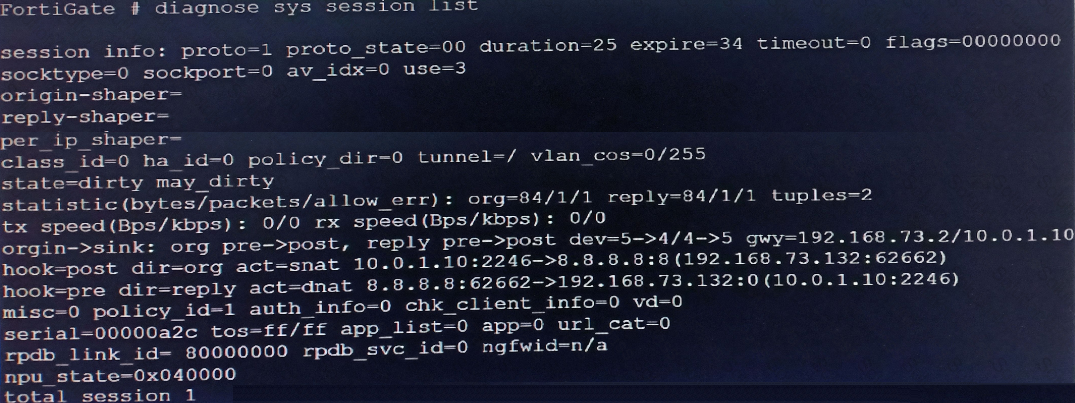
Based on the exhibit, which statement about FortiGate re-evaluating traffic is true?
The SD-WAN overlay template helps to prepare SD-WAN deployments. To complete the tasks performed by the SD-WAN overlay template, the administrator must perform some post-run tasks. What are three mandatory post-run tasks that must be performed? (Choose three.)
