NSE8_812 Fortinet Network Security Expert 8 Written Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE8_812 Network Security Expert 8 Written Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster. Which statement about this solution is true?
Refer to the exhibit.
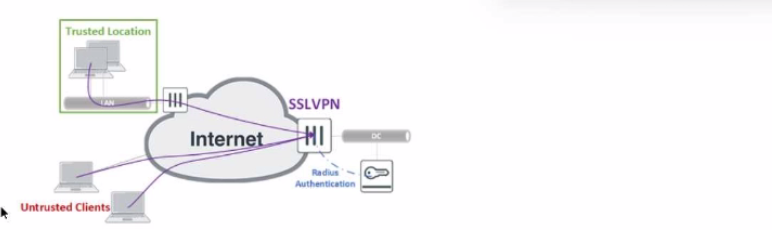
The exhibit shows the topology a customer wants to implement using a flexible authentication scheme. Users connecting from trusted remote locations are authenticated using only their username/password when connecting to the SSLVPN FortiGate in the data center.
When connecting from the Untrusted Clients, users must authenticate using 2-factor authentication.
In this scenario, which RADIUS attribute can be used as a RADIUS policy selector on the FortiAuthenticator to accomplish this goal?
An HA topology is using the following configuration:
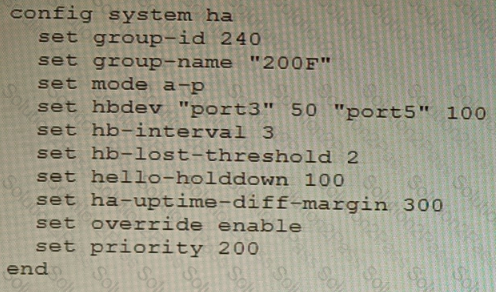
Based on this configuration, how long will it take for a failover to be detected by the secondary cluster member?
Refer to the exhibit showing FortiGate configurations
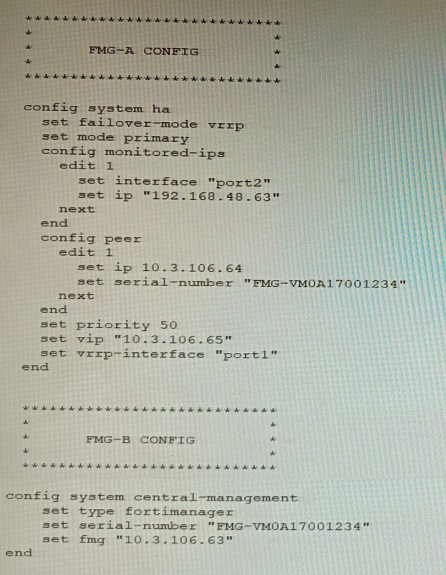
FortiManager VM high availability (HA) is not functioning as expected after being added to an existing deployment.
The administrator finds that VRRP HA mode is selected, but primary and secondary roles are greyed out in the GUI The managed devices never show online when FMG-B becomes primary, but they will show online whenever the FMG-A becomes primary.
What change will correct HA functionality in this scenario?
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP.
What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
You are creating the CLI script to be used on a new SD-WAN deployment You will have branches with a different number of internet connections and want to be sure there is no need to change the Performance SLA configuration in case more connections are added to the branch.
The current configuration is:
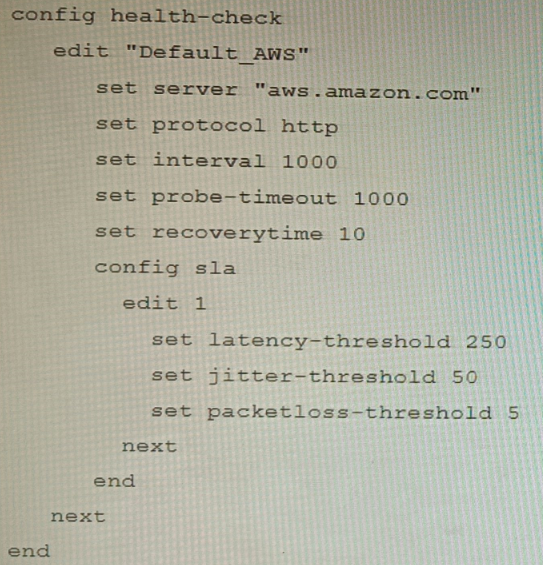
Which configuration do you use for the Performance SLA members?
Refer to the exhibit.
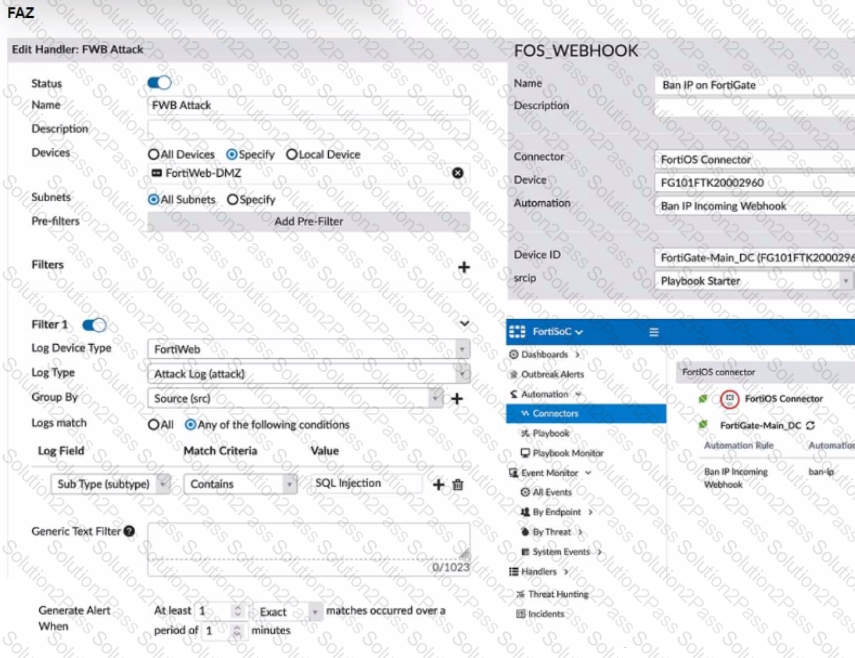
A customer is trying to setup a Playbook automation using a FortiAnalyzer, FortiWeb and FortiGate. The intention is to have the FortiGate quarantine any source of SQL Injection detected by the FortiWeb. They got the automation stitch to trigger on the FortiGate when simulating an attack to their website, but the quarantine object was created with the IP 0.0.0.0. Referring to the configuration and logs in the exhibits, which two statements are true? (Choose two.)
You are deploying a FortiExtender (FEX) on a FortiGate-60F. The FEX will be managed by the FortiGate. You anticipate high utilization. The requirement is to minimize the overhead on the device for WAN traffic.
Which action achieves the requirement in this scenario?
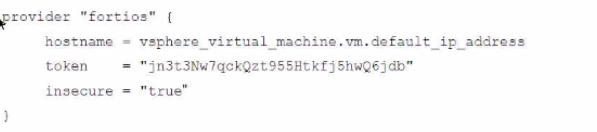
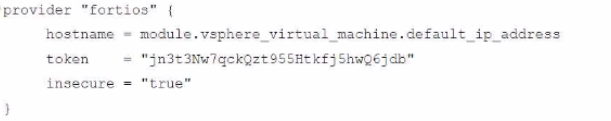
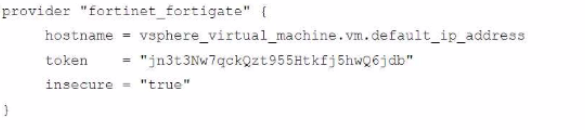
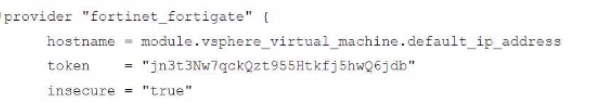
Refer to the exhibit.
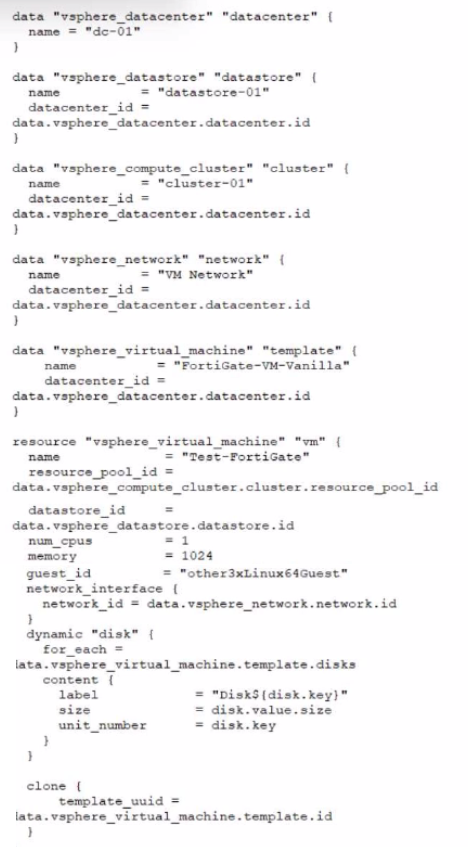
A customer wants to automate the creation and configuration of FortiGate VM instances in a VMware vCenter environment using Terraform. They have the creation part working with the code shown in the exhibit.
Which code snippet will allow Terraform to automatically connect to a newly deployed FortiGate if its IP was dynamically assigned by VMware NSX-T?
Refer to The exhibit showing a FortiEDR configuration.
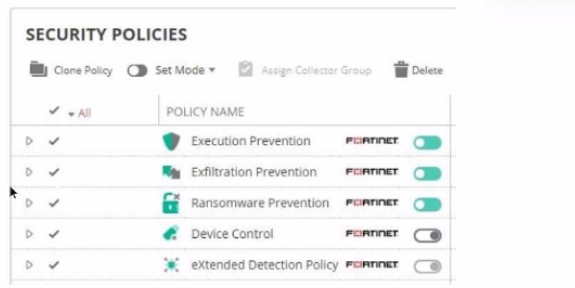
Based on the exhibit, which statement is correct?
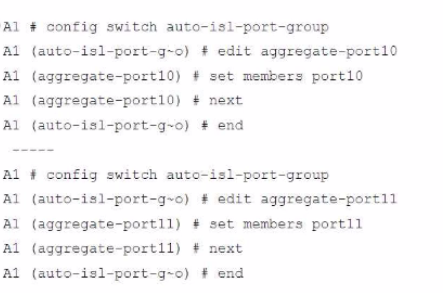
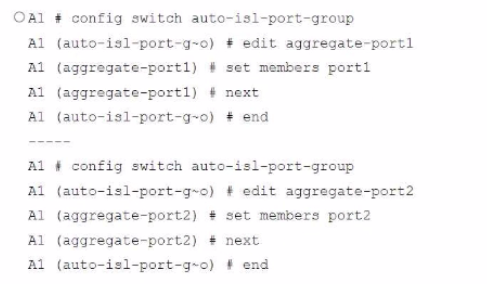
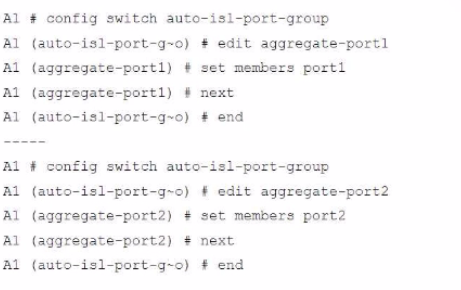
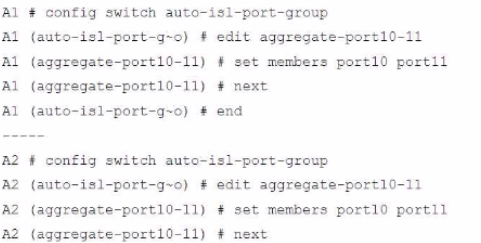
Refer to the exhibit.
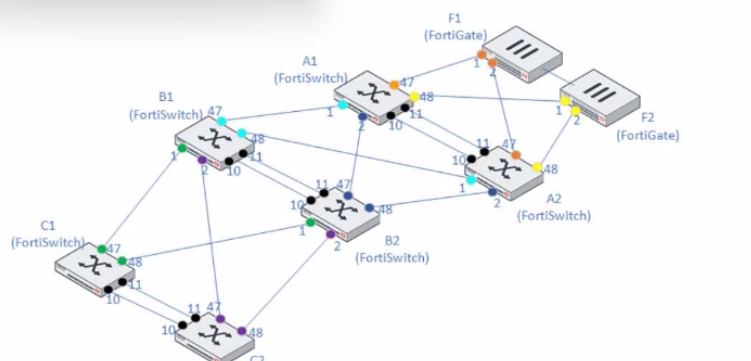
A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?