NSE8_812 Fortinet Network Security Expert 8 Written Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Fortinet NSE8_812 Network Security Expert 8 Written Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
You are designing a setup where the FortiGate device is connected to two upstream ISPs using BGP. Part of the requirement is that you must be able to refresh the route advertisements manually without disconnecting the BGP neighborships.
Which feature must you enable on the BGP neighbors to accomplish this goal?
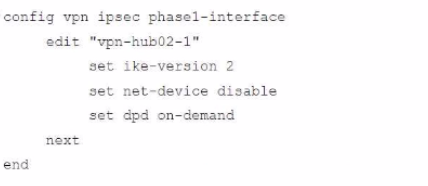
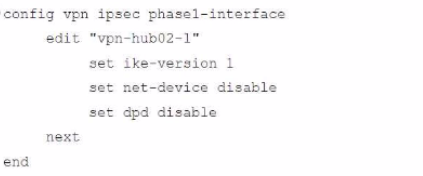
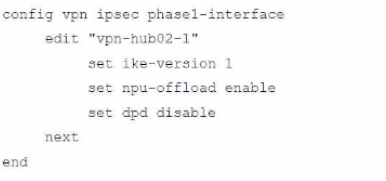
Refer to the exhibits.
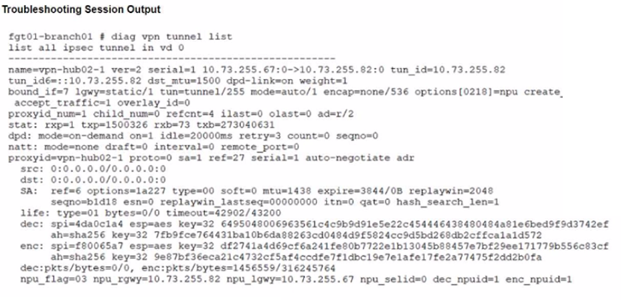
A customer is trying to restore a VPN connection configured on a FortiGate. Exhibits show output during a troubleshooting session when the VPN was working and the current baseline VPN configuration.
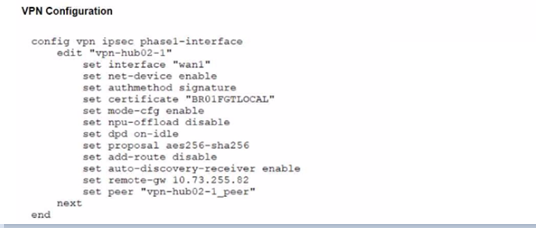
Which configuration parameters will restore VPN connectivity based on the diagnostic output?
Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
A FortiGate must be configured to accept VoIP traffic which will include session initiation protocol (SIP) traffic. Which statement about the VoIP configuration options is correct?
Refer to the exhibit.
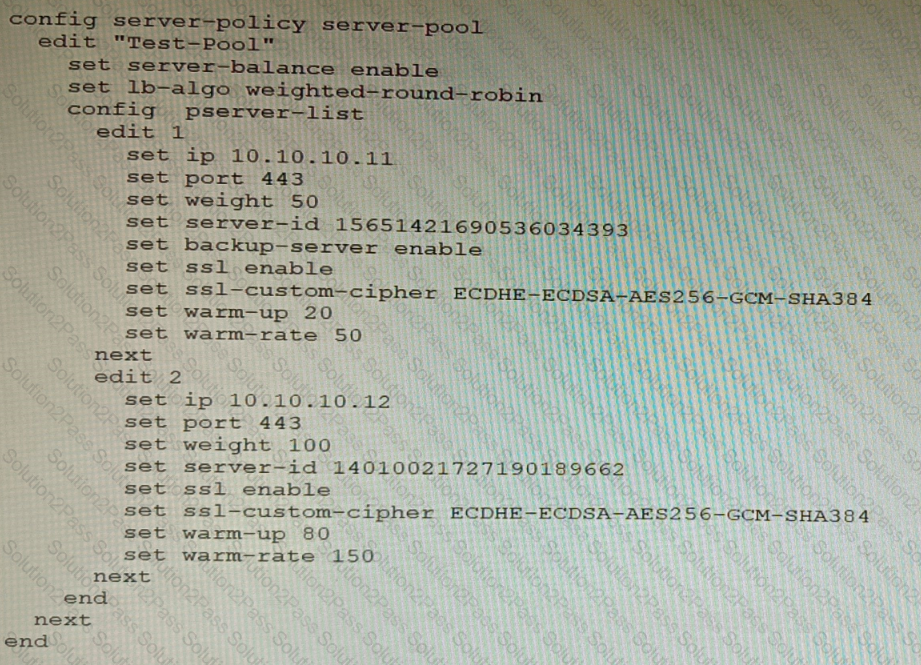
A FortiWeb appliance is configured for load balancing web sessions to internal web servers. The Server Pool is configured as shown in the exhibit.
How will the sessions be load balanced between server 1 and server 2 during normal operation?
A remote IT Team is in the process of deploying a FortiGate in their lab. The closed environment has been configured to support zero-touch provisioning from the FortiManager, on the same network, via DHCP options. After waiting 15 minutes, they are reporting that the FortiGate received an IP address, but the zero-touch process failed.
The exhibit below shows what the IT Team provided while troubleshooting this issue:

Which statement explains why the FortiGate did not install its configuration from the FortiManager?
You are migrating the branches of a customer to FortiGate devices. They require independent routing tables on the LAN side of the network.
After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments.
Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?
A customer would like to improve the performance of a FortiGate VM running in an Azure D4s_v3 instance, but they already purchased a BYOL VM04 license.
Which two actions will improve performance the most without making a FortiGate license change? (Choose two.)
You deployed a fully loaded FG-7121F in the data center and enabled sslvpn-load-balance. Based on the behavior of this feature which statement is correct?
Refer to the exhibits.
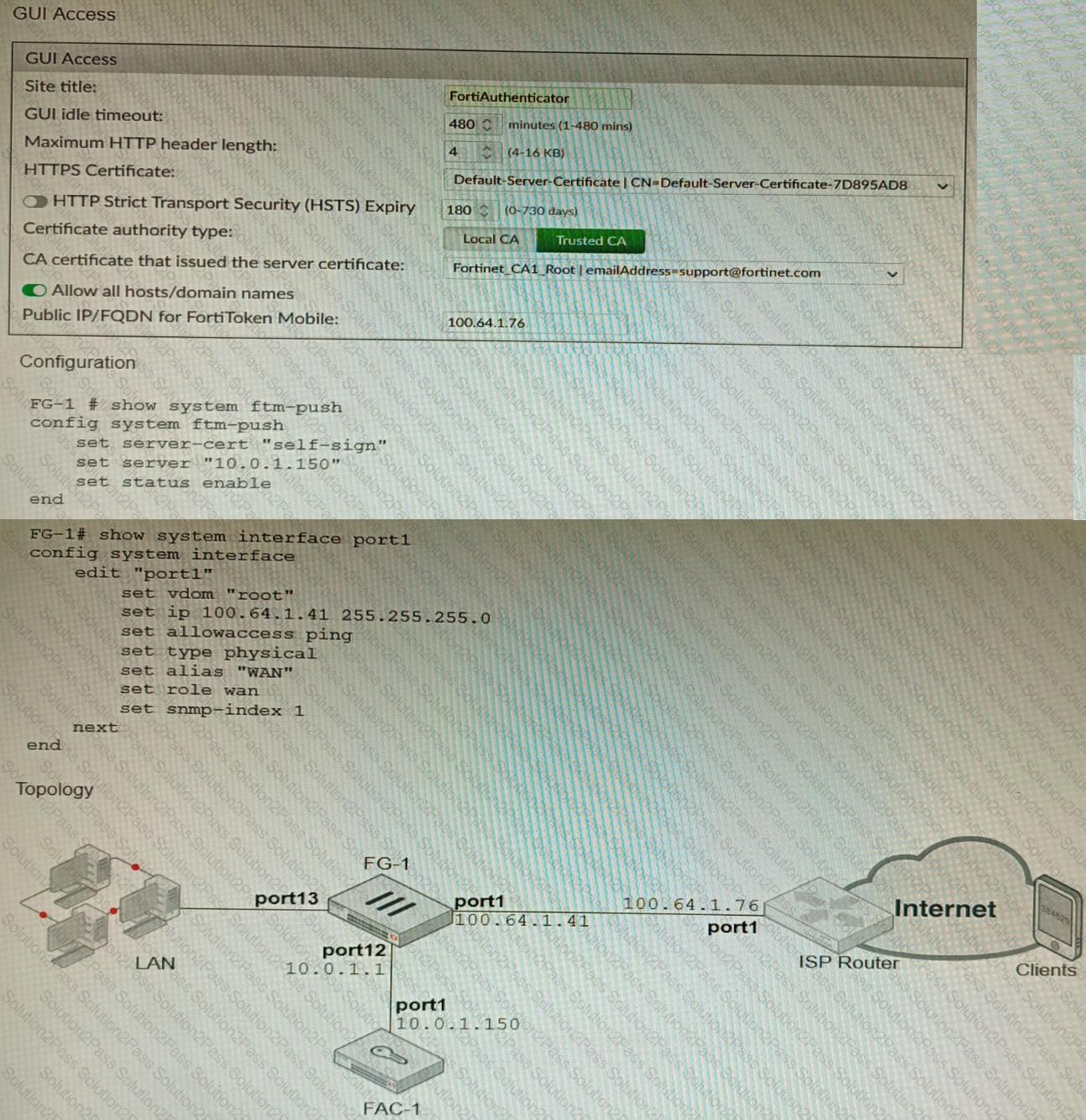
An administrator has configured a FortiGate and Forti Authenticator for two-factor authentication with FortiToken push notifications for their SSL VPN login. Upon initial review of the setup, the administrator has discovered that the customers can manually type in their two-factor code and authenticate but push notifications do not work
Based on the information given in the exhibits, what must be done to fix this?
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
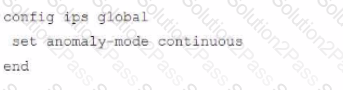
Review the Application Control log.
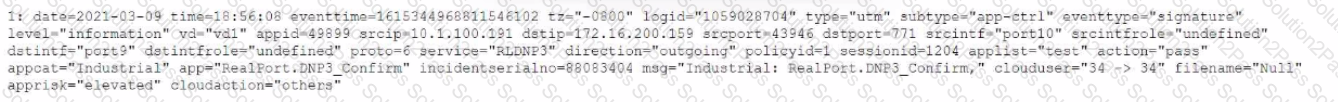
Which configuration caused the IPS engine to generate this log?
What is the benefit of using FortiGate NAC LAN Segments?
Refer to the exhibit that shows VPN debugging output.
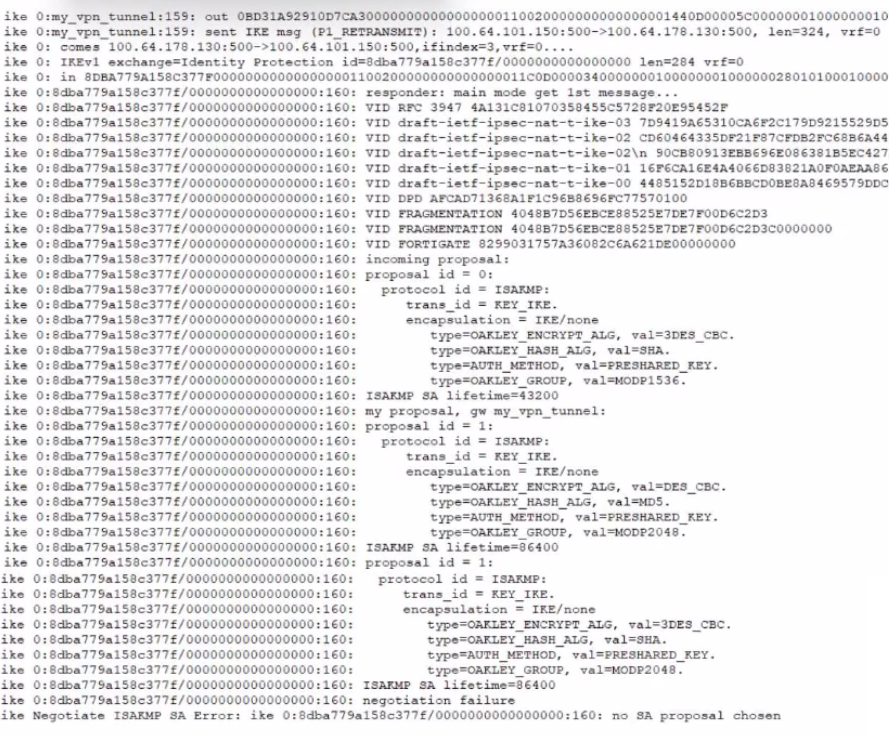
The VPN tunnel between headquarters and the branch office is not being established.
What is causing the problem?
A customer's cybersecurity department needs to implement security for the traffic between two VPCs in AWS, but these belong to different departments within the company. The company uses a single region for all their VPCs.
Which two actions will achieve this requirement while keeping separate management of each department's VPC? (Choose two.)
You are troubleshooting a FortiMail Cloud service integrated with Office 365 where outgoing emails are not reaching the recipients' mail What are two possible reasons for this problem? (Choose two.)
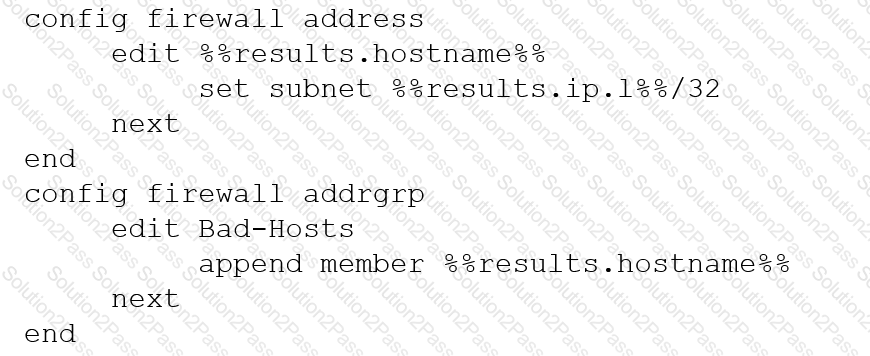
An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
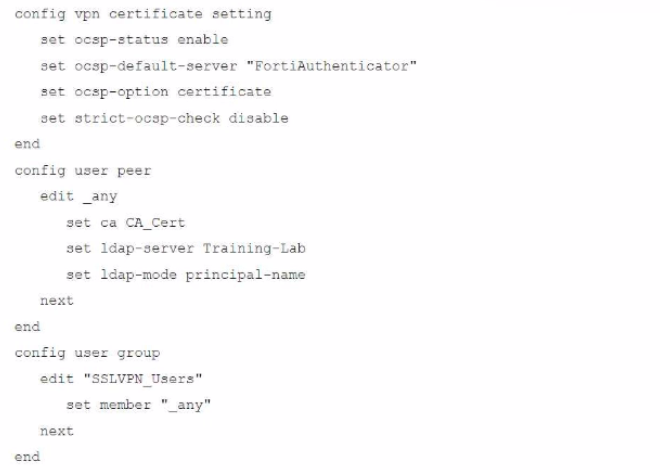
Based on this configuration, which authentication scenario will FortiGate deny?
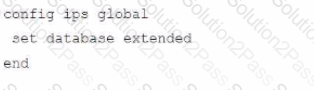
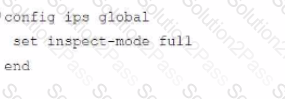
Refer to the exhibit, which shows a FortiGate configuration snippet.

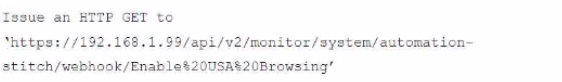
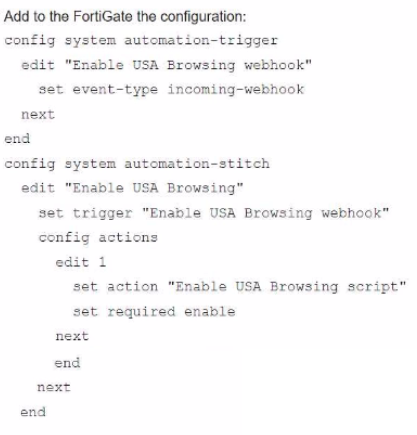
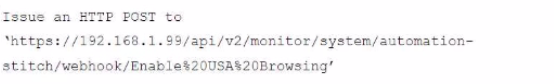
A customer in Costa Rica has a FortiGate with SD-WAN configured to use a VPN connection to the United States to browse the internet using a public IP from that country. They would like to enable the SD-WAN rule using a webhook.
Which configuration must be added to the FortiGate, and which type of HTTP request must be used to accomplish this? (Choose two.)