GSNA GIAC Systems and Network Auditor Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSNA GIAC Systems and Network Auditor certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following protocols are used to provide secure communication between a client and a server over the Internet? (Choose two)
You work as an Exchange Administrator for XYZ CORP. The network design of the company is given below:

Employees are required to use Microsoft Outlook Web Access to access their emails remotely. You are required to accomplish the following goals: Ensure fault tolerance amongst the servers. Ensure the highest level of security and encryption for the Outlook Web Access clients. What will you do to accomplish these goals?
Which of the following services are provided by the proxy servers?
Which of the following commands can be used to format text files?
Martha works as a Web Developer for XYZ CORP. She is developing a Web site for the company. In the Web site, she uses multiple and overlapping style definitions to control the appearance of HTML elements. What is this technique known as?
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
You have just taken over as the Network Administrator for a medium sized company. You want to check to see what services are exposed to the outside world. What tool would you use to accomplish this?
You are the Security Administrator for an Internet Service Provider. From time to time your company gets subpoenas from attorneys and law enforcement for records of customers' access to the internet. What policies must you have in place to be prepared for such requests?
Which of the following encryption encoding techniques is used in the basic authentication method?
Which of the following statements about a screened host is true?
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. You run the following command for a router interface: show interface serial0 You get the following output: Serial0 is administratively down, line protocol is down What will be your conclusion after viewing this output?
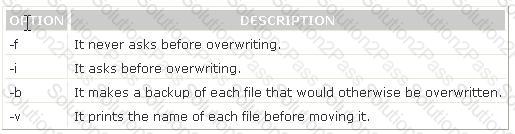
You have to move the whole directory /foo to /bar. Which of the following commands will you use to accomplish the task?
John works as a contract Ethical Hacker. He has recently got a project to do security checking for www.we-are-secure.com. He wants to find out the operating system of the we-are-secure server in the information gathering step. Which of the following commands will he use to accomplish the task? (Choose two)
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to fix partitions on a hard drive. Which of the following Unix commands can you use to accomplish the task?
Which of the following tools works both as an encryption-cracking tool and as a keylogger?
You check performance logs and note that there has been a recent dramatic increase in the amount of broadcast traffic. What is this most likely to be an indicator of?
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to run a command that forces all the unwritten blocks in the buffer cache to be written to the disk. Which of the following Unix commands can you use to accomplish the task?
You work as a Network Administrator for XYZ CORP. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. You have installed a Windows Server 2008 computer. You have configured auditing on this server. The client computers of the company use the Windows XP Professional operating system. You want to audit each event that is related to a user managing an account in the user database on the computer where the auditing is configured. To accomplish the task, you have enabled the Audit account management option on the server. Which of the following events can be audited by enabling this audit option?
Which of the following tools is used to make fake authentication certificates?
In addition to denying and granting access, what other services does a firewall support?
 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG