GSNA GIAC Systems and Network Auditor Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSNA GIAC Systems and Network Auditor certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He performs Web vulnerability scanning on the We-are-secure server. The output of the scanning test is as follows: C.\whisker.pl -h target_IP_address -- whisker / v1.4.0 / rain forest puppy / www.wiretrip.net -- = - = - = - = - = = Host: target_IP_address = Server: Apache/1.3.12 (Win32) ApacheJServ/1.1 mod_ssl/2.6.4 OpenSSL/0.9.5a mod_perl/1.22 + 200 OK: HEAD /cgi-bin/printenv John recognizes /cgi-bin/printenv vulnerability ( 'Printenv' vulnerability) in the We_are_secure server. Which of the following statements about 'Printenv' vulnerability are true?
Which of the following statements about Secure Sockets Layer (SSL) are true? (Choose two)
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He begins to perform a pre-attack test before conducting an attack on the We-are-secure server. Which of the following will John perform in the pre-attack phase?
Mike works as a Network Engineer for XYZ CORP. The company has a multi-platform network. Recently, the company faced lots of blended threat issues that lead to several drastic attacks. Mike has been assigned a project to manage the resources and services of the company through both Intranet and Internet to protect the company from these attacks. Mike needs a system that provides auto-discovering and network topology building features to allow him to keep an intuitive view of the IT infrastructure. What will Mike use to meet the requirement of the project?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
You are concerned about rootkits on your network communicating with attackers outside your network. Without using an IDS how can you detect this sort of activity?
A sequence number is a 32-bit number ranging from 1 to 4,294,967,295. When data is sent over the network, it is broken into fragments (packets) at the source and reassembled at the destination system. Each packet contains a sequence number that is used by the destination system to reassemble the data packets in the correct order. The Initial Sequence Number of your computer is 24171311 at login time. You connect your computer to a computer having the IP address 210.213.23.21. This whole process takes three seconds. What will the value of the Initial Sequence Number be at this moment?
Peter works as a Web Developer for XYZ CORP. He is developing a Web site for the company. Peter specifies MARGINHEIGHT="0" and MARGINWIDTH="0" in one of the Web pages. How will this affect the Web page?
Which of the following tools can be used by a user to hide his identity?
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that Host B is not able to connect to other resources on the network. The IP configuration of Host B is shown below:
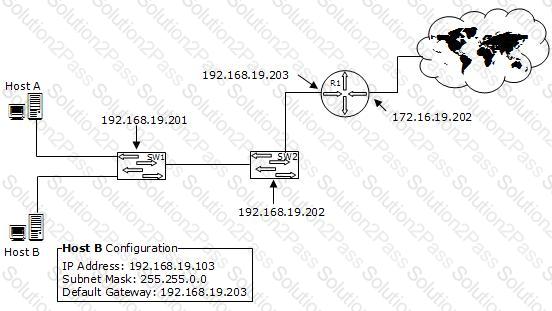
Which of the following is the most likely cause of the issue?
You work as a Network Architect for Tech Perfect Inc. The company has a TCP/IP based Enterprise network. The company uses Cisco IOS technologies in the Enterprise network. You have enabled system message logging (syslog) service on all the routers that are currently working in the network. The syslog service provides all the reports, and important error and notification messages. You want to store all the reports and messages. Choose the locations where you can store all of these.
Which of the following is the most secure place to host a server that will be accessed publicly through the Internet?
The following output is generated by running the show ip route command: RouterA#show ip route < - - Output Omitted for brevity - -> Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
You work as an IT Technician for XYZ CORP. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement? (Choose two)
Which of the following techniques can be used to determine the network ranges of any network?
A Cisco router can have multiple connections to networks. These connections are known as interfaces for Cisco Routers. For naming each interface, Cisco generally uses the type of interface as part of the name. Which of the following are true about the naming conventions of Cisco Router interfaces?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to break a dat a.txt file, 200MB in size, into two files in which the size of the first file named data.txt.aa should be 150MB and that of the second file named data.txt.ab should be 50MB. To accomplish his task and to further delete the data.txt file, he enters the following command: split --verbose -b 150m data.txt data.txt. ; rm -vf data.txt Which of the following commands can John use to join the splitted files into a new data.txt file?
Which TCP and UDP ports can be used to start a NULL session attack in NT and 2000 operating systems?
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to identify the secure terminals from where the root can be allowed to log in. Which of the following Unix configuration files can you use to accomplish the task?
