GSNA GIAC Systems and Network Auditor Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSNA GIAC Systems and Network Auditor certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which of the following is Microsoft's implementation of the file and application server for the Internet and private intranets?
You work as a Network Administrator for BetaTech Inc. You have been assigned the task of designing the firewall policy for the company. Which of the following statements is unacceptable in the 'acceptable use statement' portion of the firewall policy?
Which of the following is the default port for Hypertext Transfer Protocol (HTTP)?
You work as the Project Engineer for XYZ CORP. The company has a Unix-based network. Your office consists of one server, seventy client computers, and one print device. You raise a request for printing a confidential page. After 30 minutes, you find that your print request job is not processed and is at the seventh position in the printer queue. You analyze that it shall take another one hour to print. You decide to remove your job from the printer queue and get your page printed outside the office. Which of the following Unix commands can you use to remove your job from the printer queue?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to use Kismet as a wireless sniffer to sniff the We-are-secure network. Which of the following IEEE-based traffic can be sniffed with Kismet?
Which of the following allows the use of multiple virtual servers using different DNS names resolved by the same IP address?
You work as a Network Administrator for ABC Inc. The company uses a secure wireless network. John complains to you that his computer is not working properly. What type of security audit do you need to conduct to resolve the problem?
You are concerned about an attacker being able to get into your network. You want to make sure that you are informed of any network activity that is outside normal parameters. What is the best way to do this?
Mark implements a Cisco unified wireless network for Tech Perfect Inc. Which functional area of the Cisco unified wireless network architecture includes intrusion detection and prevention?
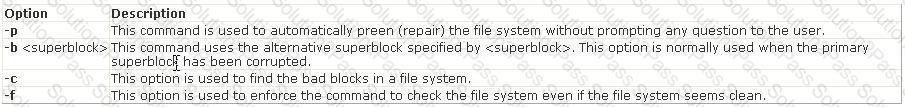
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system. Which of the following Unix commands can you use to accomplish the task?
Sam works as a Web Developer for McRobert Inc. He creates a Web site. He wants to include the following table in the Web site:
He writes the following HTML code to create the table:
1.
| 8. | 10. | 12. |
16. | 18. | 20. |
Which of the following tags will Sam place at lines 3 and 4 to create the table?
Which of the following responsibilities does not come under the audit process?
Which of the following types of firewall functions at the Session layer of OSI model?
Which of the following statements about session tracking is true?
Which of the following tools can be used to read NetStumbler's collected data files and present street maps showing the logged WAPs as icons, whose color and shape indicates WEP mode and signal strength?
You work as a Network Administrator for XYZ CORP. The company has a Windows-based network. You are concerned about the vulnerabilities existing in the network of the company. Which of the following can be a cause for making the network vulnerable? (Choose two)
Sam works as a Network Administrator for Blue Well Inc. All client computers in the company run the Windows Vista operating. Sam creates a new user account. He wants to create a temporary password for the new user such that the user is forced to change his password when he logs on for the first time. Which of the following options will he choose to accomplish the task?
Which of the following is a prevention-driven activity to reduce errors in the project and to help the project meet its requirements?
Mark works as a Web Designer for XYZ CORP. The company has a Windows-based network. Mark creates an HTML document that gives the following error on execution: "These hypertext system features are not supported by HTML". Which of the following can be the hypertext system features that are NOT supported by HTML? (Choose three)
Web mining allows a user to look for patterns in data through content mining, structure mining, and usage mining. What is the function of structure mining?
 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG