GSNA GIAC Systems and Network Auditor Free Practice Exam Questions (2026 Updated)
Prepare effectively for your GIAC GSNA GIAC Systems and Network Auditor certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You work as the Network Technician for XYZ CORP. The company has a Linux-based network. You are working on the Red Hat operating system. You want to view only the last 4 lines of a file named /var/log/cron. Which of the following commands should you use to accomplish the task?
What does a firewall check to prevent certain ports and applications from getting the packets into an Enterprise?
Which of the following are the countermeasures against WEP cracking?
Pervasive IS controls can be used across all the internal departments and external contractors to define the direction and behavior required for the technology to function properly. When these controls are implemented properly, which of the following areas show the reliability improvement? (Choose three)
Which of the following are the drawbacks of the NTLM Web authentication scheme?
You work as a Web Developer for XYZ CORP. The company has a Windows-based network. You have been assigned the task to secure the website of the company. To accomplish the task, you want to use a website monitoring service. What are the tasks performed by a website monitoring service?
With reference to the given case study, one of the security goals requires to configure a secure connection between the Boston distribution center and the headquarters. You want to implement IP filter to fulfill the security requirements. How should you implement IP filters at the headquarters? (Click the Exhibit button on the toolbar to see the case study.)
You work as a Network Administrator for XYZ CORP. The company's Windows 2000 network is configured with Internet Security and Acceleration (ISA) Server 2000. ISA Server is configured as follows: The server uses the default site and content rule and default IP packet filters. Packet filtering is enabled. The server has two protocol rules:
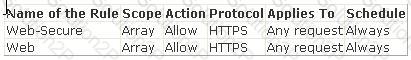
Users in the network complain that they are unable to access secure Web sites. However, they are able to connect to Web sites in which secure transmission is not required. What is the most likely cause?
Which of the following statements are true about security risks? (Choose three)
From an auditing perspective, database security can be broken down into four key categories: Server Security Database Connections Table Access Control Restricting Database Access Which of the following categories leads to the process of limiting access to the database server?
Which of the following commands can be used to find out where commands are located?
You work as a Network Administrator for NTY Inc. The company has a secure wireless network. While auditing the network for maintaining security, you find an unknown node. You want to locate that node. Which tool will you use to pinpoint the actual physical location of the node?
You work as a Software Developer for UcTech Inc. You want to ensure that a class is informed whenever an attribute is added, removed, or replaced in a session. Which of the following is the event that you will use to accomplish the task?
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Which of the following are attributes of the
