HPE6-A78 HP Aruba Certified Network Security Associate Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HP HPE6-A78 Aruba Certified Network Security Associate Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is one practice that can help you to maintain a digital chain of custody in your network?
What purpose does an initialization vector (IV) serve for encryption?
A company has Aruba Mobility Controllers (MCs). Aruba campus APs. and ArubaOS-CX switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type The ClearPass admins tell you that they want to run Network scans as part of the solution
What should you do to configure the infrastructure to support the scans?
An AOS-CX switch currently has no device fingerprinting settings configured on it. You want the switch to start collecting DHCP and LLDP information. You enter these commands:
Switch(config)# client device-fingerprint profile myprofile
Switch(myprofile)# dhcp
Switch(myprofile)# lldp
What else must you do to allow the switch to collect information from clients?
A client has accessed an HTTPS server at myhost1.example.com using Chrome. The server sends a certificate that includes these properties:
Subject name: myhost.example.com
SAN: DNS: myhost.example.com; DNS: myhost1.example.com
Extended Key Usage (EKU): Server authentication
Issuer: MyCA_SigningThe server also sends an intermediate CA certificate for MyCA_Signing, which is signed by MyCA. The client’s Trusted CA Certificate list does not include the MyCA or MyCA_Signing certificates.Which factor or factors prevent the client from trusting the certificate?
Your Aruba Mobility Master-based solution has detected a rogue AP Among other information the ArubaOS Detected Radios page lists this Information for the AP
SSID = PubllcWiFI
BSSID = a8M27 12 34:56
Match method = Exact match
Match type = Eth-GW-wired-Mac-Table
The security team asks you to explain why this AP is classified as a rogue. What should you explain?
What distinguishes a Distributed Denial of Service (DDoS) attack from a traditional Denial of Service (DoS) attack?
You have been asked to send RADIUS debug messages from an ArubaOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command: logging 10.5.6.12
You enter this command: debug radius all
What is the correct debug destination?
What is one method for HPE Aruba Networking ClearPass Policy Manager (CPPM) to use DHCP to classify an endpoint?
What is a benefit of Opportunistic Wireless Encryption (OWE)?
You are deploying a new wireless solution with an HPE Aruba Networking Mobility Master (MM), Mobility Controllers (MCs), and campus APs (CAPs). The solution will include a WLAN that uses Tunnel for the forwarding mode and WPA3-Enterprise for the security option.
You have decided to assign the WLAN to VLAN 301, a new VLAN. A pair of core routing switches will act as the default router for wireless user traffic.
Which links need to carry VLAN 301?
A company has an AOS controller-based solution with a WPA3-Enterprise WLAN, which authenticates wireless clients to HPE Aruba Networking ClearPass Policy Manager (CPPM). The company has decided to use digital certificates for authentication. A user's Windows domain computer has had certificates installed on it. However, the Networks and Connections window shows that authentication has failed for the user. The Mobility Controller’s (MC's) RADIUS events show that it is receiving Access-Rejects for the authentication attempt.
What is one place that you can look for deeper insight into why this authentication attempt is failing?
A company has a WLAN that uses Tunnel forwarding mode and WPA3-Enterprise security, supported by an Aruba Mobility Controller (MC) and campus APs (CAPs). You have been asked to capture packets from a wireless client connected to this WLAN and submit the packets to the security team.
What is a guideline for this capture?
What is a difference between passive and active endpoint classification?
A user is having trouble connecting to an AP managed by a standalone Mobility Controller (MC). What can you do to get detailed logs and debugs for that user's client?
You need to implement a WPA3-Enterprise network that can also support WPA2-Enterprise clients. What is a valid configuration for the WPA3-Enterprise WLAN?
Your ArubaoS solution has detected a rogue AP with Wireless intrusion Prevention (WIP). Which information about the detected radio can best help you to locate the rogue device?
An ArubaOS-CX switch enforces 802.1X on a port. No fan-through options or port-access roles are configured on the port The 802 1X supplicant on a connected client has not yet completed authentication
Which type of traffic does the authenticator accept from the client?
Refer to the exhibit.
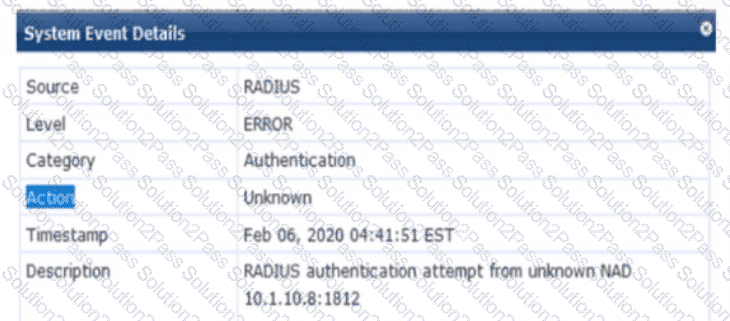
You are deploying a new HPE Aruba Networking Mobility Controller (MC), which is enforcing authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown in the exhibit in the CPPM Event Viewer.
What should you check?
Which is a correct description of a Public Key Infrastructure (PKI)?
