HPE6-A78 HP Aruba Certified Network Security Associate Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HP HPE6-A78 Aruba Certified Network Security Associate Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is a consideration for implementing wireless containment in response to unauthorized devices discovered by ArubaOS Wireless Intrusion Detection (WIP)?
What is a Key feature of me ArubaOS firewall?
What is one way that WPA3-Enterprise enhances security when compared to WPA2-Enterprise?
What is social engineering?
What role does the Aruba ClearPass Device Insight Analyzer play in the Device Insight architecture?
You have been instructed to look in an AOS Security Dashboard’s client list. Your goal is to find clients that belong to the company and have connected to devices that might belong to hackers.
Which client fits this description?
What is one benefit of a Trusted Platform Module (TPM) on an Aruba AP?
You are setting up an Aruba mobility solution which includes a Mobility Master (MM), Mobility Controllers (MCs), and campus APs (CAPs) for a university. The university plans to enforce WPA2-Enterprise for all users' connections. The university wants to apply one set of access control rules to faculty users' traffic and a different set of rules to students' traffic.
What is the best approach for applying the correct rules to each group?
What is a benefit of deploying Aruba ClearPass Device insight?
A company has AOS-CX switches deployed in a two-tier topology that uses OSPF routing at the core.
You need to prevent ARP poisoning attacks. To meet this need, what is one technology that you could apply to user VLANs on access layer switches? (Select two.)
Your AOS solution has detected a rogue AP with Wireless Intrusion Prevention (WIP). Which information about the detected radio can best help you to locate the rogue device?
What is a benefit of Protected Management Frames (PMF). sometimes called Management Frame Protection (MFP)?
Which attack is an example or social engineering?
Refer to the exhibit.
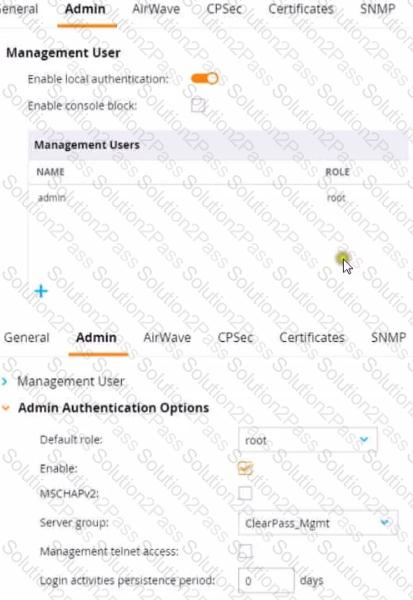
This Aruba Mobility Controller (MC) should authenticate managers who access the Web Ul to ClearPass Policy Manager (CPPM) ClearPass admins have asked you to use RADIUS and explained that the MC should accept managers' roles in Aruba-Admin-Role VSAs
Which setting should you change to follow Aruba best security practices?
You have been asked to send RADIUS debug messages from an AOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command:
logging 10.5.15.6
You enter this command:
debug radius all
What is the correct debug destination?
What is an Authorized client as defined by ArubaOS Wireless Intrusion Prevention System (WIP)?
A customer has an AOS-10 network infrastructure. The customer is looking for a solution that can classify many different types of devices, including IoT devices. Which solution should you explain can provide these capabilities?
You have been instructed to look in the ArubaOS Security Dashboard's client list. Your goal is to find clients that belong to the company and have connected to devices that might belong to hackers.
Which client fits this description?
Which correctly describes one of HPE Aruba Networking ClearPass Policy Manager's (CPPM's) device profiling methods?
What is one thing can you determine from the exhibits?
