HPE7-A02 HP Aruba Certified Network Security Professional Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your HP HPE7-A02 Aruba Certified Network Security Professional Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
What is a benefit of Online Certificate Status Protocol (OCSP)?
You manage AOS-10 APs with HPE Aruba Networking Central. A role is configured on these APs with these rules (in order):
Allow UDP on port 67 to any destination
Allow any to network 10.1.4.0/23
Deny any to network 10.1.0.0/18 + log
Deny any to network 10.0.0.0/8
Allow any to any destination
You add this new rule immediately before rule 4:
Deny SSH to network 10.1.0.0/21 + denylist
After this change, what happens when a client assigned to this role sends SSH traffic to 10.1.7.12?
You are proposing HPE Aruba Networking ZTNA to an organization that currently uses a third-party, IPsec-based client-to-site VPN.
What is one advantage of ZTNA that you should emphasize?
The security team needs you to show them information about MAC spoofing attempts detected by HPE Aruba Networking ClearPass Policy Manager (CPPM).
What should you do?
You need to create a rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) role mapping policy that references a ClearPass Device Insight Tag.
Which Type (namespace) should you specify for the rule?
You are setting up an HPE Aruba Networking VIA solution for a company. You need to configure access control policies for applications and resources that remote
clients can access when connected to the VPN.
Where on the VPNC should you configure these policies?
Which use case is fulfilled by applying a time range to a firewall rule on an AOS device?
A company has AOS-CX switches and HPE Aruba Networking APs, which run AOS-10 and bridge their SSIDs. Company security policies require 802.1X on all edge ports, some of which connect to APs. How should you configure the auth-mode on AOS-CX switches?

(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central
interface as versions change; however, similar concepts continue to apply.)
An HPE Aruba Networking 9x00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit. What would cause the
gateway to drop traffic as part of its IDPS settings?
What role can Internet Key Exchange (IKE)/IKEv2 play in an HPE Aruba Networking client-to-site VPN?
A ClearPass Policy Manager (CPPM) service includes these settings:
Role Mapping Policy:
Evaluate: Select first
Rule 1 conditions:
Authorization:AD:Groups EQUALS Managers
Authentication:TEAP-Method-1-Status EQUALS Success
Rule 1 role: manager
Rule 2 conditions:
Authentication:TEAP-Method-1-Status EQUALS Success
Rule 2 role: domain-comp
Default role: [Other]
Enforcement Policy:
Evaluate: Select first
Rule 1 conditions:
Tips Role EQUALS manager AND Tips Role EQUALS domain-comp
Rule 1 profile list: domain-manager
Rule 2 conditions:
Tips Role EQUALS manager
Rule 2 profile list: manager-only
Rule 3 conditions:
Tips Role EQUALS domain-comp
Rule 3 profile list: domain-only
Default profile: [Deny access]
A client is authenticated by the service. CPPM collects attributes indicating that the user is in the Contractors group, and the client passed both TEAP methods.
Which enforcement policy will be applied?
A company has a third-party security appliance deployed in its data center. The company wants to pass all traffic for certain clients through that device before forwarding that traffic toward its ultimate destination.
Which AOS-CX switch technology fulfills this use case?
Which statement describes Zero Trust Security?
You have run an Active Endpoint Security Report on HPE Aruba Networking ClearPass. The report indicates that hundreds of endpoints have MAC addresses but
no known IP addresses.
What is one step for addressing this issue?
You are setting up user-based tunneling (UBT) between access layer AOS-CX switches and AOS-10 gateways. You have selected reserved (local) VLAN mode.
Tunneled devices include IoT devices, which should be assigned to:
Roles: iot on the switches and iot-wired on the gateways
VLAN: 64, for which the gateways route traffic.
IoT devices connect to the access layer switches' edge ports, and the access layer switches reach the gateways on their uplinks.
Where must you configure VLAN 64?
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy
Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to
further protect itself from internal threats.
What is one solution that you can recommend?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. You want
to assign managers to groups on the AOS-CX switch by name.
How do you configure this setting in a CPPM TACACS+ enforcement profile?
A company wants to apply a standard configuration to all AOS-CX switch ports and have the ports dynamically adjust their configuration based on the identity of
the user or device that connects. They want to centralize configuration of the identity-based settings as much as possible.
What should you recommend?
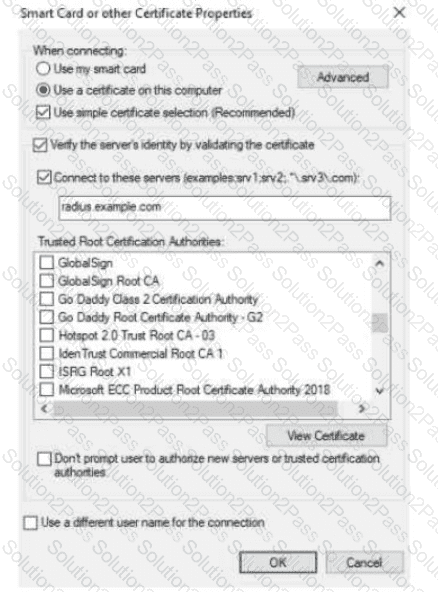
The exhibit shows the 802.1X-related settings for Windows domain clients. What should admins change to make the settings follow best security practices?
A company has AOS-CX switches and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants switches to implement 802.1X authentication to CPPM and download user roles. What is one task that you must complete on CPPM to support this use case?
