H12-711_V4.0 Huawei HCIA-Security V4.0 Exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Huawei H12-711_V4.0 HCIA-Security V4.0 Exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
An enterprise wants to build a server system and requires the following functions: 1. The enterprise needs to have its own dedicated mailbox, and the sending and receiving of emails needs to go through the enterprise's server; 2. The server must provide file transfer and access services. Users in different departments of the enterprise provide accounts with different permissions: 3. When the enterprise accesses the internal webpage of the enterprise, the enterprise can directly enter the domain name in the browser to access. To meet the above requirements, which of the following servers do enterprises need to deploy? ( )*
Which of the following descriptions of server authentication is correct?
Certificates saved in DER format may or may not contain a private key.
Among the various aspects of the risk assessment of IS027001, which of the following does not belong to the system design and release process?
In the Linux system, which of the following is the command to query the P address information? ( )[Multiple choice]*
We should choose the encryption algorithm according to our own use characteristics. When we need to encrypt a large amount of data, it is recommended to use the ____ encryption algorithm to improve the encryption and decryption speed.[fill in the blank]*
Which of the following descriptions of single sign-on is correct?
Drag the phases of the cybersecurity emergency response on the left into the box on the right, and arrange them from top to bottom in the order of execution.[fill in the blank]*

SSL VPN is a VPN technology that realizes remote secure access through SSL protocol. Which of the following software must be installed when using SSL VPN?
An engineer needs to back up the firewall configuration. Now he wants to use a command to view all the current configurations of the firewall. May I ask the command he uses is ____[fill in the blank]*
DES is a stream encryption algorithm, because the cipher capacity is only 56 bits, so it is not enough to deal with the weakness of insufficient security, and later 3DES was proposed.
Database operation records can be used as ___ evidence to backtrack security events.[fill in the blank]*
When the Layer 2 switch receives a unicast frame and the MAC address table entry of the switch is empty, the switch discards the unicast frame.
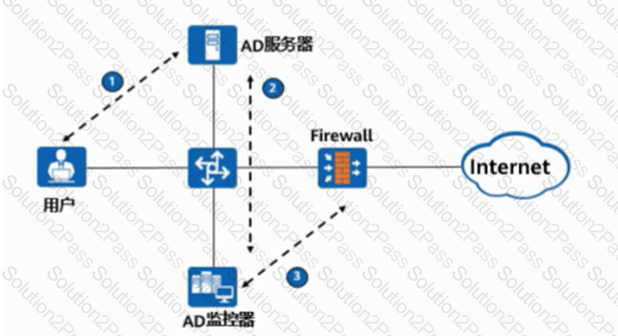
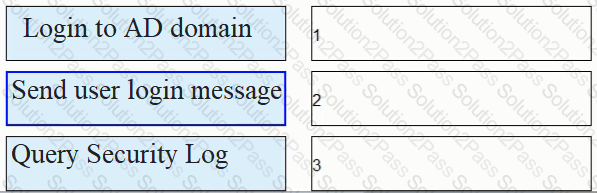
As shown in the figure, the process of AD single sign-on (querying the security log mode of AD server), please match the corresponding operation process.
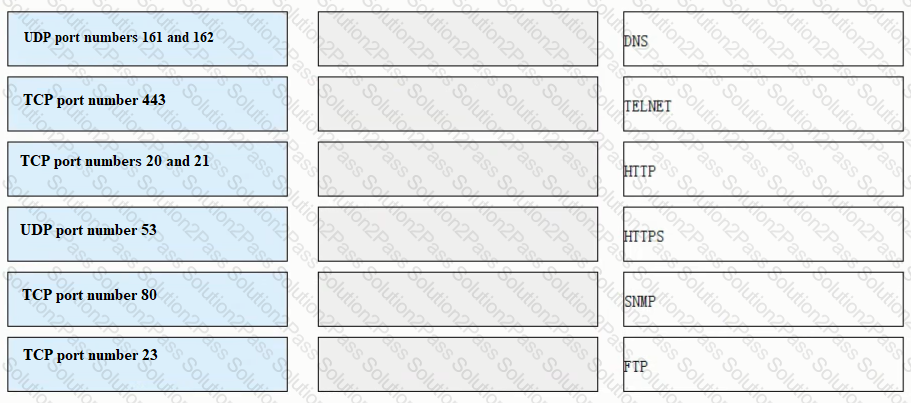
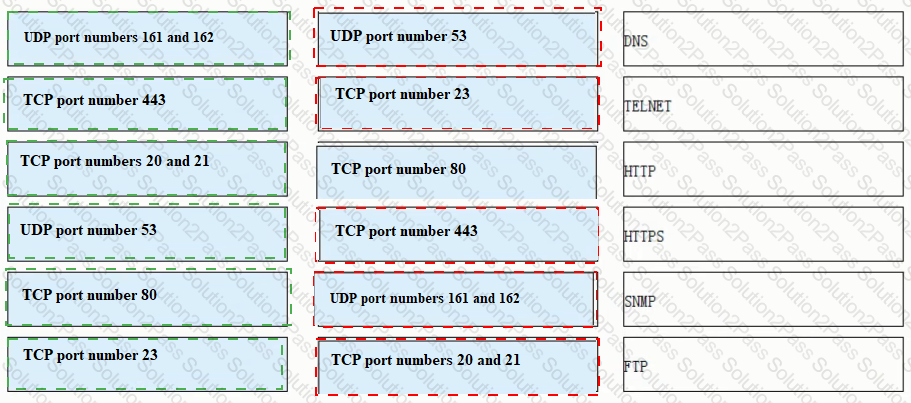
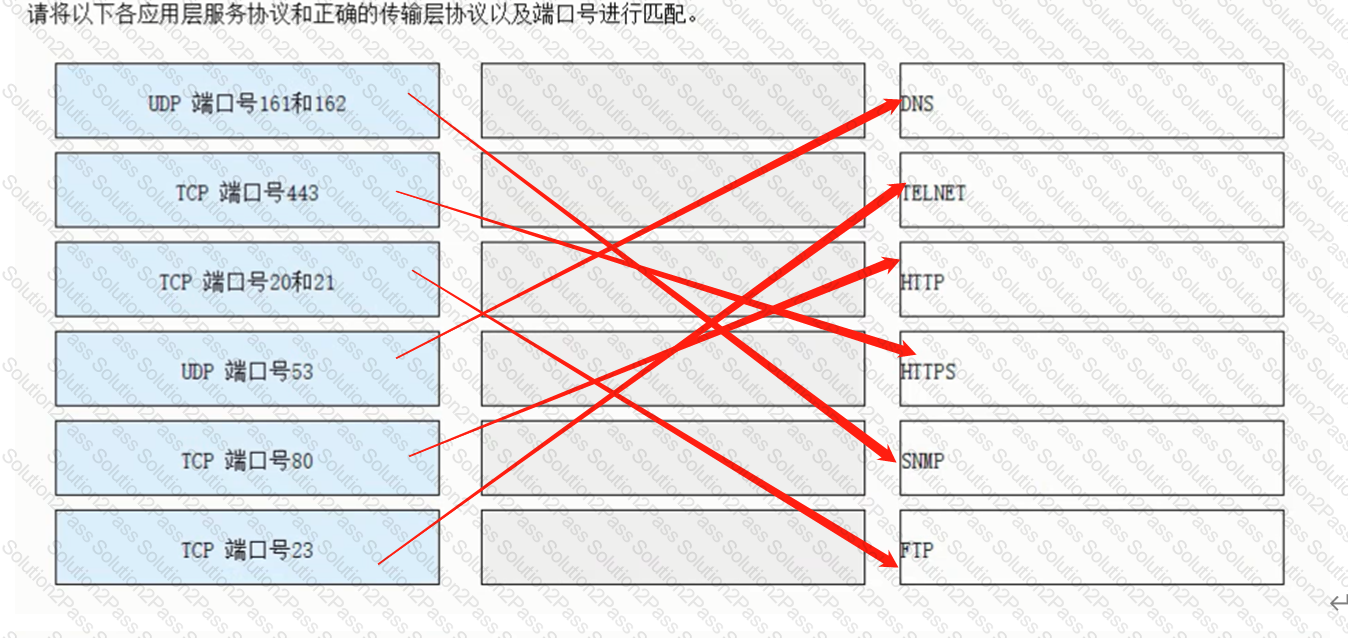
Match each of the following application layer service protocols with the correct transport layer protocols and port numbers.
What is correct in the following description of Security Alliance in IPSec?
There are two ways to set up an IPSec SA
In cases where some configurations alter existing session table entries and want them to take effect immediately, you can regenerate the session table by clearing the session table information. All session table information can be cleared by executing the _____firewall session table command.
The following description of the intrusion fire protection system IPS, which is correct?
The following description of the construction of a digital certificate, which item is wrong
At what layer does packet filtering technology in the firewall filter packets?
 Chart, line chart
Description automatically generated
Chart, line chart
Description automatically generated