JN0-335 Juniper Security, Specialist (JNCIS-SEC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-335 Security, Specialist (JNCIS-SEC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Exhibit
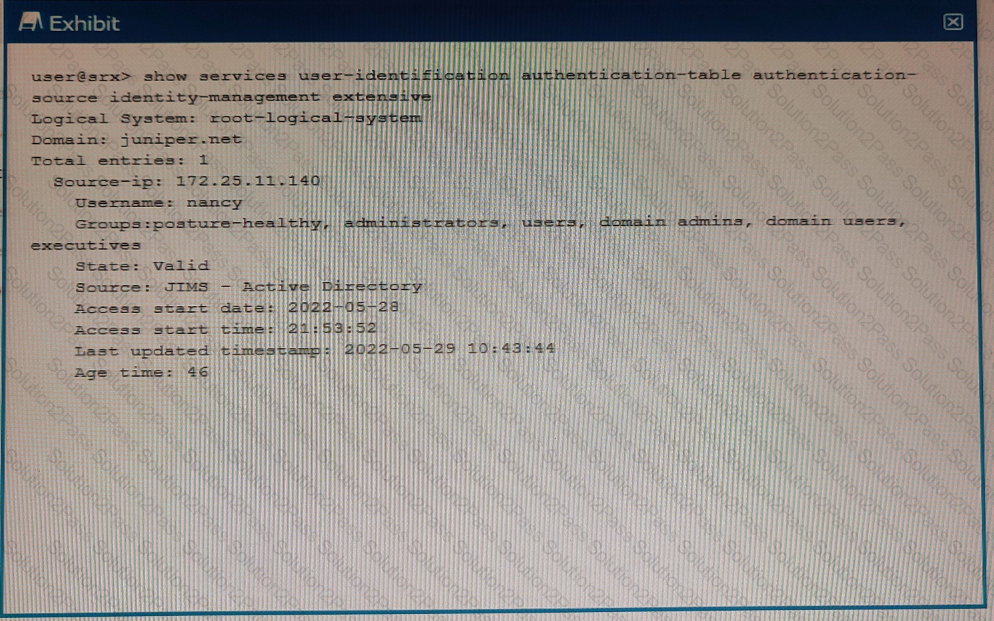
Referring to the exhibit, which two statements are true? (Choose two.)
Which two statements about the DNS ALG are correct? (Choose two.)
Exhibit
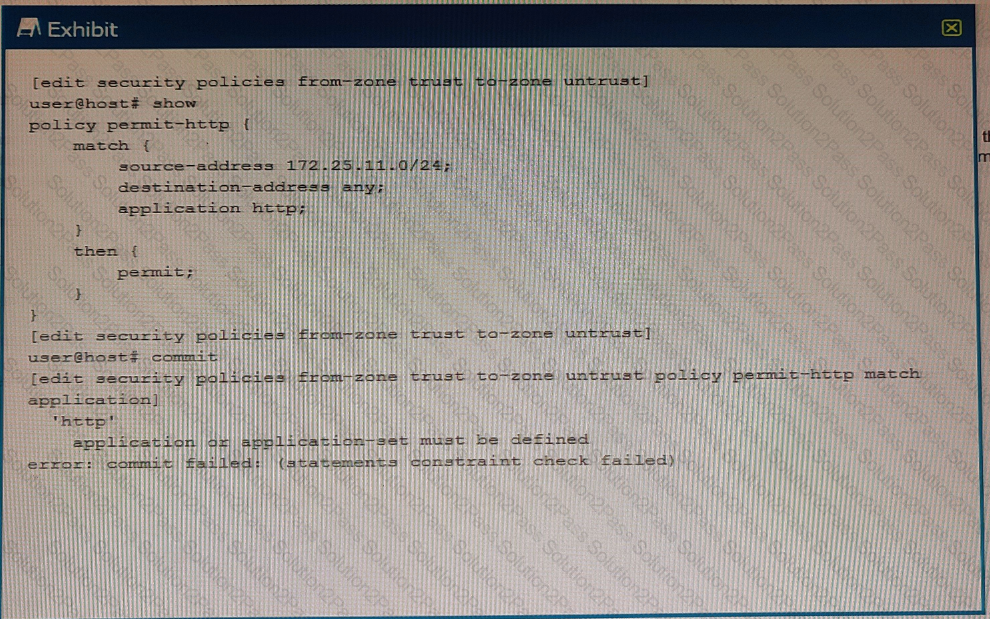
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
You are experiencing excessive packet loss on one of your two WAN links route traffic from the degraded link to the working link
Which AppSecure component would you use to accomplish this task?
Your manager asks you to provide firewall and NAT services in a private cloud.
Which two solutions will fulfill the minimum requirements for this deployment? (Choose two.)
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
Which two statements are correct about JSA data collection? (Choose two.)
What information does encrypted traffic insights (ETI) use to notify SRX Series devices about known malware sites?
Which two types of SSL proxy are available on SRX Series devices? (Choose two.)
