JN0-335 Juniper Security, Specialist (JNCIS-SEC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-335 Security, Specialist (JNCIS-SEC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two statements about SRX chassis clustering are correct? (Choose two.)
Which two features are configurable on Juniper Secure Analytics (JSA) to ensure that alerts are triggered when matching certain criteria? (Choose two.)
How does the SSL proxy detect if encryption is being used?
Which two statements are correct about chassis clustering? (Choose two.)
Which two statements are true about the vSRX? (Choose two.)
Which two statements are correct about SSL proxy server protection? (Choose two.)
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
Exhibit
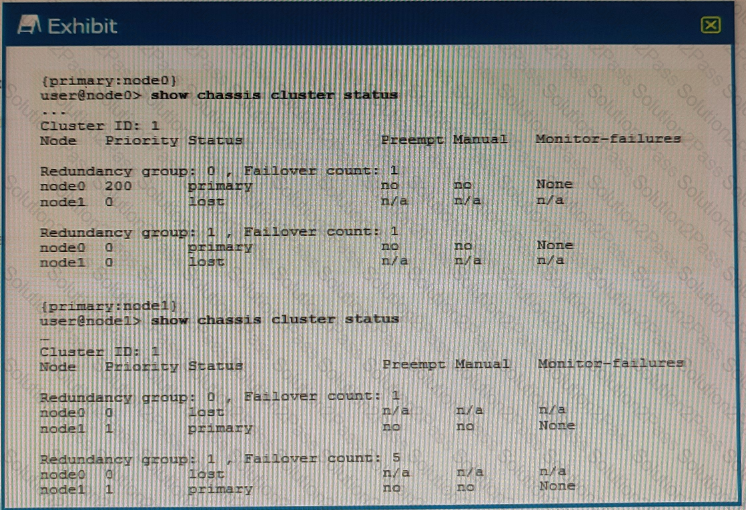
Referring to the exhibit, what do you determine about the status of the cluster.
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Which two statements are true about application identification? (Choose two.)
Which two statements are true about the vSRX? (Choose two.)
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
Your company is using the Juniper ATP Cloud free model. The current inspection profile is set at 10 MB You are asked to configure ATP Cloud so that executable files up to 30 MB can be scanned while at the same time minimizing the change in scan time for other file types.
Which configuration should you use in this scenario?
Which two statements are correct when considering IPS rule base evaluation? (Choose two.)
Exhibit
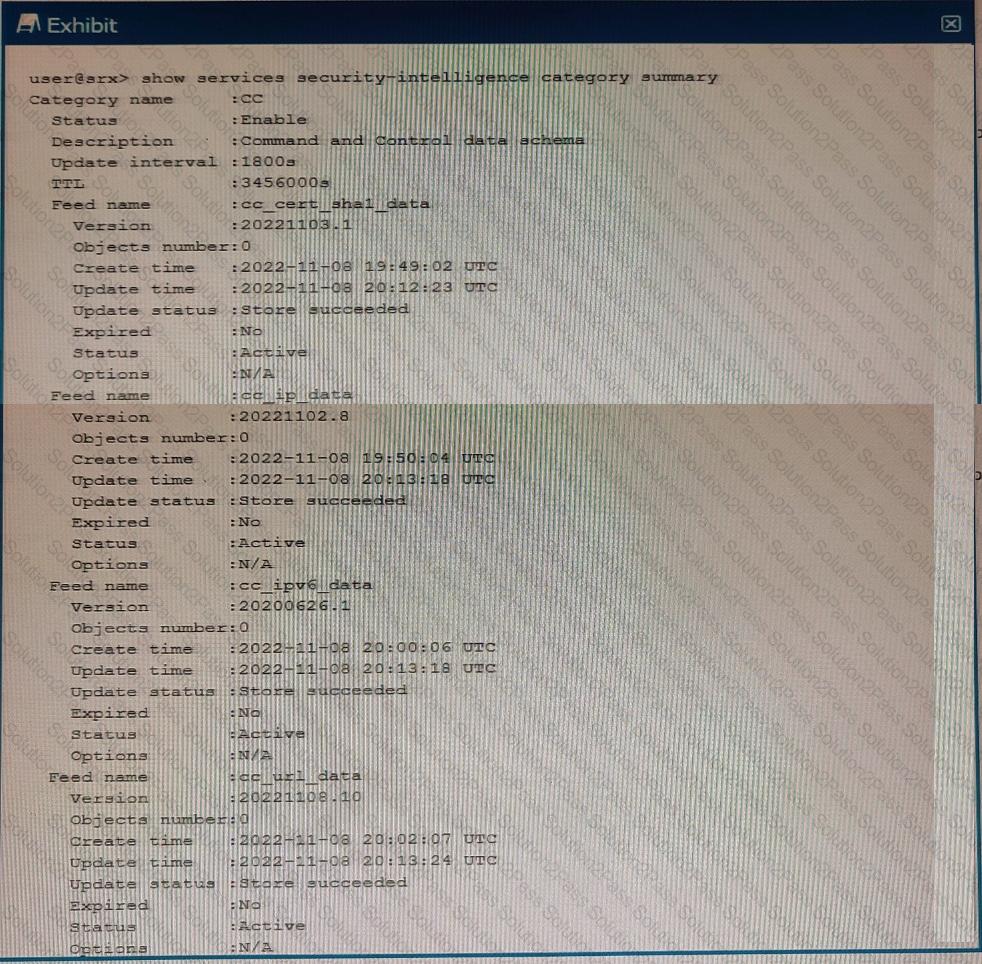
You just finished setting up your command-and-control (C&C) category with Juniper ATP Cloud. You notice that all of the feeds have zero objects in them.
Which statement is correct in this scenario?
Exhibit
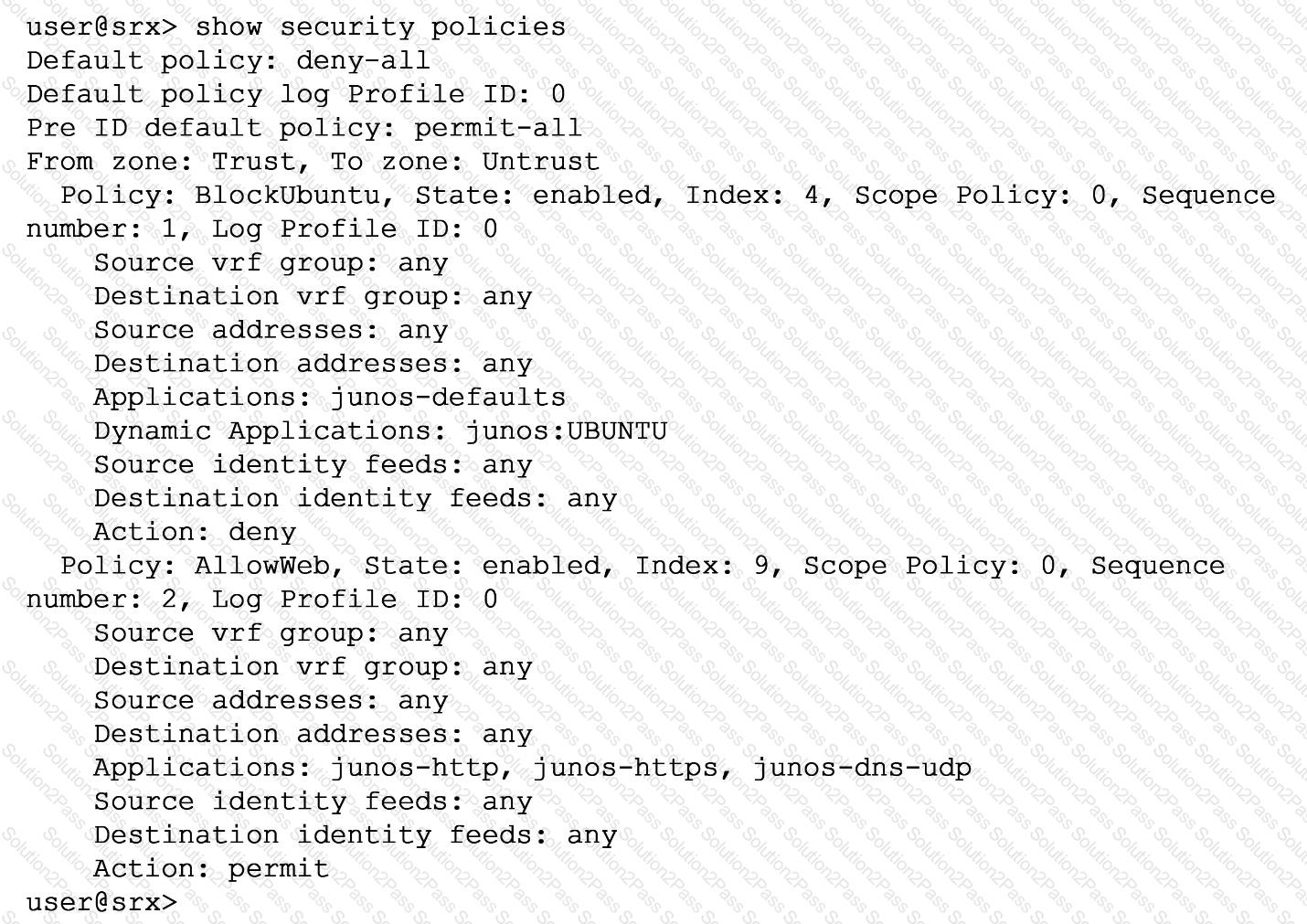
You are asked to ensure that servers running the Ubuntu OS will not be able to update automatically by blocking their access at the SRX firewall. You have configured a unified security policy named Blockuburrtu, but it is not blocking the updates to the OS.
Referring to the exhibit which statement will block the Ubuntu OS updates?
Click the Exhibit button.
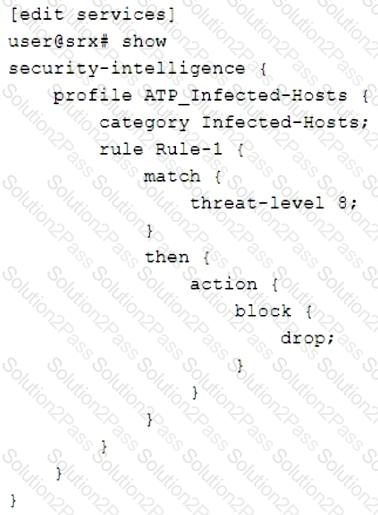
Referring to the exhibit, what will the SRX Series device do in this configuration?
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
What are two benefits of using a vSRX in a software-defined network? (Choose two.)
