JN0-636 Juniper Security, Professional (JNCIP-SEC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-636 Security, Professional (JNCIP-SEC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
You are required to secure a network against malware. You must ensure that in the event that a
compromised host is identified within the network. In this scenario after a threat has been
identified, which two components are responsible for enforcing MAC-level infected host ?
Exhibit:
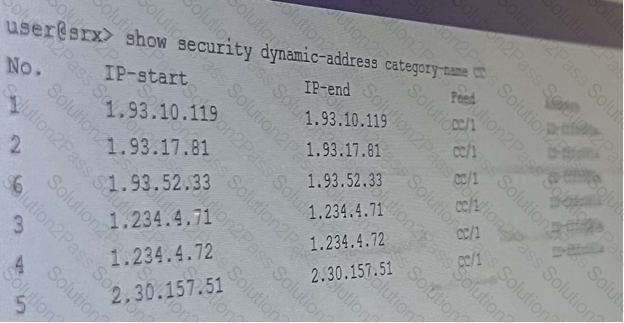
Referring to the exhibit, which two statements are correct?
Exhibit
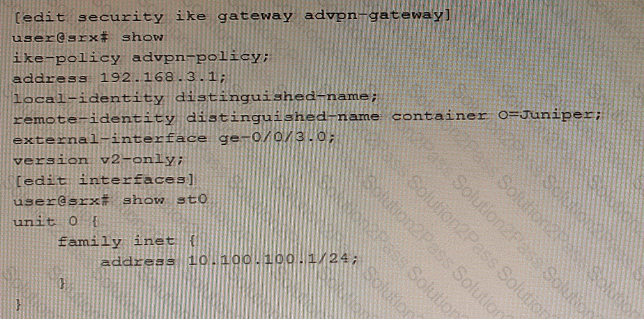
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
A)
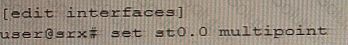
B)
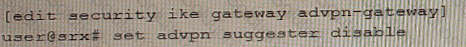
C)

D)

Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
While troubleshooting security policies, you added the count action. Where do you see the result of this action?
Exhibit
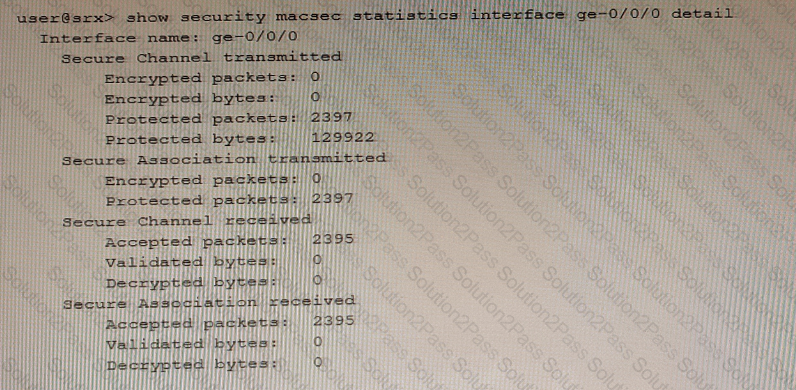
Referring to the exhibit, which two statements are true? (Choose two.)
You must setup a Ddos solution for your ISP. The solution must be agile and not block legitimate traffic.
Which two products will accomplish this task? (Choose two.)
You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices. In this scenario, which port should be opened in the firewall device?
Exhibit
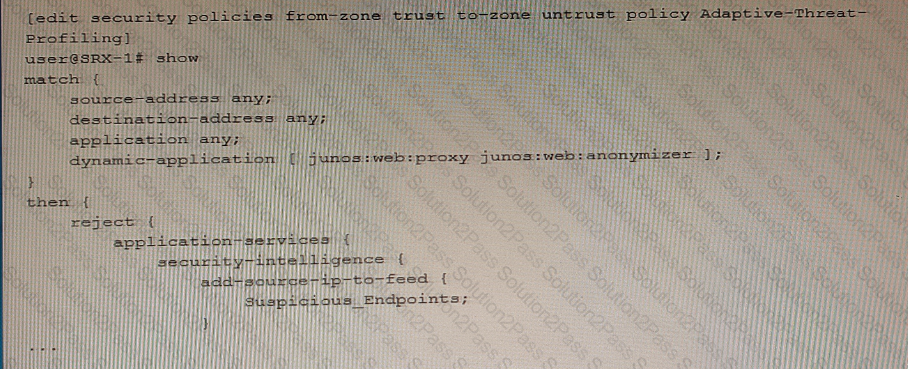
Referring to the exhibit, which two statements are true? (Choose two.)
The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
which security feature bypasses routing or switching lookup?
