JN0-636 Juniper Security, Professional (JNCIP-SEC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-636 Security, Professional (JNCIP-SEC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Exhibit
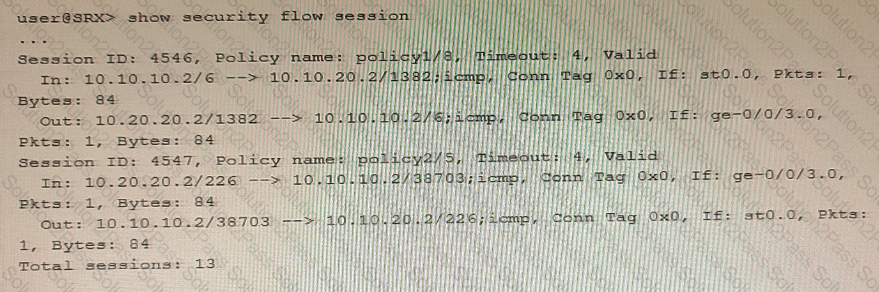
You are validating bidirectional traffic flows through your IPsec tunnel. The 4546 session represents traffic being sourced from the remote end of the IPsec tunnel. The 4547 session represents traffic that is sourced from the local network destined to the remote network.
Which statement is correct regarding the output shown in the exhibit?
Which three type of peer devices are supported for Cos-Based IPsec VPN?
Exhibit
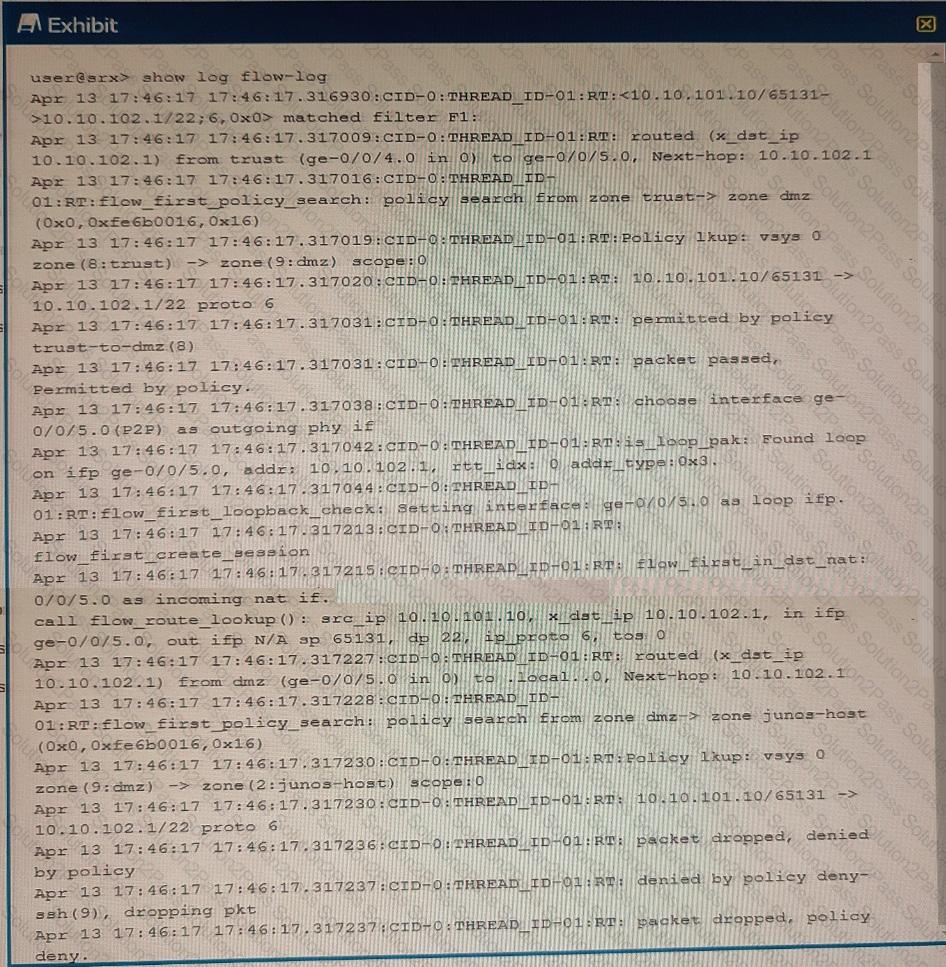
Referring to the exhibit, which three statements are true? (Choose three.)
you configured a security policy permitting traffic from the trust zone to the untrust zone but your
traffic not hitting the policy.
In this scenario, which cli command allows you to troubleshoot traffic problem using the match criteria?
You are asked to look at a configuration that is designed to take all traffic with a specific source ip address and forward the
traffic to a traffic analysis server for further evaluation. The configuration is no longer working as intended.
Referring to the exhibit which change must be made to correct the configuration?
Exhibit
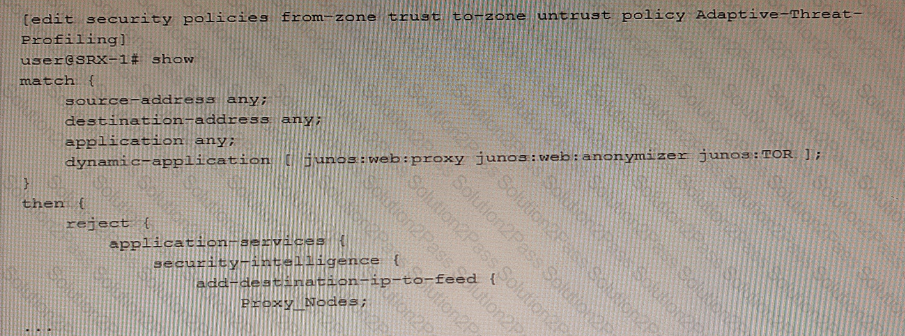
Referring to the exhibit, which two statements are true? (Choose two.)
Click the Exhibit button.
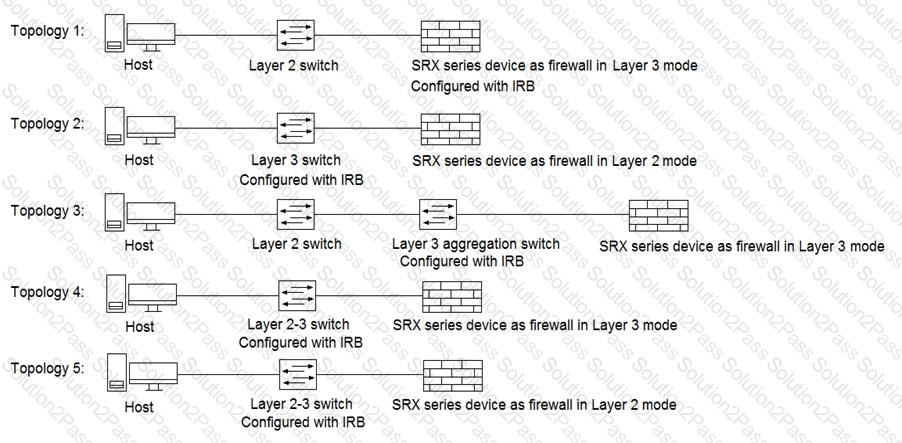
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
Which two log format types are supported by the JATP appliance? (Choose two.)
Exhibit
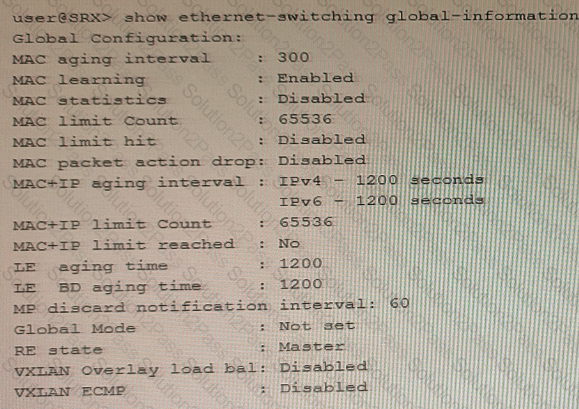
You have configured the SRX Series device to switch packets for multiple directly connected hosts that are within the same broadcast domain However, the traffic between two hosts in the same broadcast domain are not matching any security policies
Referring to the exhibit, what should you do to solve this problem?
You are deploying a virtualization solution with the security devices in your network Each SRX Series device must support at least 100 virtualized instances and each virtualized instance must have its own discrete administrative domain.
In this scenario, which solution would you choose?
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
Exhibit
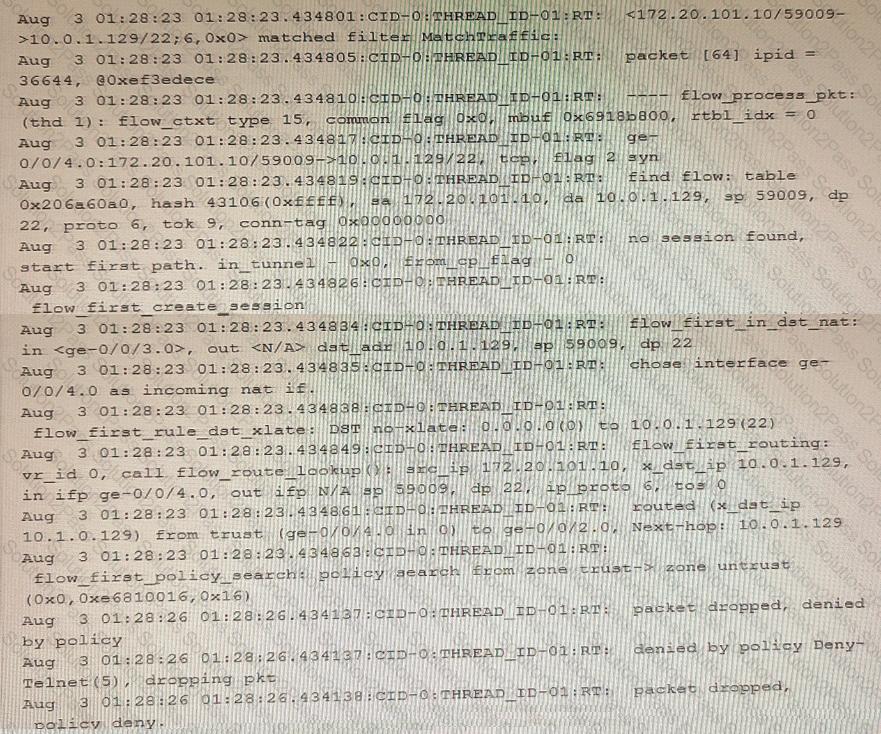
Referring to the exhibit, which statement is true?
Exhibit
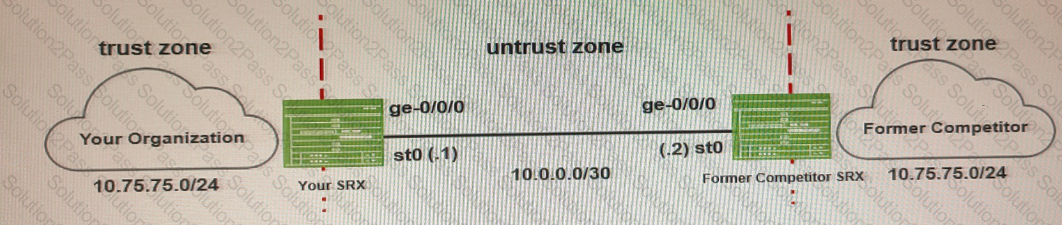
Your company recently acquired a competitor. You want to use using the same IPv4 address space as your company.
Referring to the exhibit, which two actions solve this problem? (Choose two)
You have the NAT rule, shown in the exhibit, applied to allow communication across an IPsec tunnel between your two sites with identical networks. Which statement is correct in this scenario?
Exhibit
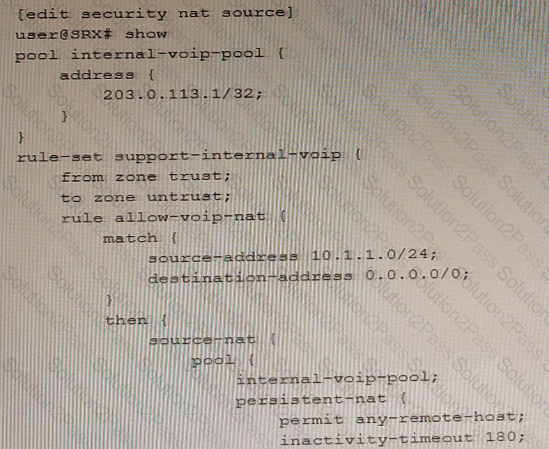
Referring to the exhibit, an internal host is sending traffic to an Internet host using the 203.0.113.1 reflexive address with source port 54311.
Which statement is correct in this situation?
you are connecting two remote sites to your corporate headquarters site. You must ensure that traffic
passes corporate headquarter.
In this scenario, which VPN should be used?
You are asked to deploy filter-based forwarding on your SRX Series device for incoming traffic sourced from the 10.10 100 0/24 network in this scenario, which three statements are correct? (Choose three.)
Exhibit.
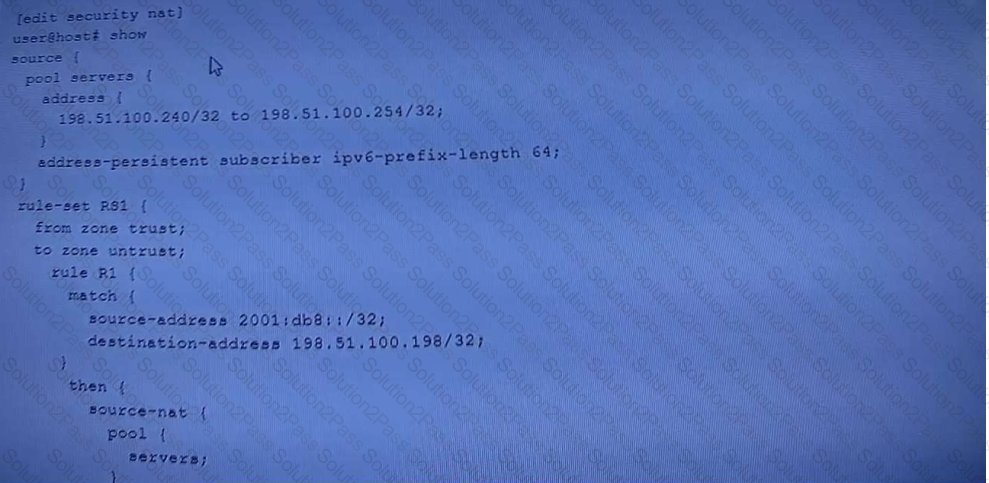
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit.
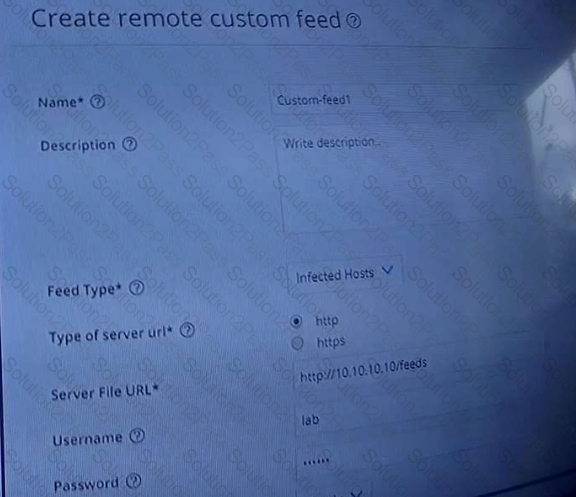
Referring to the exhibit, which two statements are true? (Choose two.)
You are asked to allocate security profile resources to the interconnect logical system for it to work properly.
In this scenario, which statement is correct?
