JN0-637 Juniper Security, Professional (JNCIP-SEC) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Juniper JN0-637 Security, Professional (JNCIP-SEC) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Exhibit:
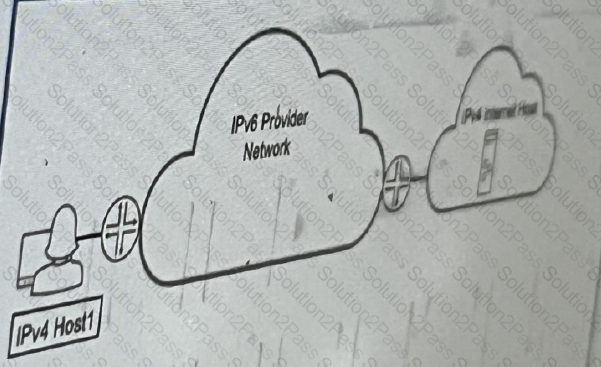
Referring to the exhibit, which technology would you use to provide communication between
IPv4 host1 and ipv4 internal host
Exhibit:
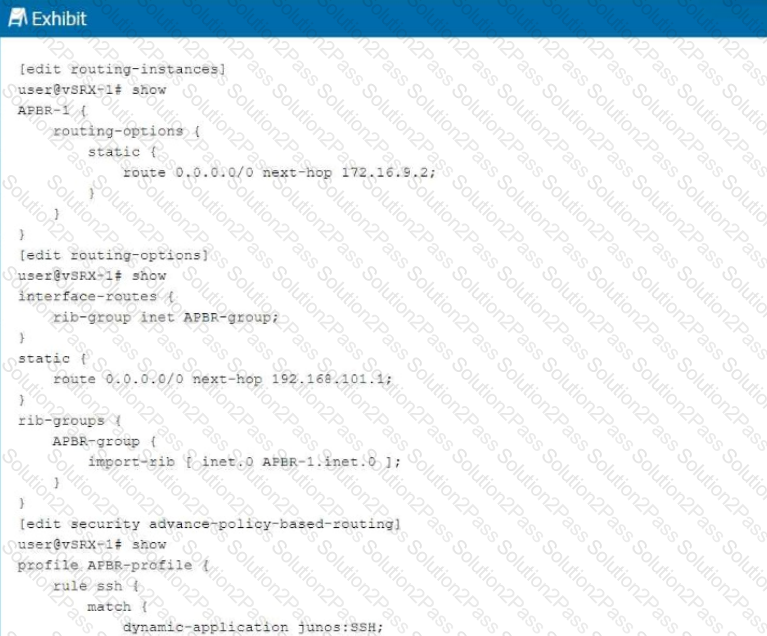
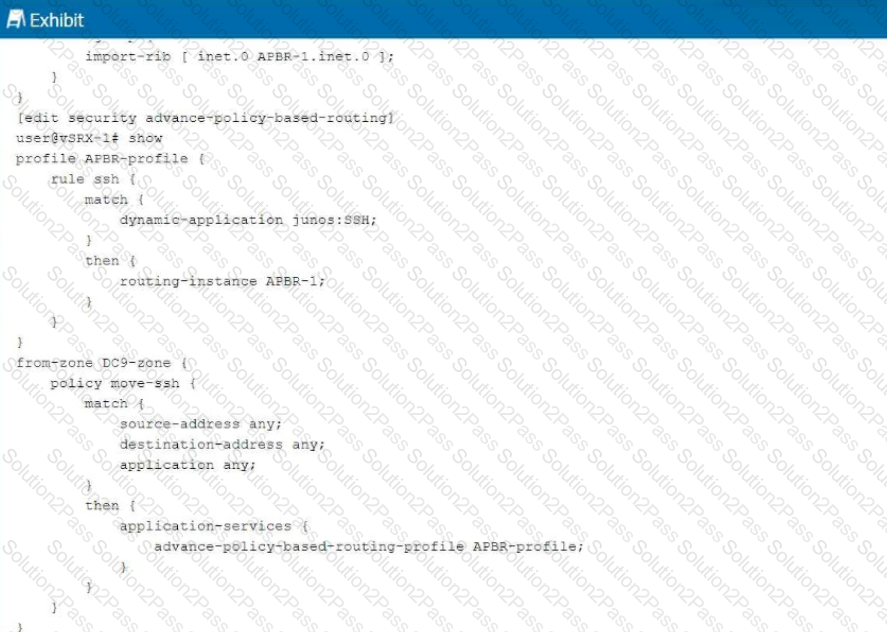
You are having problems configuring advanced policy-based routing.
What should you do to solve the problem?
Click the Exhibit button.
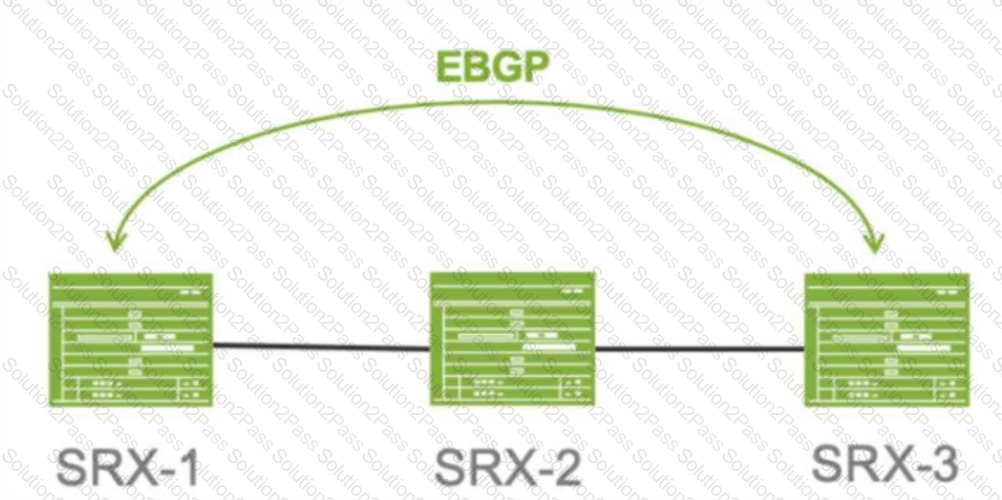
Referring to the exhibit. SRX-1 and SRX-3 have to be connected using EBGP. The BGP configuration on SRX-1 and SRX-3 is verified and correct.
Which configuration on SRX-2 would establish an EBGP connection successfully between SRX-1 and SRX-3?
Which two statements are correct about mixed mode? (Choose two.)
You are asked to configure tenant systems.
Which two statements are true in this scenario? (Choose two.)
You configured two SRX series devices in an active/passive multimode HA setup.
In this scenario, which statement is correct?
Which two statements about the differences between chassis cluster and multinode HA on
SRX series devices are true? (Choose Two)
Which two statements are true when setting up an SRX Series device to operate in mixed mode? (Choose two.)
A company has acquired a new branch office that has the same address space as one of its local networks, 192.168.100.0/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
You have deployed a new site as shown in the exhibit. Hosts in the 10.10.10.0/24 network
must access the DB1 server. The DB1 server must also have internet access the DB1 server encrypted.
Which two configuration statements will be required as part of the configuration on SRX1 to satisfy this requirement? (Choose two)
You want to configure the SRX Series device to map two peer interfaces together and ensure that there is no switching or routing lookup to forward traffic.
Which feature on the SRX Series device is used to accomplish this task?
Which two statements are correct about automated threat mitigation with Security Director? (Choose two.)
What are three core components for enabling advanced policy-based routing? (Choose three.)
Exhibit:
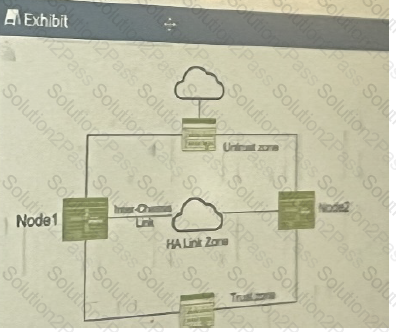
You have deployed a pair of SRX series devices in a multimode HA environment. You need to enable IPsec encryption on the interchassis link.
Referring to the exhibit, which three steps are required to enable ICL encryption? (Choose three.)
Which three statements about persistent NAT are correct? (Choose Three)
Which two statements are true regarding NAT64? (Choose two.)
Which two statements are true about the procedures the Junos security device uses when handling traffic destined for the device itself? (Choose two.)
You Implement persistent NAT to allow any device on the external side of the firewall to
initiate traffic.
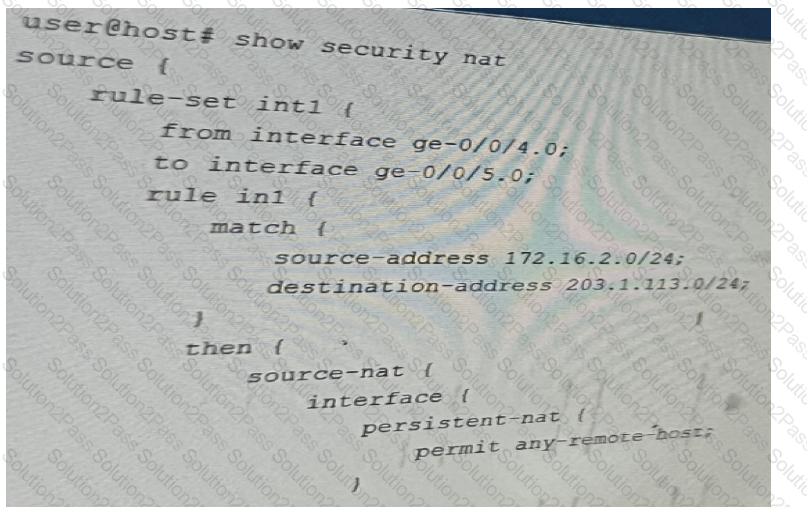
Referring to the exhibit, which statement is correct?
Click the Exhibit button.
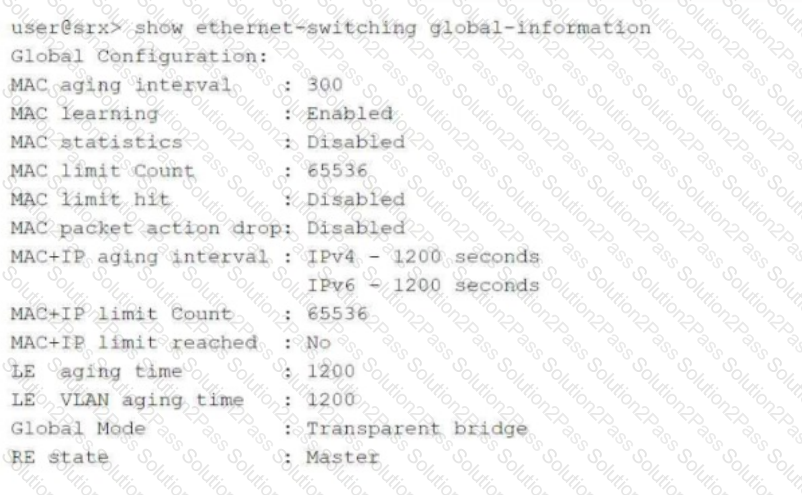
Referring to the exhibit, which two statements are correct? (Choose two.)
You are using trace options to troubleshoot a security policy on your SRX Series device.
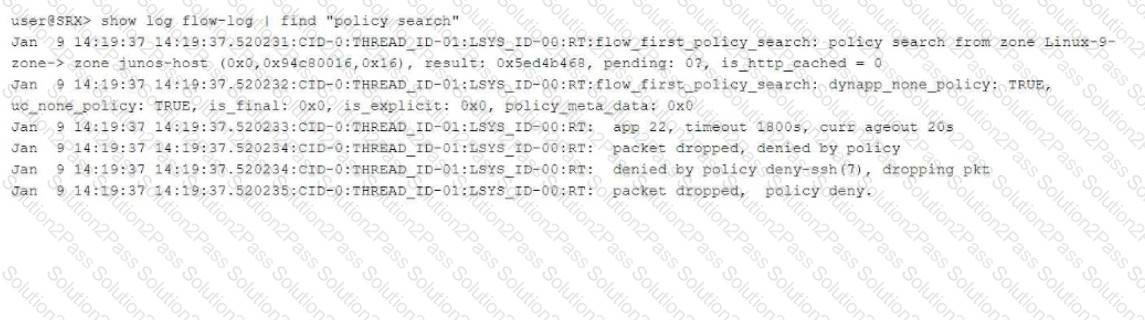
Referring to the exhibit, which two statements are true? (Choose two.)
