SC-900 Microsoft Security Compliance and Identity Fundamentals Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Microsoft SC-900 Microsoft Security Compliance and Identity Fundamentals certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
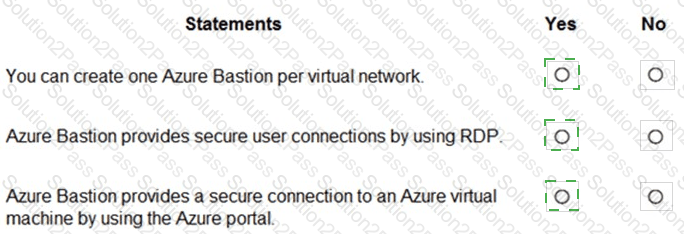
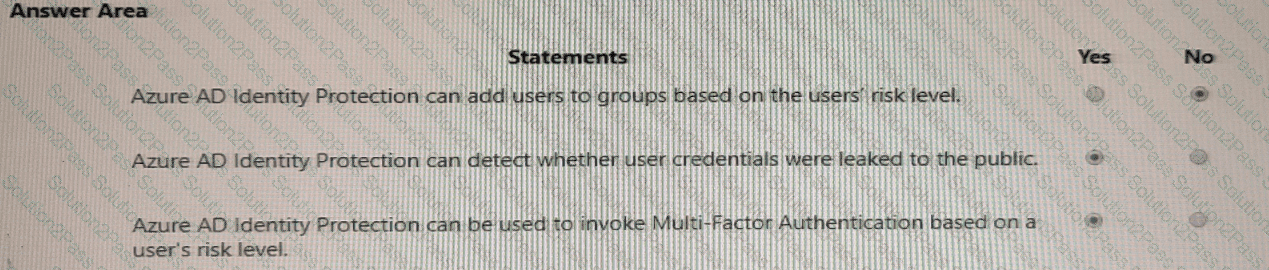
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
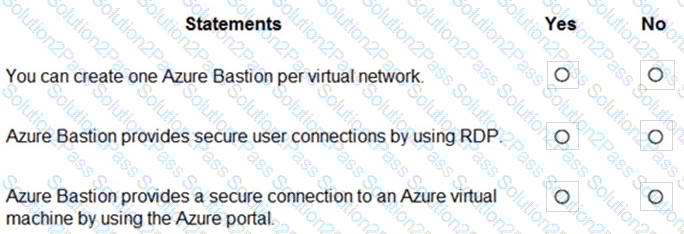
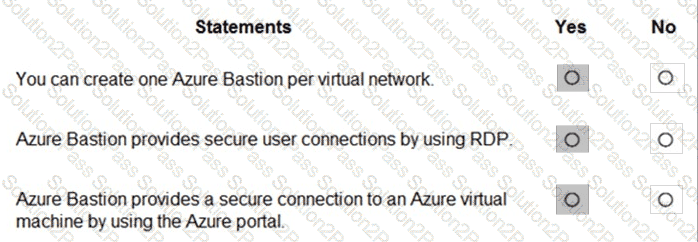
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

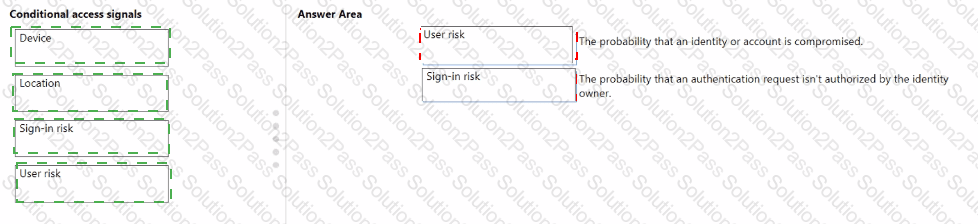
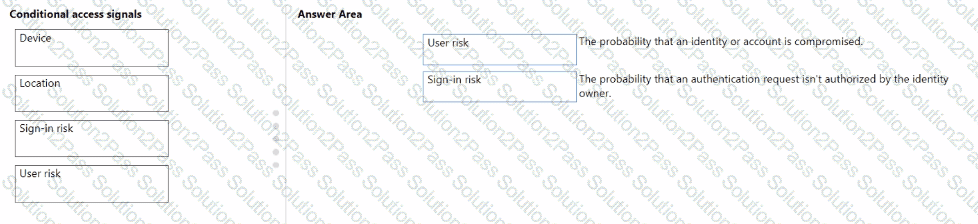
Match the types of Conditional Access signals to the appropriate definitions.
To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

What should you use in the Microsoft 365 security center to view security trends and track the protection status of identities?
Which two types of devices can be managed by using Endpoint data loss prevention (Endpoint DLP)? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.
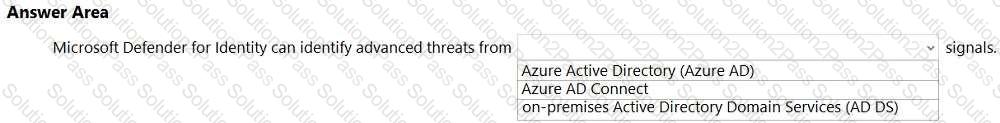
Select the answer that correctly completes the sentence.

What is the purpose of Azure Active Directory (Azure AD) Password Protection?
What Microsoft Purview feature can use machine learning algorithms to detect and automatically protect sensitive items?
You are evaluating the compliance score in Microsoft Purview Compliance Manager.
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
What can you use to protect against malicious links sent in email messages, chat messages, and channels?
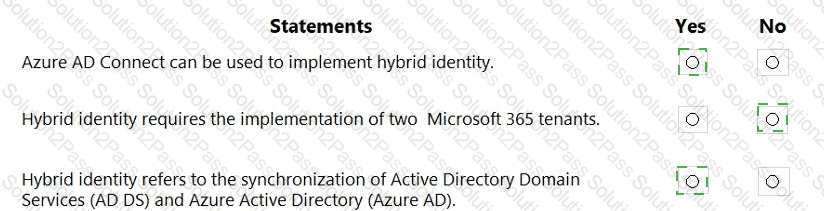
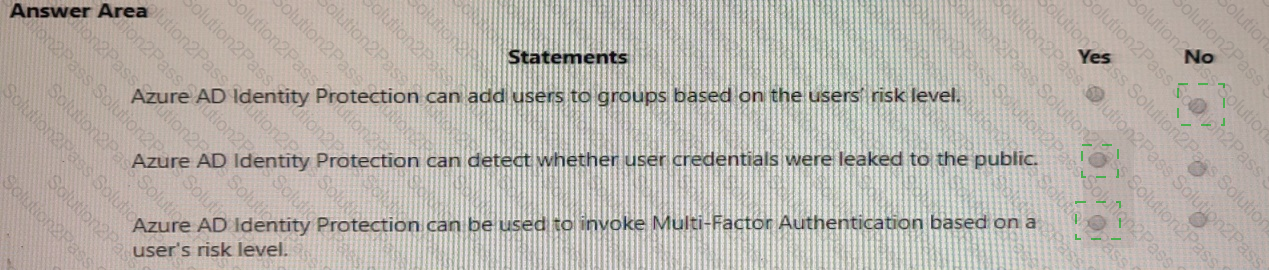
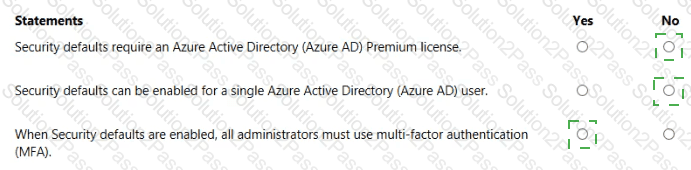
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
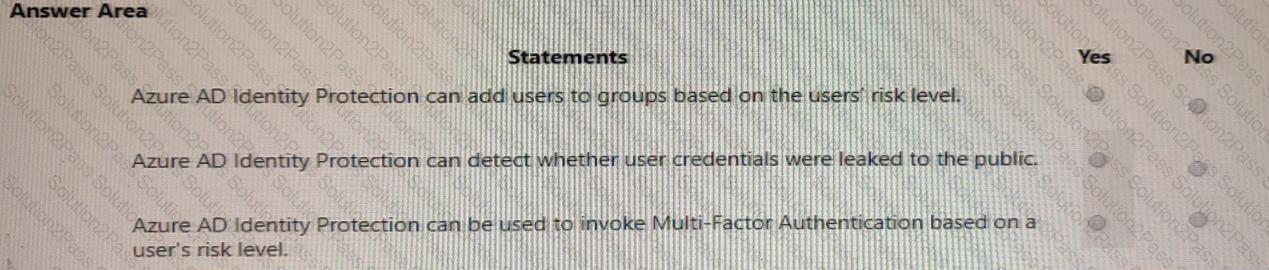
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
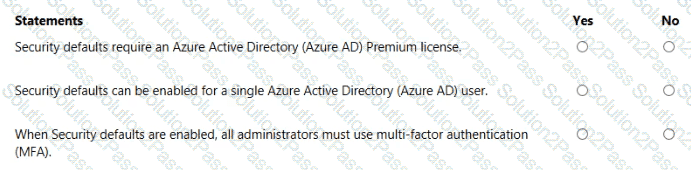
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory (Azure AD)?
Select the answer that correctly completes the sentence.

Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
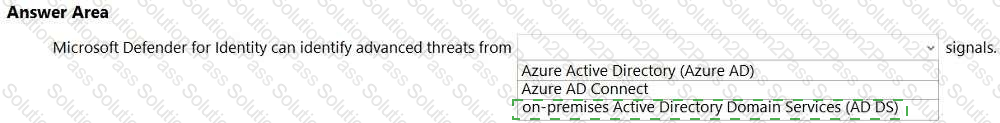
Select the answer that correctly completes the sentence.

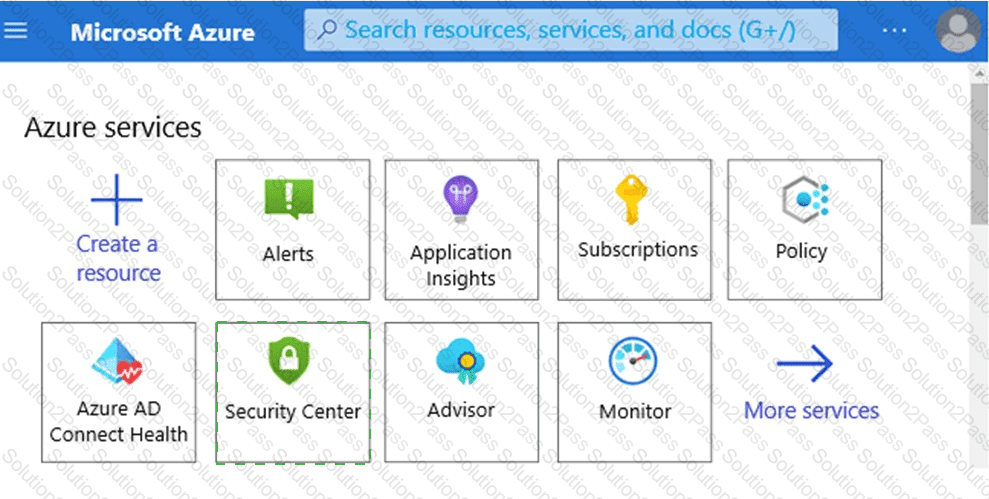
Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area.