NSK200 Netskope Certified Cloud Security Integrator (NCCSI) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Netskope NSK200 Netskope Certified Cloud Security Integrator (NCCSI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Your customer has some managed Windows-based endpoints where they cannot add any clients or agents. For their users to have secure access to their SaaS application, you suggest that the customer use Netskope's Explicit Proxy.
Which two configurations are supported for this use case? (Choose two.)
Your customer has deployed the Netskope client to secure their Web traffic. Recently, they have enabled Cloud Firewall (CFW) to secure all outbound traffic for their endpoints. Through a recent acquisition, they must secure all outbound traffic at several remote offices where they have access to the local security stack (routers and firewalls). They cannot install the Netskope client.
Review the exhibit.
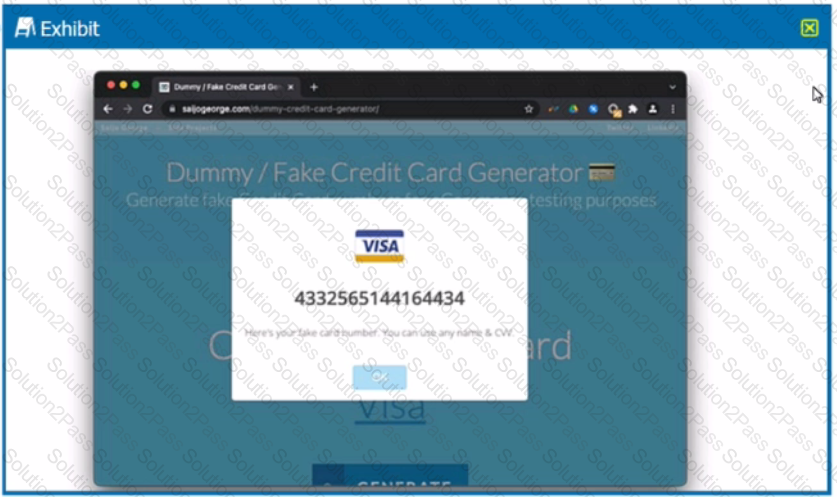
You are asked to create a DLP profile that will ensure that the data shown in the exhibit cannot be uploaded to a user's personal Google Drive.
What must be used to accomplish this task?
Review the exhibit.
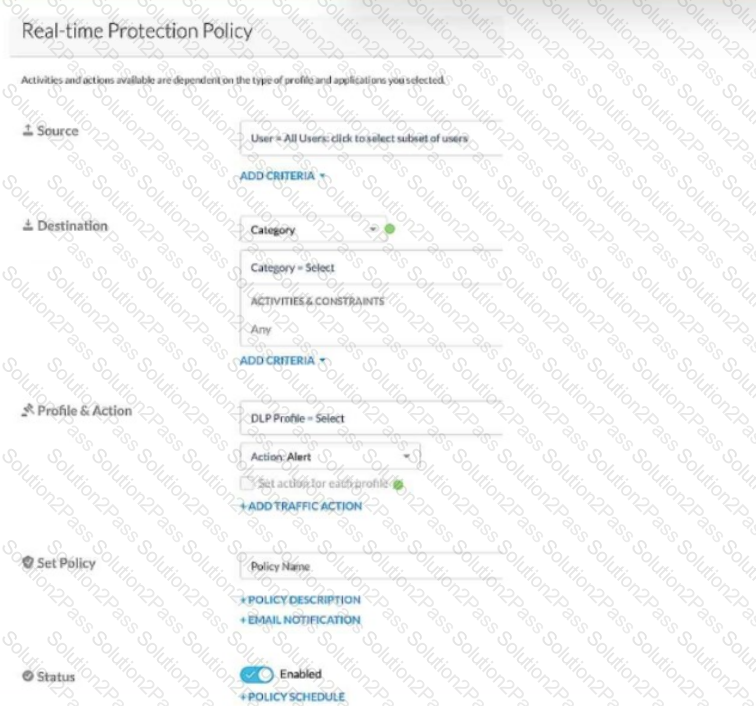
Given the information shown below:
-for PCI data uploads, you want to provide no notification,
-for PHI data uploads, you want to allow users to proceed by clicking OK,
-for GDPR data uploads, you want to provide block notification,
-if none of the above matches, you want to provide no notification.
You want to reduce the number of policies by combining multiple DLP profiles Into one policy.
Referring to the exhibit, which two statements are true? (Choose two.)
The director of IT asks for confirmation If your organization's Web traffic would be blocked when the Netskope client fails. In this situation, what would confirm the fail close status?
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated. In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
Review the exhibit.
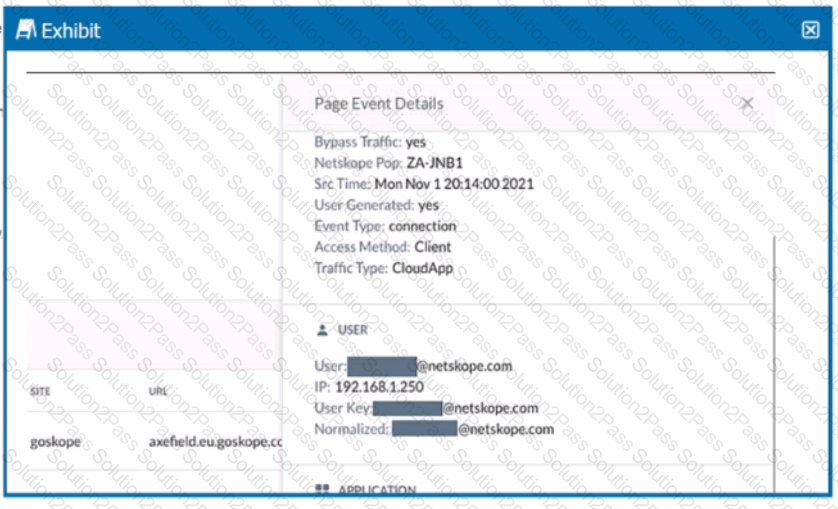
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
