NSK200 Netskope Certified Cloud Security Integrator (NCCSI) Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Netskope NSK200 Netskope Certified Cloud Security Integrator (NCCSI) certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Recently your company implemented Zoom for collaboration purposes and you are attempting to inspect the traffic with Netskope. Your initial attempt reveals that you are not seeing traffic from the Zoom client that is used by all users. You must ensure that this traffic is visible to Netskope.
In this scenario, which two steps must be completed to satisfy this requirement? (Choose two.)
Netskope is being used as a secure Web gateway. Your organization's URL list changes frequently. In this scenario, what makes It possible for a mass update of the URL list in the Netskope platform?
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected. In this scenario, how would you accomplish this task?
A city uses many types of forms, including permit applications. These forms contain personal and financial information of citizens. Remote employees download these forms and work directly with the citizens to complete them. The city wants to be able to identify and monitor the specific forms and block the employees from downloading completed forms.
Which feature would you use to accomplish this task?
While most Web and SaaS traffic is decrypted for inspection, you are asked to prevent a certain host on the network from SSL decryption for privacy purposes.
Review the exhibit.
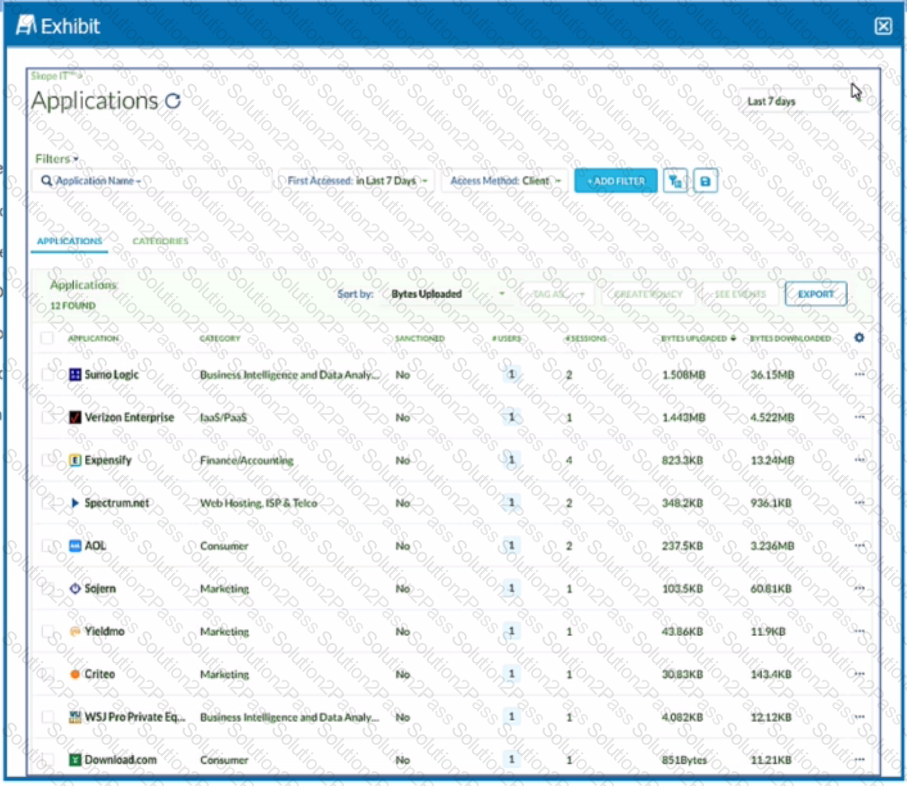
You want to discover new cloud applications in use within an organization.
Referring to the exhibit, which three methods would accomplish this task? (Choose three.)
You want to prevent a document stored in Google Drive from being shared externally with a public link.
Your company wants to know if there has been any unusual user activity. In the UI, you go to Skope IT -> Alerts.
Which two types of alerts would you filter to find this information? (Choose two.)
Review the exhibit.
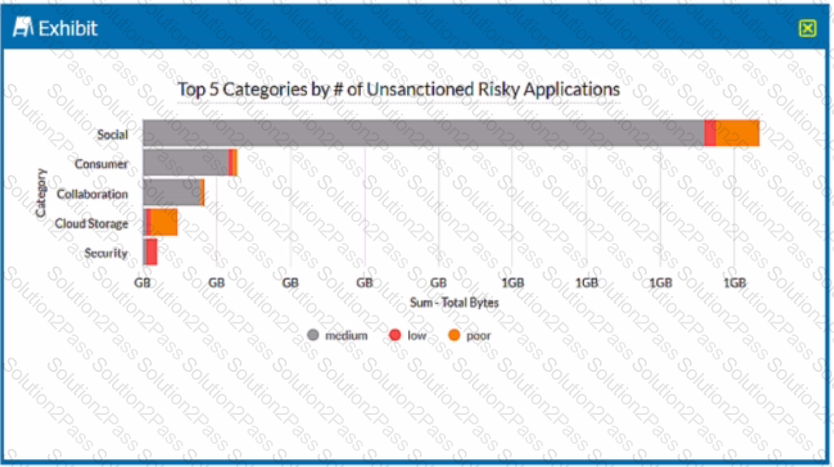
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
You created the Netskope application in your IdP for user provisioning and validated that the API Integration settings are correct and functional. However, you are not able to push the user groups from the IdP into your Netskope tenant.
Review the exhibit.
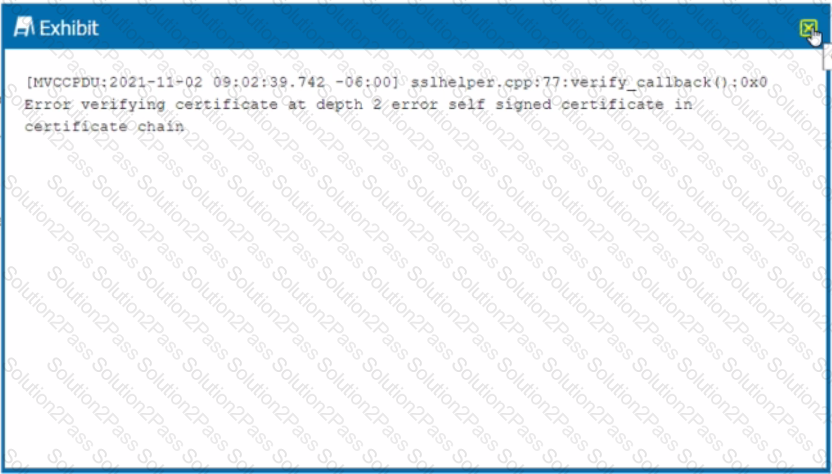
While diagnosing an NPA connectivity issue, you notice an error message in the Netskope client logs.
Referring to the exhibit, what does this error represent?
After deploying the Netskope client to a number of devices, users report that the Client status indicates "Admin Disabled". User and gateway information is displayed correctly in the client configuration dialog
Why are clients installing in an "Admin Disabled" state in this scenario?
Which object would be selected when creating a Malware Detection profile?
Your organization has three main locations with 30.000 hosts in each location. You are planning to deploy Netskope using iPsec tunnels for security.
What are two considerations to make a successful connection in this scenario? (Choose two.)
A customer wants to deploy the Netskope client on all their employee laptops to protect all Web traffic when users are working from home. However, users are required to work from their local offices at least one day per week. Management requests that users returning to the office be able to transparently leverage the local security stack without any user intervention.
Which two statements are correct in this scenario? (Choose two.)
You are troubleshooting an issue with Microsoft where some users complain about an issue accessing OneDrive and SharePoint Online. The configuration has the Netskope client deployed and active for most users, but some Linux machines are routed to Netskope using GRE tunnels. You need to disable inspection for all users to begin troubleshooting the issue.
In this scenario, how would you accomplish this task?
Your customer is concerned about malware in their AWS S3 buckets. What two actions would help with this scenario? (Choose two.)
Your company is using on-premises QRadar as a SIEM solution. They are replacing it with Rapid7 in the cloud. The legacy on-premises QRadar will eventually be decommissioned. Your IT department does not want to use the same token that QRadar uses.
You are having issues with fetching user and group Information periodically from the domain controller and posting that information to your tenant instance in the Netskope cloud. To begin the troubleshooting process, what would you Investigate first in this situation?
Your company wants to deploy Netskope using a tunnel because you have a mixture of device operating systems. You also do not want to enable encryption because you want to maximize bandwidth.
