NCP-MCI-6.5 Nutanix Certified Professional - Multicloud Infrastructure (NCP-MCI) v6.5 exam Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Nutanix NCP-MCI-6.5 Nutanix Certified Professional - Multicloud Infrastructure (NCP-MCI) v6.5 exam certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which two predefined views can be added to a report to identify inefficient VMs?
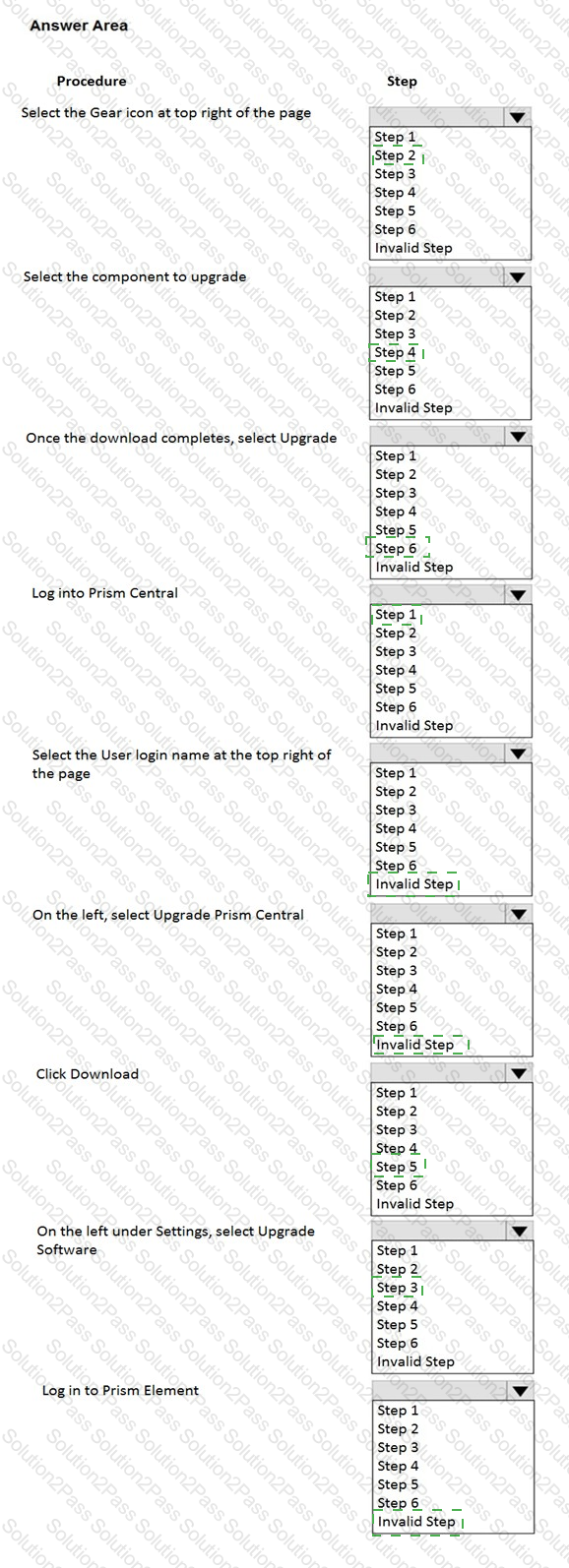
What is the proper sequence to perform a one-click upgrade to a Nutanix cluster?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements. Not all procedures are valid. Identify any invalid procedures using the drop-down option.
An administrator has been alerted to a VM that has high I/O latency and wants to determine if there are any other factors, such as insufficient network or memory resources that correlate, as part of a troubleshooting process.
Which type of chart should the administrator create to allow all relevant data to be easily exported to CSV for later analysis?
Microsegmentation was recently enabled in a Nutanix environment. The administrator wants to leverage Prism Central to create a policy that will block all traffic regardless of direction, between two groups of VMs identified by their category.
Which policy should be used to meet this requirement?
When installing Nutanix Guest Tools (NGT) on an ESXi-hosted VM, which port should be enabled on the VM to allow communication with the NGT-Controller VM service?
An administrator recently added new SSDs to a Nutanix cluster and knows the firmware will be out of date, Due to security constraints, the cluster does not have access to the Internet.
Which two steps must be completed to update the firmware? (Choose two.)
An administrator manages an AHV cluster that is dedicated to a dev/test environment. The administrator receiving complaints from users that they are unable to create new VMs on the cluster.
After the reviewing the cluster, the administrator finds that the memory resources are almost fully utilized, with many VMs over-provisioned on memory.
What option is the most efficient resolution to enable additional VMs to be created?
An administrator notices that most of the VMs in the cluster are on one host. Users report that an application seems to respond slowly. The application server VM has significantly more memory assigned to it than other VMs.
How should the administrator fix this issue?
An administrator has a Custom backup application that requires a 2TB disk and runs m Windows. Throughput is considerably lower than expected.
The application was installed on a VM with the following configuration:
• FOU vCPUs with one core/vCPU
• 4GB of Memory
• One 50GB vDisk for the Windows installation
• One 2TB vDisk for the application
What is the recommended configuration change to improve throughput?
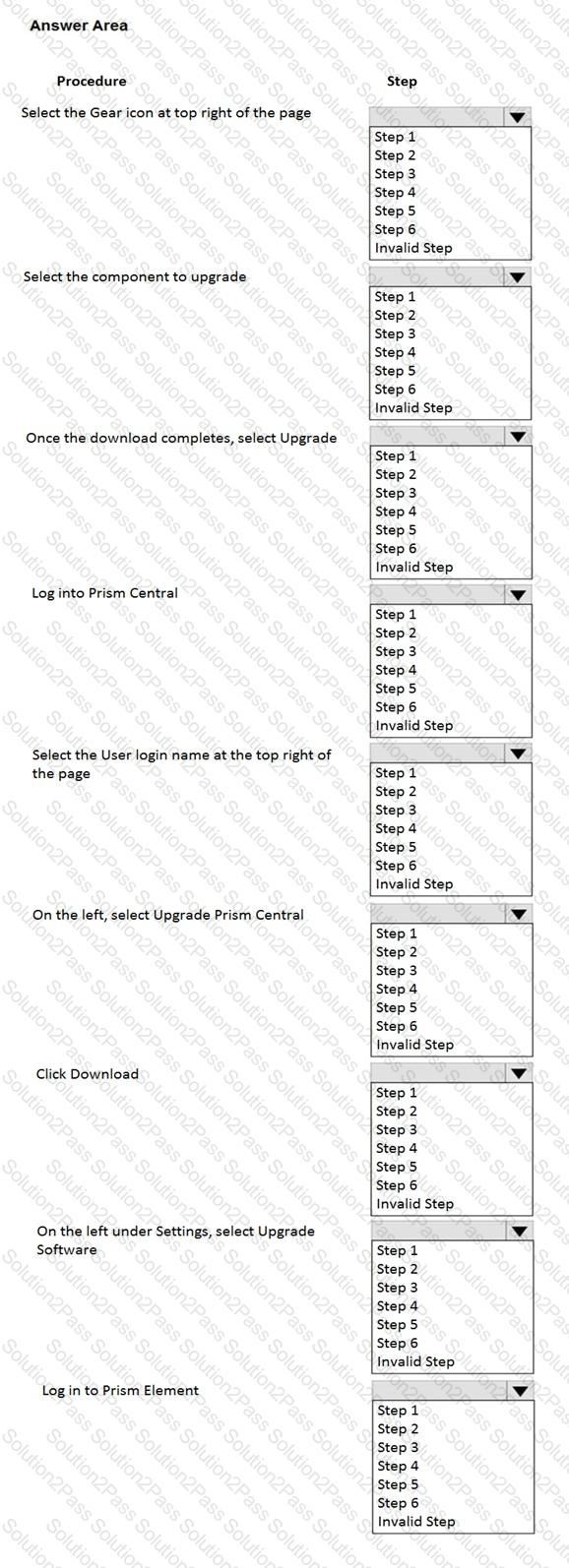
An administrator is reviewing performance of a core banking system that routinely has 20,000 concurrent users. During, business hours, the CPU on the applications servers runs at close to 100%. The administrator needs to determine if there is a performance issue specific to the app servers, the database servers, or all servers on the cluster.
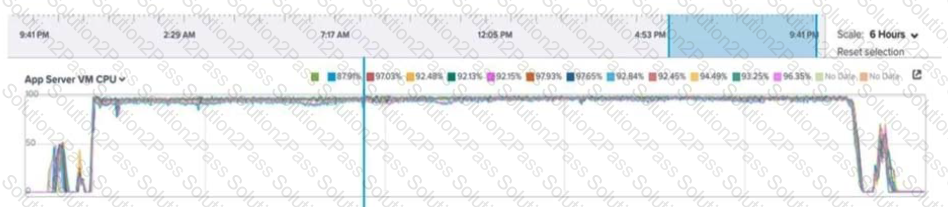
Which metrics should the administrator review in Prism Analysis Graphs?
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
During an AHV upgrade, an administrator finds that a critical VM was powered off rather than migration to another host.
Which scenario explains this behavior?
Which storage policy value can be inherited from a cluster?
A user running a Computer Aided Design (CAD) application is complaining about slow response time within the VM, particular when moving windows or rendering images.
Which VM metric will guide the administrator toward diagnosing the problem?
Where are Leap Availability Zones configured?
Refer to Exhibit:
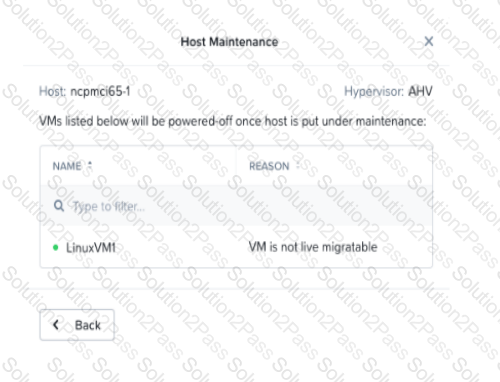
An administrator is trying to put a node into maintenance mode but receives the message shown in the exhibit.
What is a potential reason for this dialog?
An administrator wants to have a VM on an AHV cluster with access to multiple VLANs. What is the most efficient way to achieve this?
An administrator is performing validation testing of a new-deploy cluster. During this test, the administrator disconnect each LAN interface from each of the nodes while pinging the hypervisor and guest VMs.
When the first interface is disconnected, pings continue as expected to the hypervisor, but pings stop responding from the guest. Pings continue when the interface is reconnected. When the second interface is disconnected, pings continue to both the hypervisor and guest VMs.
What could be the cause of this error?
What is the name of the internal bridge used by AHV nodes and CVMs?
An administrator is preparing to deploy a new application on an AHV cluster, Security requirements dictate that all virtual servers supporting this application must be prevented from communicating with unauthorized hosts.
Which option would achieve this goal?