CloudSec-Pro Paloalto Networks Palo Alto Networks Cloud Security Professional Free Practice Exam Questions (2026 Updated)
Prepare effectively for your Paloalto Networks CloudSec-Pro Palo Alto Networks Cloud Security Professional certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2026, ensuring you have the most current resources to build confidence and succeed on your first attempt.
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying.
How should the customer automate vulnerability scanning for images deployed to Fargate?
A customer wants to be notified about port scanning network activities in their environment. Which policy type detects this behavior?
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
Prisma Cloud supports sending audit event records to which three targets? (Choose three.)
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User: $ADMIN_USER
Which command generates the YAML file for Defender install?
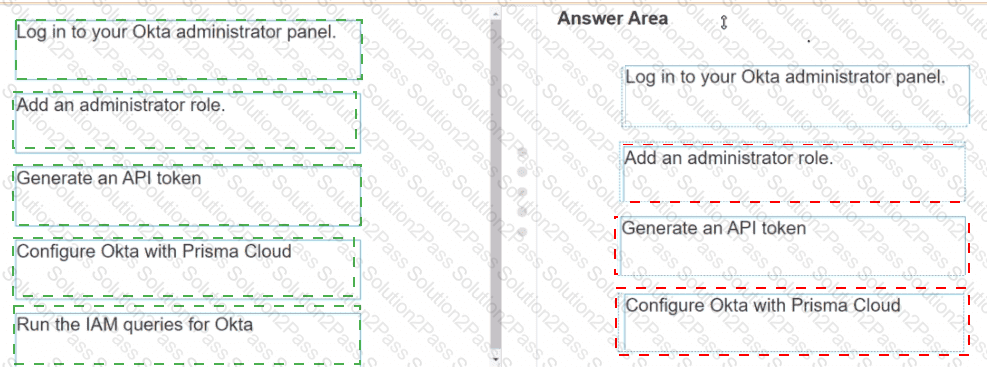
Put the steps of integrating Okta with Prisma Cloud in the right order in relation to CIEM or SSO okra integration.

The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
Under which tactic is “Exploit Public-Facing Application” categorized in the ATT&CK framework?
Which two bot types are part of Web Application and API Security (WAAS) bot protection? (Choose two.)
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
Which options show the steps required to upgrade Console when using projects?
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
Which three types of buckets exposure are available in the Data Security module? (Choose three.)
Which step is included when configuring Kubernetes to use Prisma Cloud Compute as an admission controller?
Given the following information, which twistcli command should be run if an administrator were to exec into a running container and scan it from within using an access token for authentication?
• Console is located at https://prisma-console.mydomain.local
• Token is: TOKEN_VALUE
• Report ID is: REPORTJD
• Container image running is: myimage:latest
Which “kind” of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?