CSQA Software Certifications CSQA Certified Software Quality Analyst Free Practice Exam Questions (2025 Updated)
Prepare effectively for your Software Certifications CSQA CSQA Certified Software Quality Analyst certification with our extensive collection of free, high-quality practice questions. Each question is designed to mirror the actual exam format and objectives, complete with comprehensive answers and detailed explanations. Our materials are regularly updated for 2025, ensuring you have the most current resources to build confidence and succeed on your first attempt.
Which management tool would you use if your QA team needed to prioritize issues?
Risk has two attributes. One is magnitude and the other is:
There are five levels of ISO Process Capability.
During the management cycle, which activity MUST be integrated with other activities because it is a continuous activity?
Which of the following is considered a subjective measure?
-- Exhibit –
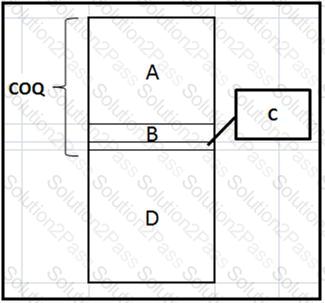
-- Exhibit --
In the Cost of Quality diagram shown, the COQ cost labeled "A" represents:
Prior to TQM, the distinction between “little-Q” and “big-Q” was given by:
In the new quality management philosophy, the emphasis must be on:
Which of the following is not a process within Level 4 for maturing Quality Assurance Processes?
Checking if a date field on a screen gives an error on entering February 29 is an example of:
Which of the following is NOT one of the five types of listening?
Procedures describe how methods, _________, techniques, and people are applied to perform a process?
The guarantee provided by the contractor of software development that the deliverables will meet the specification is called:
-- Exhibit –
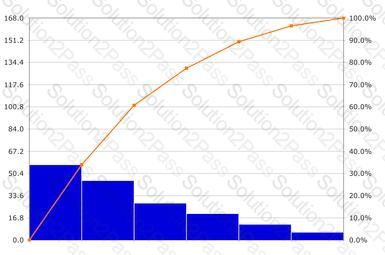
-- Exhibit --
The diagram is called a:
What type of testing evaluates the completeness of the documentation associated with a software application?
Continuing process improvement techniques should be applied to which of the following IT work processes?
Which of the following management philosophies would be associated with a quality management philosophy as opposed to the traditional management philosophy?
The check sheet is used to record data gathered over a period of time to determine frequency of an event.
Which layer of management is the weakest link in a successful quality management program?
The risk associated with replacing a team member would be characterized as:
Event identification, control activities, and risk response are included in which of the following internal control models?
-- Exhibit –
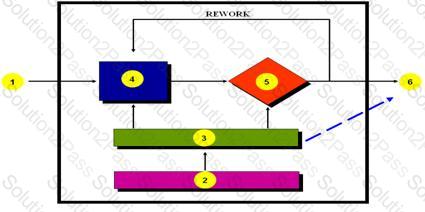
-- Exhibit --
In the diagram of the tester's work bench, the box labeled (2) is the:
There is a strong correlation between process maturity and defect rates. As the process maturity level increases, the defect rate decreases.
-- Exhibit –
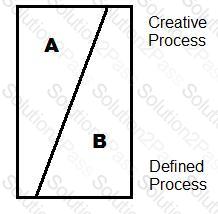
-- Exhibit --
In the diagram, the sections of the diagram labeled "A" and "B" represent larger portions of "DO" and "CHECK". Note that the top of the diagram represents a more creative process and lower portion a more defined process.
Which party(s) is responsible to ensure protection of intellectual property rights included within a contract for software development?
Staff job satisfaction increases significantly as processes mature.
The purpose of a security awareness program is to achieve all of the following objectives, EXCEPT:
For contracted software, detailing the obligations of both contractual parties within the contract addresses:
Requirements reviews, code walkthroughs, and inspections are examples of:
After establishing the team for conducting security baseline, the first step should be to:
